Ransomware recently struck some unsecured MongoDB installations and held the data to ransom. Here we will see what is MongoDB and take a look at some steps you can take to secure and protect MongoDB database. To begin with, here is a brief introduction about MongoDB.
What is MongoDB
MongoDB is an open source database that stores data using a flexible document data model. MongoDB differs from traditional databases which are built using tables and rows, whereas, MongoDB uses an architecture of collections and documents.
Following a dynamic schema design, MongoDB allows the documents in a collection to have different fields and structures. The database uses a document storage and data interchange format called BSON, which provides a binary representation of JSON-like documents. This makes data integration for certain types of applications faster and easier.
Ransomware attacks MongoDB data
Recently, Victor Gevers, a security researcher tweeted that there was a string of Ransomware attacks on poorly secured MongoDB installations. The attacks started last December around Christmas 2016 and have since then infected thousands of MongoDB servers.
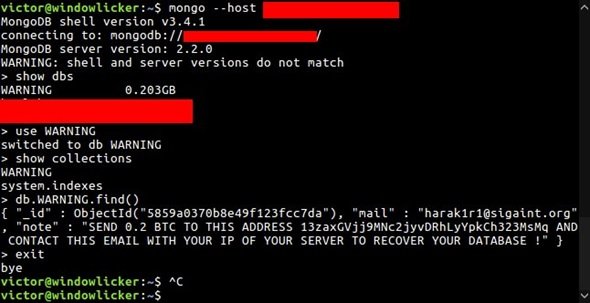
Initially, Victor discovered 200 MongoDB installations which were attacked and held for ransom. However, soon the infected installations soared to 2000 DBs as reported by another security researcher, Shodan Founder John Matherly, and by the end of the 1st week of 2017, the number of the compromised systems were more than 27,000.
Ransom demanded
Initial reports suggested, that attackers were demanding 0.2 Bitcoins (Approx US$184) as ransom which was paid by 22 victims. Currently, the attackers have increased the ransom amount and are now demanding 1 Bitcoin (Approx 906 USD).
Since the disclosure, the security researchers have identified more than 15 hackers involved in hijacking MongoDB servers. Among them, an attacker using email handle kraken0 has compromised more than 15,482 MongoDB servers and is demanding 1 Bitcoin to return the lost data.
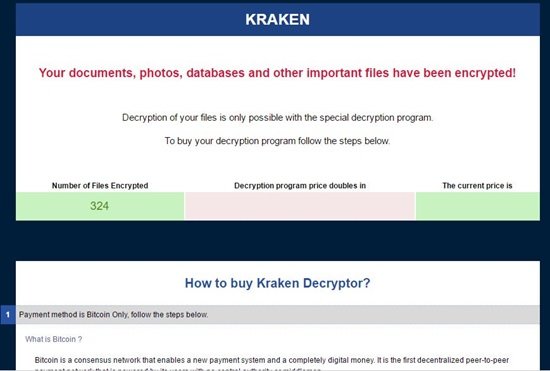
Until now, hijacked MongoDB servers has grown over 28,000 as more hackers are also doing the same — accessing, copying and deleting badly-configured databases for Ransom. Moreover, Kraken, a group that has been previously involved in the distribution of Windows Ransomware, has joined in too.
How does the MongoDB Ransomware sneak in
MongoDB servers which are accessible via the internet without a password have been the ones who are targeted by the hackers. Hence, Server Administrators who chose to run their servers without a password and employed default usernames were easily spotted by the hackers.
What’s worse, there are instances of the same server being re-hacked by different hacker groups who have been replacing existing ransom notes with their own, making it impossible for victims to know if they’re even paying the right criminal, let alone whether their data can be recovered. Therefore, there is no certainty if any of the stolen data will be returned. Hence, even if you paid the ransom, your data may still be gone.
MongoDB security
It’s a must that Server Administrators must assign a strong password and username for accessing the database. Companies using the default installation of MongoDB are also advised to update their software, set up authentication and lock down port 27017 which has been targeted the most by the hackers.
Steps to protect your MongoDB data
- Enforce Access Control and Authentication
Start by Enabling access control of your server and specify the authentication mechanism. Authentication requires that all users provide valid credentials before they can connect to the server.
The latest MongoDB 3.4 release enables you to configure authentication to an unprotected system without incurring downtime.
- Setup Role-Based Access Control
Rather than providing full access to a set of users, create roles that define the exact access a set of users’ needs. Follow a principle of least privilege. Then create users and assign them only the roles they need to perform their operations.
- Encrypt Communication
Encrypted data is difficult to interpret, and not many hackers are able to decrypt it successfully. Configure MongoDB to use TLS/SSL for all incoming and outgoing connections. Use TLS/SSL to encrypt communication between mongod and mongos components of a MongoDB client as well as between all applications and MongoDB.
Using MongoDB Enterprise 3.2, the WiredTiger storage engine’s native Encryption at Rest can be configured to encrypt data in the storage layer. If you are not using WiredTiger’s encryption at rest, MongoDB data should be encrypted on each host using file-system, device, or physical encryption.
- Limit Network Exposure
To Limit Network exposure ensure that MongoDB runs in a trusted network environment. Admins should allow only trusted clients to access the network interfaces and ports on which MongoDB instances are available.
- Backup your data
MongoDB Cloud Manager and MongoDB Ops Manager provide continuous backup with point in time recovery, and users can enable alerts in Cloud Manager to detect if their deployment is internet exposed
- Audit System Activity
Auditing systems periodically will ensure that you are aware of any irregular changes to your database. Track access to database configurations and data. MongoDB Enterprise includes a system auditing facility that can record system events on a MongoDB instance.
- Run MongoDB with a Dedicated User
Run MongoDB processes with a dedicated operating system user account. Ensure that the account has permissions to access data but no unnecessary permissions.
- Run MongoDB with Secure Configuration Options
MongoDB supports the execution of JavaScript code for certain server-side operations: mapReduce, group, and $where. If you do not use these operations, disable server-side scripting by using the –noscripting option on the command line.
Use only the MongoDB wire protocol on production deployments. Keep input validation enabled. MongoDB enables input validation by default through the wireObjectCheck setting. This ensures that all documents stored by the mongod instance are valid BSON.
- Request a Security Technical Implementation Guide (where applicable)
The Security Technical Implementation Guide (STIG) contains security guidelines for deployments within the United States Department of Defense. MongoDB Inc. provides its STIG, upon request, for situations where it is required. You can request a copy for more information.
- Consider Security Standards Compliance
For applications requiring HIPAA or PCI-DSS compliance, please refer to the MongoDB Security Reference Architecture here to learn more about how you can use the key security capabilities to build compliant application infrastructure.
How to find out if your MongoDB installation is hacked
- Verify your databases and collections. The hackers usually drop databases and collections and replace them with a new one while demanding a ransom for the original
- If access control is enabled, audit the system logs to find out for unauthorized access attempts or suspicious activity. Look for commands that dropped your data, modified users, or created the ransom demand record.
Do note that there is no guarantee that your data will be returned even after you have paid the ransom. Hence, post attack, your first priority should be securing your cluster(s) to prevent further unauthorized access.
How do I protect my MongoDB database?
There are several things you can do to protect your MongoDB database, and some of the tips and tricks are mentioned in this article. For example, you can enforce the access control and authentication, configure role-based access control, encrypt your communications, set a limit for network exposure, etc. Apart from these, it is recommended to backup your data continuously so that you can always be on the safe side.
Is MongoDB a secure database?
Yes, MongoDB is a secure database that you can use for almost any purpose. It is a great alternative to Apache, DynamoDB, Redis, etc. Talking about security, you can use it to get things done for your projects. It takes several security measures to make things secure and safe for the users.
If you take backups, then at the time you restore the most recent version, you can evaluate what data may have changed since the most recent backup and the time of the attack. For more, you may visit mongodb.com.