In this article, we will discuss possible fixes to resolve the AADSTS50020, User account from identity provider does not exist in tenant error. This error usually occurs when a guest user from an identity provider (IdP) can’t sign in to a resource tenant in Azure Active Directory (Azure AD). You may see this error in different situations. Each situation requires a different way to troubleshoot.
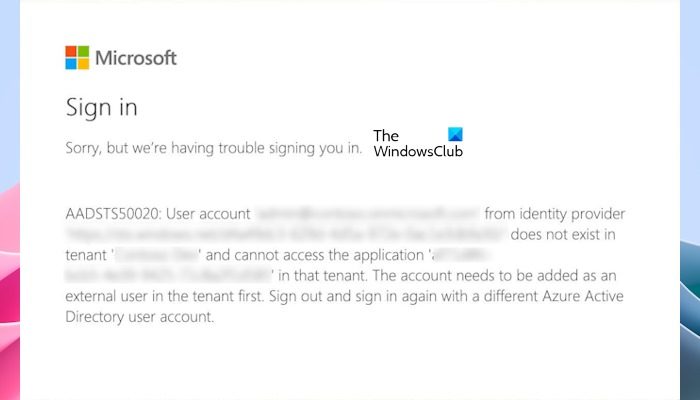
The complete error message that the guest user sees when trying to access an application or resource in the resource tenant is:
AADSTS50020: User account ‘[email protected]’ from identity provider {IdentityProviderURL} does not exist in tenant {ResourceTenantName}.
On reviewing the logs on the home tenant, the administrator will see the following error message:
User account {email} from identity provider {idp} does not exist in tenant {tenant} and cannot access the application {appId}({appName}) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account.
AADSTS50020, User account from identity provider does not exist in tenant
The solutions below will help you fix the AADSTS50020, User account from identity provider does not exist in tenant error.
- Change the sign-in audience setting in the app registration manifest
- Use the correct sign-in URL
- Sign out, then sign in again from a different browser or a private browser session
- Invite the guest user
- Assign access to users (if applicable)
- Use an endpoint that’s specific to the tenant or organization
- Reset the redemption status of the guest user account
Let’s see all these fixes in detail.
1] Change the sign-in audience setting in the app registration manifest
One possible cause of this error is when a tenant uses an unsupported account type. For example, If a single-tenant account type is set for your app registration, a user from another identified provider can’t sign in to the application.
To fix the AADSTS50020 error, change the sign-in audience setting in the app registration manifest as follows:
- Go to the Azure portal.
- Select App registrations.
- Select the name of your app registration.
- Select Manifest, from the Sidebar.
- In the JSON code, find the signInAudience setting.
- Check the setting from one of the following values:
-
- AzureADandPersonalMicrosoftAccount
- AzureADMultipleOrgs
- PersonalMicrosoftAccount
The SignInAudience should contain one of the above-mentioned values. If you do not find any of these values in the SignInAudience setting, you have to create the app registration again.
2] Use the correct sign-in URL
Another cause of this error is using the incorrect sign-in URL. For example, if you use https://login.Microsoftonline.com/<YourTenantNameOrID> URL, the authentication is expected to be run on your tenant only. That’s why users in other organizations cannot access the application. When other users try to do so, they will receive a sign-in error.
To resolve this problem, you must add these users as guests in the tenant specified in the request. You can use the corresponding sign-in URL for a specific type of application. Some examples are mentioned below:
For the Multitenant applications type, you can use the following sign-in URL.
https://login.microsoftonline.com/organizations
If you’re using Multitenant and personal accounts type, then you can use the following sign-in URL.
https://login.microsoftonline.com/common
For personal accounts only, use this sign-in URL.
https://login.microsoftonline.com/consumers
3] Sign out, then sign in again from a different browser or a private browser session
Sometimes this error occurs when the user signed in to the wrong tenant. For example, when a user already has an active session in his web browser and he/she tries to access your application by clicking on the respective link or entering the required URL in a new tab.
In this situation, ask the guest user to do one of the following things:
- Sign out of the account already opened in his/her web browser. This will end the already active session. Now, he/she can sign in by using the correct link and credentials.
- Sign in using a different web browser.
- Sign in in the Private or Incognito window in the same web browser.
4] Invite the guest user
This error also appears when the guest user is not invited. The solution to this situation is straightforward. Invite the guest user.
5] Assign access to users (if applicable)
If your application is an enterprise application that requires user assignment and the user is not in the list of allowed users who have been assigned access to the application, then this error will occur.
You can check if your enterprise application requires user assignment or not by following the steps provided below:
- Go to the Azure portal.
- Select the Enterprise application(s).
- Select your enterprise application.
- Select Properties.
- Check whether the Assignment Required option is set to Yes. If it is set to Yes, then that application requires the user assignment.
In this situation, Assign access to users individually or as part of a group.
6] Use an endpoint that’s specific to the tenant or organization
The error code AADSTS50020 can also occur when a user tries to use the Resource Owner Password Credential (ROPC) flow for his/her personal account(s). Microsoft Identity Platform only supports ROPC within Azure AD tenants and not personal accounts.
In this situation, the user has to use the endpoint that is specific to the tenant or organization. Do note that personal accounts cannot use ROPC even if they are invited to an Azure AD tenant.
7] Reset the redemption status of the guest user account
If the administrator has deleted the username of the guest user in the resource tenant and re-created it in the home tenant, the guest user will encounter this error. The administrator should also verify that the guest user account in the resource tenant is not associated with the guest user account in the home tenant.
To fix the error in this situation, reset the redemption status of the guest user account in the resource tenant.
That’s it. I hope this helps.
What tenant ID is used in Azure?
The tenant ID in Azure is a unique identifier for an Azure Active Directory (Azure AD) tenant. It is also called Office 365 tenant ID. There are different ways to get your Azure Tenant ID.
Who is tenant admin?
A tenant admin is a user who has the highest level of permissions in an Azure Active Directory (Azure AD) tenant. He/she can manage all aspects of the tenant, including users, groups, permissions, and settings.
Read next: Error AADSTS90100, Login Parameter is empty or not valid.