Hackers use many methods to get into a computer, computer network, website or online service. Carrying out a Brute Force Attack is one of them. Hacking a server or a normal computer is one of the simplest yet time-consuming methods. The Brute force attack mechanism has its advantages – it can also be used to check network security and to recover forgotten passwords. In this post, we will try and understand Brute Force Attack definition and see the basic prevention method.
What are Brute Force Attacks?
A Brute Force Attack is a type of Cyber Attack, where you have software spinning up different characters to create a possible password combination. The Brute Force Attack password cracker software simply uses all possible combinations to figure out passwords for a computer or a network server. It is simple and does not employ any intelligent techniques. Since it is math-based, it takes less time to crack a password using brute force applications rather than figuring them out manually. I said math-based because computers are good at math and perform such calculations in split seconds compared to human brains, which take longer to create combinations.
Brute Force Attack is good or bad depending upon the person using it. It could be a cybercriminal trying to hack into a network server or it could be a network admin trying to see how secure his or her network is. Some computer users also use brute-force apps to recover forgotten passwords.
A notable example of a brute force attack is the 2016 LinkedIn incident, where attackers used automated software to guess the passwords of 117 million accounts. This led to a significant data breach, underlining the importance of robust password policies and security measures.
Speed of computing & passwords matter during Brute Force Attacks
If you use all lower letters and no special characters or digits, it might be a work of 2-10 minutes before a brute force attack can crack the password. However, a combination of upper case and lower case letters and a digit (supposing there are eight digits), will take more than 14-15 years to crack the password.
The primary weakness of a brute force attack lies in its need for extensive time and computing power to try all possible password combinations. This inefficiency is exacerbated by stronger security measures such as long, complex passwords, two-factor authentication, and the use of unique passwords, all of which significantly reduce its success rate.
It also depends upon the speed of the computer processor as to how long it takes to crack the password of the network or normal login to a Windows standalone computer.
Thus, it makes a lot of sense to have strong passwords. To create really strong passwords you can make use of ASCII characters to create stronger passwords. ASCII characters refer to all the characters available on the keyboard and more (you can see them by pressing ALT+numbers (0-255) on Numpad).
There are some 255 ASCII characters and each one has a code that is read by a machine and converted to binary (0 or 1) so that it can be used with computers. For example, the ASCII code for “space” is 32. When you enter a space, the computer reads it as 32 and converts it into binary – which would be 10000. These 1, 0, 0, 0, 0, 0 are stored as ON, OFF, OFF, OFF, OFF, OFF in the computer’s memory (that is made of electronic switches). This has nothing to do with brute force except that in the case of the use of all ASCII characters if you use special characters in the password, the total time taken to crack the password could run above 100 years or so.
I spoke about ASCII for people who do not know how characters are stored in the computer’s memory.
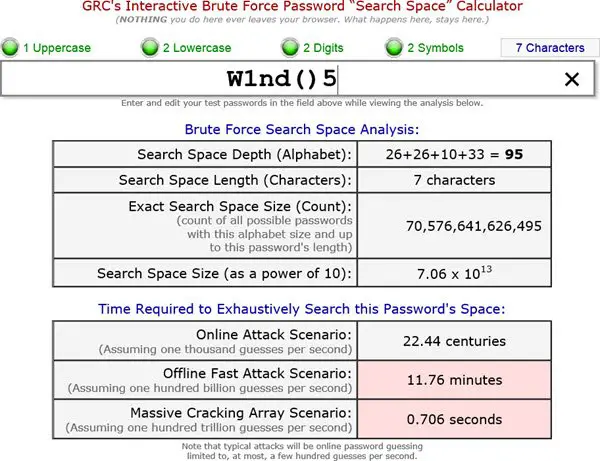
Here is a link to a Brute Force Password Calculator, where you can check out how long it will take to crack a password. There are different options given that include lower case letters, upper case letters, digits, and all ASCII characters. Based on what you used in your password, select the options and click on calculate to see how difficult it would be for a Brute force attack to compromise your computer or server.
Read: Password Cracking attacks, methods, prevention
Brute Force Attack Prevention & Protection
Since no special logic is applied in brute force attacks except for trying out different combinations of characters used for the creation of a password, prevention on a very basic level, is relatively easy.
Apart from using a fully updated Windows operating system and security software, you should use a strong password that has some of the following characteristics:
- At least one upper-case letter
- At least one digit
- At least one special character
- The password should be a minimum of 8-10 characters
- ASCII characters, if you wish.
The lengthier a password is, the more time it will take to crack the password. If your password is something like ‘PA$$w0rd”, it will take more than 100 years to crack it with currently available brute-force attack apps. Please do not use the suggested password in the example, as it is very easy to break it using some intelligent software that falls out of the realm of brute force attacks.
Our freeware PassBox is a handy little tool that will remember all your passwords and even generate strong passwords for your account – or you could use some free online password generator to create strong passwords anonymously. Having done that, test your new password with Microsoft’s Password Checker. The Password Checker evaluates your password’s strength as you type.
Related read: What is a Password Spray Attack?
If you are using WordPress website software, then many WordPress security plugins automatically block brute force attacks. Another option you can consider is using a web firewall like Sucuri or Cloudflare. One way to block brute-force attacks is to lock out accounts after a defined number of failed password attempts. The Limit Logins WordPress plugin is good for stopping brute-force attacks on your blog. Other measures include allowing logins from only select IP addresses, changing default login URLs to something else, and using Captcha’s to harden your WordPress blog security.
Read next: How to block Brute Force Attacks on Windows Server.
Leave a Reply