In the past few months, we have written a couple of articles related to Internet Privacy. We talked of how DNS works, free VPNs such as SpotFlux, NeoRouter, CyberGhost VPN, etc., as well as private browsers that hide your identities, such as the Jumpto browser, and more. In the same series, this post is about DNSCrypt, a lightweight program that encrypts the exchange of data between your computer and the DNS Servers. In a way, it is all about your privacy, as men in the middle (hackers) won’t be able to understand what is happening on your Windows computer.
DNSCrypt review
What is DNSCrypt – Why Do I Need It
You know about the VPNs that encrypt your data and exchanges it in a secure tunnel created between your computer and the host. Though VPNs provide better security and privacy of DNSCrypt, they often slow down your browsing. Proxies are for accessing sites (by changing your IP address). They don’t provide encryption in most cases. We also discussed certain DNS (example OpenDNS) that provide content filtering in addition to a secure (anti-malware) connections. You know that not all websites are not safe. Comodo and OpenDNS perform a check when you request a website connection and will inform you if the website is dangerous. OpenDNS also offers content filtering that can be called Parental Controls over the network. You do not need to configure it on all computers.
Normally, with the above (exception: VPNs), your data is exposed to the “man in the middle” when you send a website request, email or even an IM. To protect this data, you need something that encrypts your data between your computer and the DNS server you are using. The DNS server could be anything of your choice. DNSCrypt is a program that provides encryption of this data (between you and the DNS). You can select from the listed service providers or use the Network Adaptor settings to change the DNS manually.
NOTE: In some cases where you select your DNS other than the ones listed in DNSCrypt, it creates problems connecting to the Internet. I would recommend using popular DNS servers, as they pose fewer problems. If you select the ones listed in the DNSCrypt, you might not face any problem at all.
In short, if you are not using a VPN, the DNSCrypt will help you stay safe when communicating on the Internet. Communication can be anything from email to IM to browsing websites.
DNSCrypt will encrypt and protect data
Where to download DNSCrypt
There are many sites offering DNScrypt download. The main source is at GITHUB that also contains the code of the program so that you can check whether it is programmed to encrypt the data or not.
But downloading from GITHUB gives you a confusing version of DNSCrypt. The link to download is towards the bottom right corner of the screen – marked as “Download ZIP”. This ZIP file contains many folders that need to be extracted to some safe place so that your copy of DNSCrypt keeps working. See the image above for an idea of how extracted files look.
There is another site from where you can download DNSCrypt so that you can install it as a Windows Service. This is also a DNSCrypt ZIP file containing only four files. The link to download DNSCrypt Windows Service leads you to a website of a programmer named Simon Clausen – simonclausen.dk. The page also tells you about the benefits of the program. I prefer downloading it from Simon Clausen’s website rather than GITHUB. The latter is a bit complicated as it has too many files and you may not know which one to run first.
Read: What is DNSCrypt Protocol.
How To Install DNSCrypt
If you downloaded the ZIP file from GITHUB and extracted the contents, get the following folders. They look confusing, but you open the DNSCrypt folder and the run the only executable there. There is an upgrade folder when you extract it, but I was not able to understand what it meant. Maybe it was patched or maybe upgrades with new features. There are some six upgrade files. I could not find details about this.
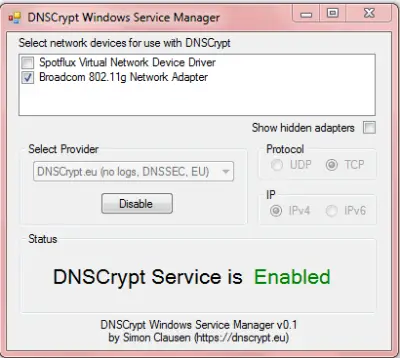
If you downloaded the ZIP file from Simon Clausen’s website, all you need to do is to extract the files and run dnscrypt-winservicemgr.exe. You will get a graphical interface as shown in the image below. You can choose your adaptor, type of communication (UDP or TCP), and also service providers (such as OpenDNS, etc.) before clicking Enable. After you click Enable, simply close the window. The process runs in the background, and you can view it in Windows Task Manager -> Process Tab.
How to remove DNSCrypt Windows Service
Always create a restore point before installing such software because if anything goes wrong (such as incorrect configuration), you can restore your computer back to before the program was installed. In the case of DNSCrypt, you will not find any entry in Programs and Features.
System Restore is the only way to remove it. Alternatively, you can go to Services from Control Panel -> Administrative Tools and disable the dnscrypt service. Right-click on the service listed as dnscrypt-proxy and click on Disable or Manual Start.
Conclusion
I prefer using the installer ZIP from Simon Clausen as it is easy and has a simple GUI to help you set it up. I had fears that the DNS resolving time may increase after installing this, but no such thing happened, meaning your browsing speed won’t decrease. It encrypts and thus provides safety and privacy to your data. It does not take up many resources on your computer. I recommend using the product for added safety while you are browsing, sending emails, or chatting.
Similar tool: Simple DNS Crypt.
As it says for third paragraph at DSNCrypt’s own site: “While not providing end-to-end security, it protects the local network, which is often the weakest point of the chain, against man-in-the-middle attacks. It also provides some confidentiality to DNS queries”.
DNSCrypt does offer 255 bit server public key Curve25519 elliptical curve encryption to any DNS request, should anyone be spoofing ARP, Wiresharking, e.g. … but if the page you land at doesn’t support HTTPS, everything falls back to cleartext (or as some say “plaintext”) in re hackers seeing page you intended to get to via TLS.
For what it’s worth, symmetric key algorithm products (e.g., Twofish, Serpent, AES, Blowfish) are better (except for Heartbleed-friendly RC4 which many banks still use due to one-time BEAST vulnerability). While no encryption scheme is ever completely break-free, today’s symmetric algorithms are less susceptible to hacker plaintext decryption attacks than any form of elliptical curve (including Diffie-Hellman) or the older RSA discrete logrithm encryption (developed similarly but independently 1973-1977 by UK’s GCHQ, and by Ron Rivest/Adi Shamir/Leonard Adelman the surnames of whom resulted in acronym “RSA”).
Your article thus is still important for those needing at least some hacker protection, and DNSCrypt gets a bit better if a trustworthy DNS resolver and HTTPS Everywhere-type mechanism are also operative. Hope this is of use, thanks for another great article, cheers!
Can you please do something about your writers’ English? Sometimes it is just plain difficult to understand. Thank you.
Warning: anybody with basic knowledge about crypto can get a heart attack after reading this.
Although the points you raise are factually correct and technically straight forward, with all due respect.. please get over yourself Dan.
As far as advancements go in protocols, DNS has been neglected since its adoption. Reason being, it simply worked as it should. DNS was never intended to incorporate security measures. However over the years of developments in many other interacting protocols, introductions of new technologies and the many, many inventive and unconventional ways people find to use these these technologies, DNS has finally received some much need attention. DNS
I commend the team for their work on DNSCrypt and support it’s continued development. I’m glad it’s finally getting some well deserved attention!
I use DNSCrypt constantly running in the background on win8.1 without a problem. I forget it’s even doing it’s work for me. I also use it while I’m connected to VPN and it has not failed me yet.
You can test your DNS queries with a quick check at https://dnsleaktest.com/
I highly recommend people to test it for themselves. Do a test before running DNSCrypt, then do a test with it running… and you will see the results for yourself.
I’m glad that you helped point those things out for the benefit of others who may not be as proficient in computer aspects as say yourself, Mr. Kumar, Bill Gates, and so forth. When a topic appears to not have anyone else talking on an issue and I humbly believe something more needs to be said for benefit of getting any less issue-experienced persons on their own path of inquiry, I give details as I believe I might be helpful. Also, have you any inputs about tests you’ve done with Wireshark or Networkminer as to how any eavesdropping on, say, DNSCrypt connected to dnsleaktest does or does not easily see the plaintext of that HTTP connection, when not using a VPN? Any HTTP requests always showed up for me, so I was wondering how you might have fared when not using a VPN with its own DNS servers.
I think you missed my point Dan …but without wasting any more time on this, you can check a quick screen dump of a https://www.grc.com/dns/dns.htm test I just done. I would say that’s a result :)
http://imgur.com/d43jgtT
Is dnscrypt-proxy-win32-full-1.4.0 a virus ?
https://www.virustotal.com/he/file/f93e3a796563c395565d95e32bffa804ea71e65ff8bcc48450dcc55c4aa29d1e/analysis/
Okay, curve encryption in re OpenDNS DNSCrypt: it has an option to enable allowing fallback to non-secure DNS, as a few issues including and apart from firewalls can cause the utility issues in some user cases; if this option is checked, although DNSCrypt will constantly say “Protected”, the user has no casual way of knowing if the utility made this, that, or all requests via cleartext as it alone “felt” necessary…even if “Shields Up!” or other sites can be reached securely.
I guess the only way for someone to know for sure they’re not operating as if w/o a VPN or as if falling back to cleartext, if they enable fallback in DNSCrypt, is to monitor their traffic…not ask for my opinions as to what is possible.
agreed, you can be sure of the trust in the destination of the packets, however the “fail safe” option is something to consider …and that’s where Wireshark makes it’s star entrance.
I highly recommend everybody to have a look at this development by Simon Clausen http://simonclausen.dk/projects/dnscrypt-winservicemgr/ he deserves some credit for this. I used the packaged distribution of DNSCrypt before coming across this.
Do Check (http://www.snapfiles.com/get/dnscrypt.html) I use this OpenDNS DNScrypt
Link is broken.
I put the bracket but, do check it out http://www.snapfiles.com/get/dnscrypt.html
this is with out any link
I mean the correct link without any brackets http://www.snapfiles.com/get/dnscrypt.html
Its working fine, http://www.snapfiles.com/screenshots/dnscrypt.htm
do check this link