In Windows 7 and Windows Vista, if a program does not have elevated permissions to write to C:\Program Files or C:\Windows folder, Windows lets the program think it is writing there. However, it redirects the action to a Virtual Store under the AppData store in your User folder. Usually, INI files, data files, templates are redirected in such a manner. In this post, I will explain about File Virtualization and Compatibility Files toolbar button in Windows 7.
File Virtualization in Windows 7
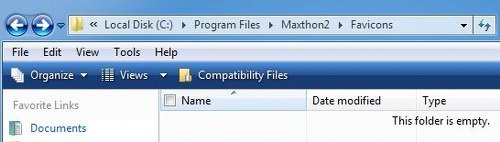
To take an example, I use the Maxthon browser. Its favicons are meant to be stored in the following location:
C:\Program Files\Maxthon2\Favicons
However, they get stored in the following folder:
C:\Users\Username\AppData\Local\VirtualStore\Program Files\Maxthon2\Favicons
Compatibility Files toolbar button
So if you open the first folder, you will see it as empty. But if you click on the Compatibility Files tab, immediately the latter folder is opened, and you see all the favicons there.
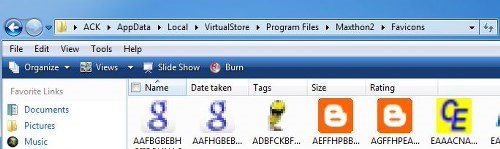
It is called File Virtualization.
It is one of the security features that are not evident in Windows. The feature provides an application, a virtual store where it can read and write without compromising the system. For instance, if you have an app that tries to write to System32, then, Windows creates a virtual System32 in the user’s profile that the application can use.
Internet Explorer running in Protected Mode makes use of this functionality. It places a file in the virtual startup folder when you visit a web page rather than the actual Startup folder so that it does not execute upon the next boot.
It makes it possible to run applications as a standard user, even when the applications require Administrator rights. In short, Windows redirects, such application writes from specified secured areas to the virtual store under the user’s profile. It is something similar to Registry Virtualization.