In response to the recent Conficker outbreak, Microsoft has made some changes in the AutoRun functionality in Windows 7.
The main purpose of Autorun is to provide a software response to hardware actions that you start on a computer. Autorun has the following features:
– Double-Click
– Contextual Menu
– AutoPlay
These features are typically called from removable media or from network shares. During AutoPlay, the Autorun.inf file from the media is parsed. This file specifies which commands the system runs. Many companies use this functionality to start their installers. AutoRun is used to start some programs automatically when a CD or another media is inserted into a computer.
Certain malware have started making use of the capabilities of AutoRun to provide a seemingly benign task to people – which masquerades as a Trojan Horse to get malware onto the computer. The malware then infects future devices plugged into that computer with the same Trojan Horse. More on Conficker at Microsoft Malware Protection Center.
In order to help prevent malware from spreading using the AutoRun mechanism, AutoPlay will no longer support the AutoRun functionality for non-optical removable media. That is, AutoPlay will work for CDs & DVDs but not for USB drives.
In the following example for a USB flash drive that has photos, malware registers as the benign task of “Open folders to view files.” If you select the first “Open folders to view files” (circled in red), you would be running malware. However, if you select the second task (circled in green), you would be safe running the Windows task.
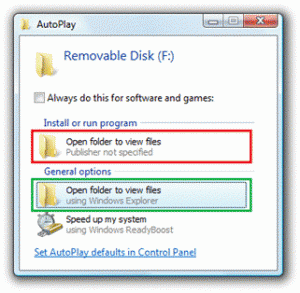
Most would be confused why they have two tasks that appear to do the same thing.
Windows will no longer display the AutoRun task in the AutoPlay dialog for devices that are not removable optical media (CD/DVD.) because there is no way to identify the origin of these entries. Was it put there by the IHV, a person, or a piece of malware? Removing this AutoRun task will block the current propagation method abused by malware and help customers stay protected. People will still be able to access all of the other AutoPlay tasks that are installed on their computer.
With these changes, if you insert a USB flash drive that has photos and has been infected by malware, you can be confident that the tasks displayed are all from software already on your computer.
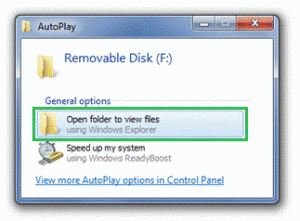
On the other hand, if you insert a CD that offers software to install, Windows will still display the AutoRun task provided by the ISV during their media creation process.
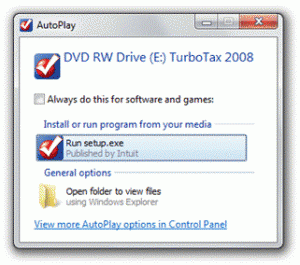
This change will soon be seen in Vista & XP too. More at E7 Blogs.
Leave a Reply