Border Gateway Protocol or BGP, for short, helps in tracing the route of data packets so that the packets can be delivered using as few nodes as possible. The nodes here, refer to autonomous networks that are all joined to create one vast Internet.
What is Border Gateway Protocol
When I was in school, our class visited a post office to see how it works. The postmaster told us that they sort mail by destinations and put them in corresponding bags. Sometimes a straight route is not possible, so some mail is forwarded to a post office near to the destination and that post office makes it possible to deliver the mail by sending it forward according to the address.
Border Gateway Protocol represents a post office. You can say it is the post office of the Internet. The data packets we generate while working on the Internet have to be routed through different autonomous networks so that they can reach the destination IP address. The Internet is a lot of networks that look like one huge network. The Internet is thus a network of autonomous networks. These autonomous networks are provided by ISPs, governments, and tech organizations, etc.
Is BGP safe? How can BGP be hijacked?
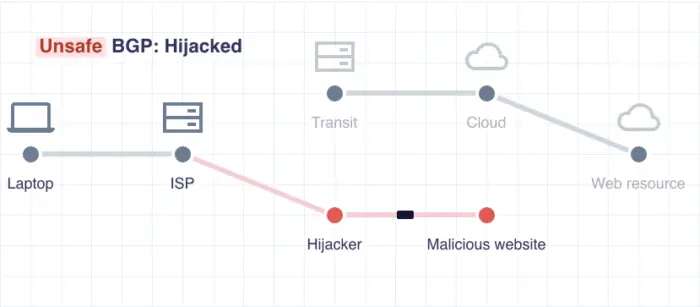
Different entities set up these autonomous networks and decide what nodes of the Internet to use so that the data packets reach their destination without getting lost. However, rogue nodes on the path hijack the data route by poisoning one or more real nodes on the Internet.
When a data packet is to be moved from A to B to C to D, where D is the destination, it is sent to A. This node contacts the next node, B, so that it can be forwarded to the destination. If any hijacker creates a fake node B and poisons the real B, the data packet will move from A to the fake node B. This malicious node will now redirect the data packets to some similar-looking malicious website.
In other words, the Border Gateway Protocol is not safer when used alone. According to Cloudflare, there is a method that makes it safer to use the Internet without falling prey to hijackers.
Resource Public Key Infrastructure (RPKI)
The Resource Public Key Infrastructure, or RPKI, is a service that protects data packets from being hijacked on BGP networks. This technique employs cryptography when querying the route to be taken for the data packets. Thus, using RPKI over Border Gateway Protocol (BGP) helps secure data and prevents the hijacking of nodes being used in an Internet route.
To see if your Internet Service Provider is using Border Gateway Protocol properly, visit IsBGPsafeyet.com and click Test your ISP button on the page.
To sum up:
- BGP is a protocol that creates a route for data packets to reach their destination
- BGP is not very safe if implemented alone
- RPKI employs cryptography, which helps avoid malicious nodes when used in combination with the Border Security Protocol (BGP).