If a code loading from the default heap or stack is detected by DEP or Data Execution Prevention, an exception is raised. It happens since the behavior is indicative of malicious code (legitimate code does not generally load in this manner). This way DEP protects the browser against attacks rendered, for example, via buffer overflow and similar type vulnerabilities.
Although a valuable feature, DEP can sometimes be the cause of certain system issues and error messages. So, if you would like to disable Data Execution Prevention for the Internet Explorer browser only, here is how you can do it :
Disable Data Execution Prevention DEP for Internet Explorer
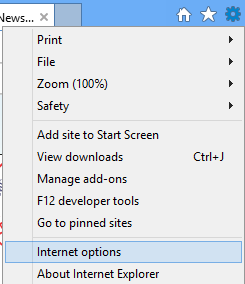
Open Internet Explorer and go to ‘Tools’. The icon appears as a small gear-shaped icon at the extreme top-right corner of Internet Explorer screen. Click open ‘Tools’ and from the displayed options, select ‘Internet Options’.
Next, click on ‘Advanced’ tab and scroll down until you find the ‘Security’ option. Un-check on Enable memory protection to help mitigate online attacks.
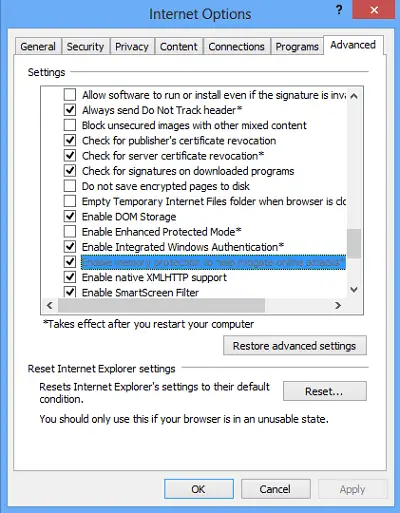
Click Apply / OK. This will disable Data Execution Prevention for Internet Explorer.
To enable Data Execution Prevention, check the check-box instead, click Apply and Exit.
Want to have a look at these posts too?
Does DEP slow down IE? Does it slow down the whole system? I have a 4 yr old netbook and I need all the speed I can get.
My netbook won’t let me uncheck it. What else can I do?
No it wont slow down the system.
Please make sure you are signed in as an administrator.
Maybe it’s because my netbook has Windows 7 Starter that it won’t let me change it? I am signed in as an admin.
Yes, maybe that’s the reason…
How can DEP be unabled on IE11 in a Surface pro?
i dont see this option in IE 11 under Security Settings
I don’t see it in my IE11 installation either, it must be something they deleted from that version of Internet Explorer.
Hello, I don’t have that Option “Enable memory protection to help mitigate online Attacks” in my Internet Explorer Options……can you help please ?
The “enable memory protection…. tab does not appear when I check IE. I have 64bit system
IN EFFETTI DOPO AVER INSTALLATO EMET DI MICROSOFT…MI SONO TROVATO ANCHE INTERNET EXPLORER (DEP) X 64…MAI INSTALLATO DA ME. INOLTRE HO DOVUTO DISINSTRALLARE EMET 5.O1 PERCHE FUNZIONAVA BENE MA CREAVA PROBLEMI AL COMPUTER…RITARDI…BLOCCHI..CRASH ECC….L.HO DISINSTALLATO ED AMEN.