Cyber-attacks have changed over the past few years. Rogue hackers can now take over your PC and lock down files unless you are ready to pay them money. These types of attacks are called Ransomware, and they use kernel-level exploits that attempt to run malware with the highest privileges, e.g., WannaCry and Petya ransomware. In order to mitigate these types of attacks, Microsoft has rolled out a feature that allows you to enable Core Isolation and Memory Integrity to prevent such attacks.
What is Core Isolation?
Core isolation is a security feature in Windows that protects important core processes of Windows from malicious software by isolating them in memory, by running those core processes in a virtualized environment. Core Isolation feature include Memory integrity and Kernel-mode Hardware-enforced Stack Protection.
What is Memory Integrity?
Memory integrity, also known as Hypervisor-protected Code Integrity (HVCI) is a security feature in Windows that makes it difficult for malicious programs to use low-level drivers to hijack your computer.
Windows Defender Security Center offer these features. Called Device Security, it offers status reporting and management of security features built into your devices – including toggling features on to provide enhanced protection. However, It doesn’t work on a software level; the hardware needs to support it as well. Your firmware should support Virtualization, which enables the Windows 11/10 PC to run applications in a container, so they don’t get access to other parts of the system.
Your device must meet the requirements for standard hardware security This means your device should support memory integrity and core isolation and also have:
- TPM 2.0 (also referred to as your security processor)
- Secure boot enabled
- DEP
- UEFI MAT.
Enable Core Isolation & Memory Integrity in Windows 11/10
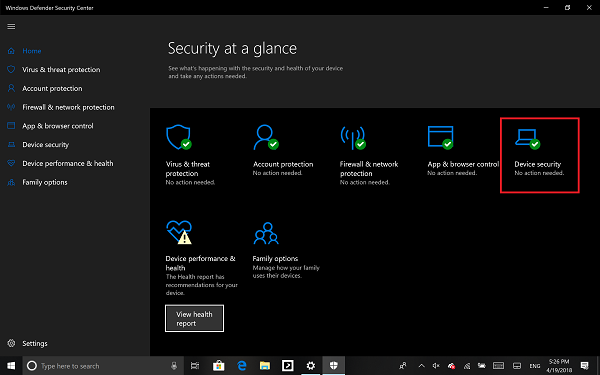
- Sign in as an administrator and open Windows Defender Security Center
- Look for Device Security option.
- Here you should check if Core Isolation under Virtualization is enabled on your PC.
- Core isolation provides virtualization-based security features to protect core parts of your device.
- Click on Core isolation details, and you will be offered to enable Memory Integrity.
Memory integrity (hypervisor-protected code integrity) is a security feature of Core isolation that prevents attacks from inserting malicious code into high-security processes. Toggle to turn it On.
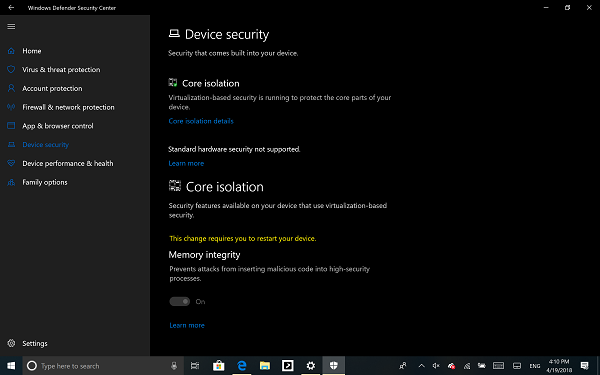
Once enabled, it will ask you to restart the PC to completely enable Memory Integrity.
If later on, you face application compatibility issues, you may need to turn this off.
Related: Memory Integrity greyed out or won’t Turn On/Off.
Enable or Disable Core Isolation and Memory Integrity using Registry
You can also use the Registry, to enable or disable Core isolation Memory integrity using Registry Editor, follow these steps:
- Press Win+R to open the Run dialog.
- Type regedit and hit the Enter button.
- Click on the Yes option.
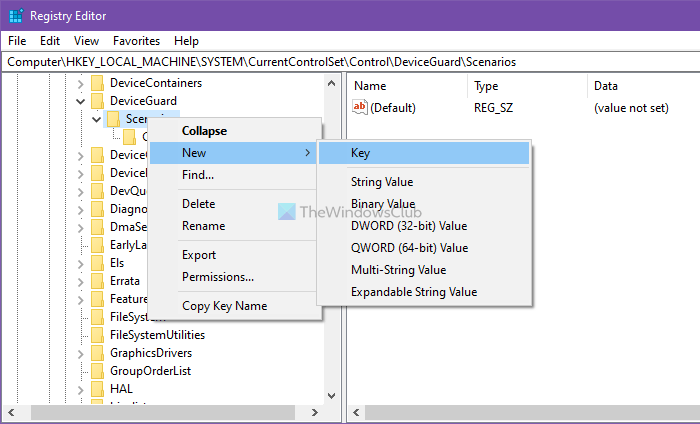
- Navigate to Scenarios in HKEY_LOCAL_MACHINE.
- Right-click on Scenarios > New > Key.
- Name it as HypervisorEnforcedCodeIntegrity.
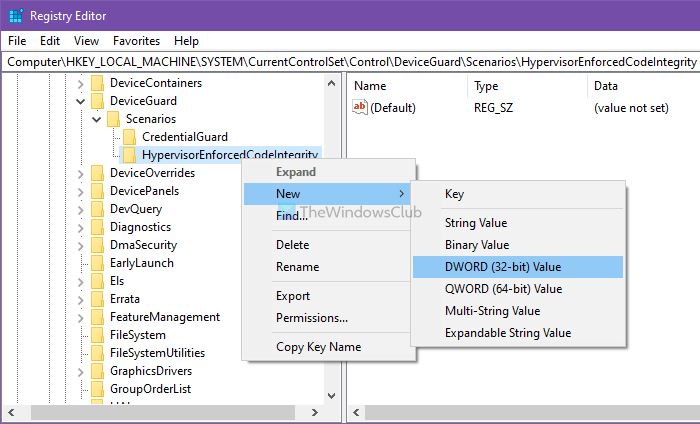
- Right-click on it > New > DWORD (32-bit) Value.
- Name it as Enabled.
- Double-click on it to set the Value data as 1 to enable and 0 to disable.
- Click the OK button.
- Restart your computer.
To learn more about these steps, keep reading.
Precaution: Before heading to the REGEDIT steps, don’t forget to create a System Restore point.
To get started, press Win+R to open the Run dialog, type regedit, and hit the Enter button. If the UAC prompt appears on your screen, click on the Yes option to open the Registry Editor.
Next, navigate to the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios
Right-click on the Scenarios key > New > Key, and name it as HypervisorEnforcedCodeIntegrity.
Then, you have to create a REG_DWORD value. For that, right-click on HypervisorEnforcedCodeIntegrity > New > DWORD (32-bit) Value, and name it as Enabled.
By default, it comes with a Value data of 0, meaning it is disabled. However, if you want to enable this functionality, double-click on it to set the Value data as 1.
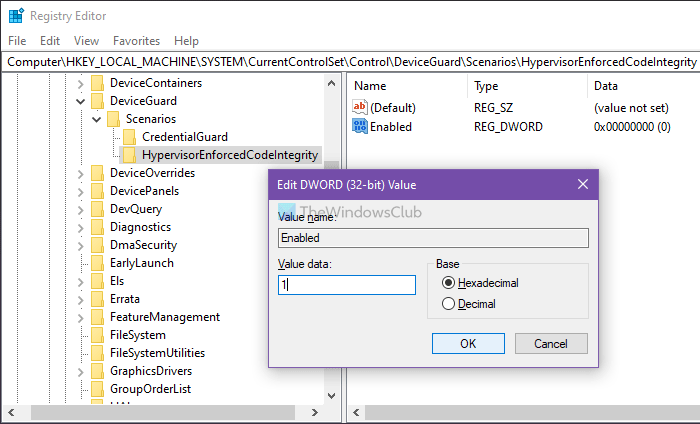
Click the OK button and restart your computer.
Related:
That said, there are two more options that might be available depending on the hardware of your PC.
- Security Processor only shows up if you have TPM available with your PC hardware. They are discrete chips soldered to a computer’s motherboard by the OEM. To get the most out of TPM, OEM must carefully integrate system hardware and firmware with the TPM to send it commands and react to its responses. The newer TPMs can also provide security and privacy benefits to the system hardware itself. So make sure to check for all of these if you are buying a new PC.
- Secure Boot prevents malicious code to load up before your OS. They are hard to crack but with secure boot it’s taken care of.
Windows 11/10 also offers Hypervisor Protected Code Integrity (HVCI) when you start with clean installs. Those who are on old hardware, will have the ability to opt-in post the upgrade using the UI in Windows Defender Security Center (WDSC). This enhancement will ensure that the kernel process that verifies code integrity runs in a secure runtime environment.
What is Memory Integrity Scan Tool?
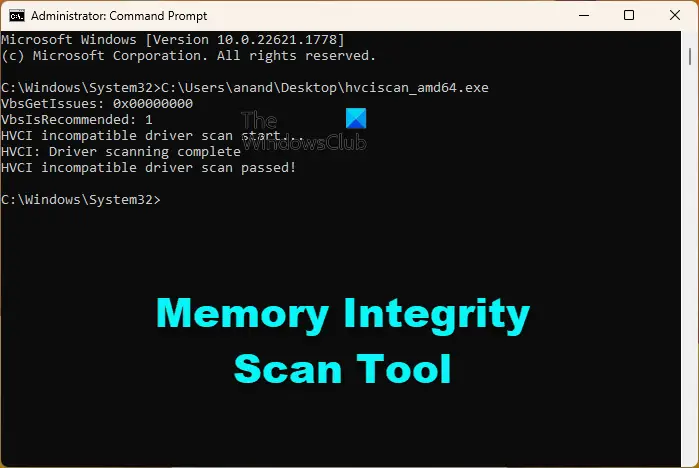
Memory Integrity Scan Tool is a free tool from Microsoft to check your computer’s compatibility with Memory Integrity or HVCI (Hypervisor-protected code integrity).
You can download the hvciscan.exe for your system architecture (AMD64 or ARM64) from the Microsoft Download Center and from an elevated command window or PowerShell, run hvciscan.exe. This will help you review the resulting output to identify any incompatibilities.
Read: Turn off Windows Security Making sure it’s you message
What is Memory access protection?
Kernel DMA protection or Memory access protection protects your device against attacks that can occur when a malicious device is plugged into a PCI (Peripheral Component Interconnect) port like a Thunderbolt port, by denying direct access to the memory to those devices except under special circumstances, particularly when the PC is locked or the user is signed out.
Read:
Small reminder that enabling Hyper-V on Windows breaks a lot of things, from Blu-ray playback to the ability to change (Ethernet) networks from Public to Private (within the Windows GUI.) Every time I enable it I wind up subsequently disabling it because of the problems it causes.