There are many inherent risks associated with wireless protocols and encryption methods. So, to minimize them a robust framework of different wireless security protocols is used. These Wireless Security Protocols assure the prevention of unauthorized access to computers by encrypting the transmitted data on a wireless network.
Difference between WPA2, WPA, WEP Wi-Fi Protocols
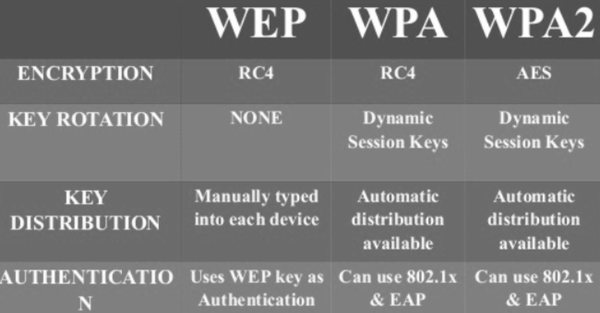
Most wireless access points come with the ability to enable one of three wireless encryption standards:
- WEP (Wired Equivalent Privacy)
- WPA or Wi-Fi Protected Access
- WPA2
WEP or Wired Equivalent Privacy
The first wireless security network to mark its appearance was WEP or Wired Equivalent Privacy. It started off with 64-bit encryption (weak) and eventually went all the way up to 256-bit encryption (strong). The most popular implementation in routers continues to be 128-bit encryption (intermediate).
It was considered as the eventual solution until security researchers discovered several vulnerabilities in it that allowed hackers to crack a WEP key within a few minutes. It used CRC or Cyclic Redundancy Check.
WPA or Wi-Fi Protected Access
To address its shortcomings, WPA was developed as a new security standard for wireless protocols. It used TKIP or Temporal Key Integrity Protocol to ensure message integrity. This was different from WEP in a way, the former used CRC or Cyclic Redundancy Check. TKIP was believed to be much stronger than CRC. The use of it ensured that every data packet was sent with a unique encryption key. Key mixing increased the complexity of decoding the keys and thereby reducing instances of intrusions. However, like WEP, WPA too had a flaw. As such, WPA was advanced into WPA 2.
Read: What is Wi-Fi 6E?
WPA2
WPA 2 is currently recognized as the most secure protocol. The single most important change visible between WPA and WPA2 is the mandatory use of AES (Advanced Encryption Standard) algorithms and the introduction of CCMP (Counter Cipher Mode with Block Chaining Message Authentication Code Protocol) as a replacement for TKIP.
The CCM mode combines Counter (CTR) mode privacy and Cipher Block Chaining Message Authentication Code (CBC-MAC) authentication. These modes have been extensively studied and are found to have well-understood cryptographic properties that provide good security and performance in software or hardware.
Read next: WPA3-Personal and WPA3-Enterprise Wi-Fi Encryption explained.
Leave a Reply