Have you ever felt an unusual slowness in your network speed or unexpected unavailability of a certain website? Chances could be that there could be a Denial of Service attack in progress. You might be familiar with the term – Denial of Service but in reality, it can be difficult to distinguish between a real attack and normal network activity. Denial of Service (or DoS) attack, which, as the name suggests, directly relates to being denied a service, notably, the Internet.

A DoS attack is a kind of attack that eats upon a user’s resources and brings the network down to its knees, thereby preventing legitimate users from accessing any website. The DoS attack has been and remains one of the most sophisticated attacks to which one does not have a potential prevention policy. In this post, we’ll shed some light on what is a DoS attack and how to prevent it better and what to do in case you know that you’re attacked.
What is DoS or Denial of Service Attack
In a DoS attack, an attacker with malicious intent prevents users from accessing a service. He does so by either targeting your computer and its network connection or the computers and network of the website that you are trying to use. He can thus prevent you from accessing your email or online accounts.
Imagine a situation where you are trying to log into your Internet Banking account for online transaction activity. However, as strange as it may seem, you are denied access to the bank’s website despite having a swift internet connection. Now there could be two possibilities – either your internet service provider is down or you’re under a DoS attack!
In a DoS attack, the attacker sends a flood of superfluous requests to the website’s main server, which basically overloads it and blocks out any further requests before the capacity is retained. This causes a denial of the incoming legitimate requests for this website, and consequentially, you’re the victim.
However, the ways of attack may differ based on the attacker’s motives, but this is the most common way to launch a DoS attack. Other ways of attacking may involve preventing a particular person from accessing a certain website, obstructing the connection between two machines at the server end, disrupting the service, etc.
Some attackers also act on another kind of DoS attack – Email bombing in which a lot of spam emails are generated and flooded into one’s Inbox so that any further request to the mail server is debarred. This can happen widely, even on the email account provided to you by your employers, not to mention the public mail services like Yahoo, Outlook, etc. You can even get deprived of receiving any further legitimate emails as your allotted storage quota will be filled up. With a great deal of variety in their ambitions, the motivation of attackers may range from ‘just-for-fun’ to financial clinch to revenge.
Related: Browser stuck at Checking Your Browser Before Accessing message.
Types of DoS Attacks
Based on the nature and intent of the attack, several types of programs can be used to launch DoS attacks on your network. Take note of the below most commonly used DoS attacks:
1] SYN Flood
SYN Flood takes undue advantage of the standard way to open a TCP connection. When a client wants to open a TCP connection with the server’s open port, it sends out a SYN packet. The server receives the packets, processes it, and then sends back a SYN-ACK packet which includes the source client’s information stored in Transmission Control Block (TCB) table. Under normal circumstances, the client would send back an ACK packet acknowledging the server’s response and hence opening a TCP connection. However, under a potential SYN flood attack, the attacker sends out an army of connection requests using a parody IP address which are treated as legitimate requests by the target machine. Subsequently, it gets busy processing each one of these and makes an attempt to open a connection for all of these malevolent requests.
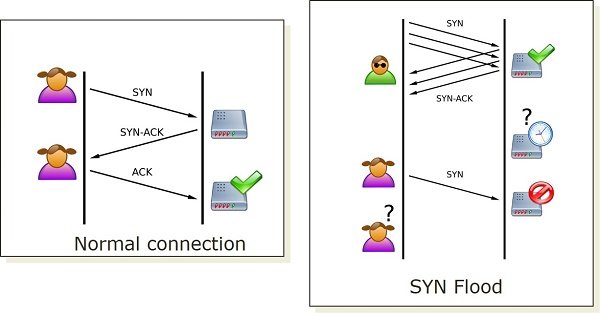
Under normal circumstances, the client would send back an ACK packet acknowledging the server’s response and hence opening a TCP connection. However, under a potential SYN flood attack, the attacker sends out an army of connection requests using a parody IP address which are treated as legitimate requests by the target machine. Subsequently, it gets busy processing each one of these and attempts to open a connection for all of these malevolent requests. This causes the server to keep waiting for an ACK packet for each connection request which actually never arrives. These requests quickly fill up the server’s TCB table before it can time any connection out and thus any further legitimate connection requests are pushed into the waiting queue.
Read: What is Ransom Denial of Service?
2] HTTP Flood
This is most commonly used for attacking web services and applications. Without emphasizing high-rate network traffic, this attack sends out a complete and seemingly valid HTTP POST requests. Designed specifically to exhaust the target server’s resources, the attacker sends out a number of these requests to make sure the further legitimate requests are not pulled through by the target server while it is busy processing the fake requests. Yet, it is so simple, but it is very difficult to distinguish these HTTP requests from the valid ones as the content of the Header seems admissible in both cases.
3] Distributed Denial of Service Attack (DDoS)
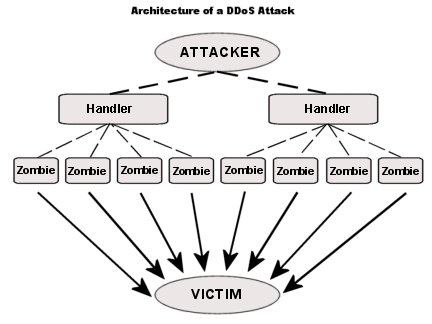
Distributed Denial of Service or DDoS attack is like the decorated officer in this gang. Much sophisticated by levels above normal DoS attack, DDoS generates the traffic on the target machine via more than one computer. The attacker controls several compromised computers and other devices at once and distributes the task of flooding the target server with traffic, heavily eating on its resources and bandwidth. The attacker can also use your computer to launch an attack on another computer if there are lingering security issues.
Now, as obvious as it is, a DDoS attack can be much more effective and real when comparing to DoS. Some websites that can easily handle multiple connections can be brought down easily by sending numerous simultaneous spam requests. Botnets are used to recruit all sorts of vulnerable devices whose security can be compromised by injecting a virus into them and signing them up for Zombie army which the attacker can control and use them for a DDoS attack. Hence, being a normal computer user, you need to be aware of security loopholes in and around your system; otherwise, you might end up doing somebody’s dirty work and never know about it.
DoS attack prevention
DoS attacks can not be pre-determined. You can’t prevent being a victim of the DoS attack. There are not many effective ways to that. However, you can reduce the prospect of being a part of such an attack where your computer can be used to attack another. Take note of the salient points which can help you get the odds in your favor.
- Deploy an antivirus program and firewall into your network if not already done. This helps in restricting the bandwidth usage to authenticated users only.
- Server configuration can help diminish the probability of being attacked. If you’re a network administrator at a firm, review your network configurations and harden the firewall policies to block unauthenticated users from addressing the server’s resources.
- Some third-party services offer guidance and protection against DoS attacks. These can be expensive but effective as well. If you have the capital to deploy such services in your network, better get going.
DoS attacks are generally targeted to high-profile organizations such as banking and financial sector companies, trade and commercial stubs, etc. One should be fully aware and keep looking over one’s shoulder to prevent any potential attacks. Although these attacks do not directly relate to the theft of confidential information, it can cost the victims a hefty sum of time and money to eliminate the problem.
Pretty good article, but HTTP Floods aren’t post specific, could be GET requests as well.