Windows Security Center in Windows 11/10 introduces a new security protection feature called Exploit Protection. With the introduction of this feature, Windows 11/10 users now no longer need to install Enhanced Mitigation Experience Toolkit. In fact, during the upgrade process itself, Windows 10 uninstalls EMET.
Exploit Protection helps protect your Windows computers from malware that use security exploits to infect your system. It includes mitigations that you can apply at the operating system level, or at the app level, as well. It can prevent codes from being run from data-only memory pages, terminate a process when heap corruption is detected, etc.
Exploit Protection in Windows 11/10
Exploit Protection is a part of the Exploit Guard feature in Windows Defender. To access this feature, open Windows Defender Security Center > App and browser control > Exploit protection settings. In Windows 11, you can access the Exploit Protection feature using the Windows Security app. Open the Settings app, go to Privacy & security category, and select the Windows Security option. Press the Open Windows Security button to open the app interface. Select the App & browser control category in the app and click on the Exploit protection settings option. A new panel will open. Scroll down a bit, and you will see the Exploit Protection options here.
The settings are divide under two tabs:
- System settings
- Program settings.
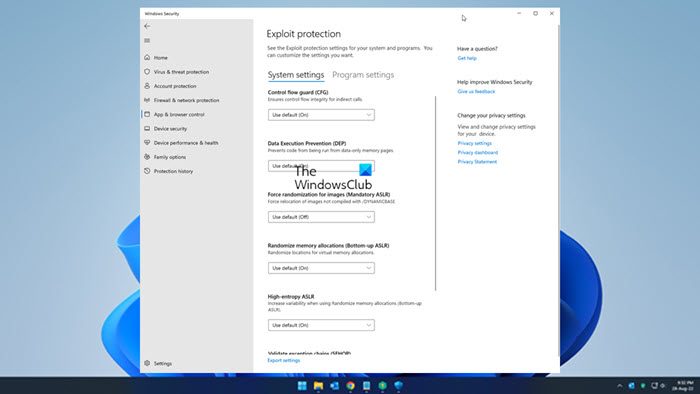
Under System settings you will see the following options:
- Control Flow Guard
- Data Execution Prevention
- Force randomization for images.
- Randomize memory allocations
- Validate exception chains
- Validate heap integrity.
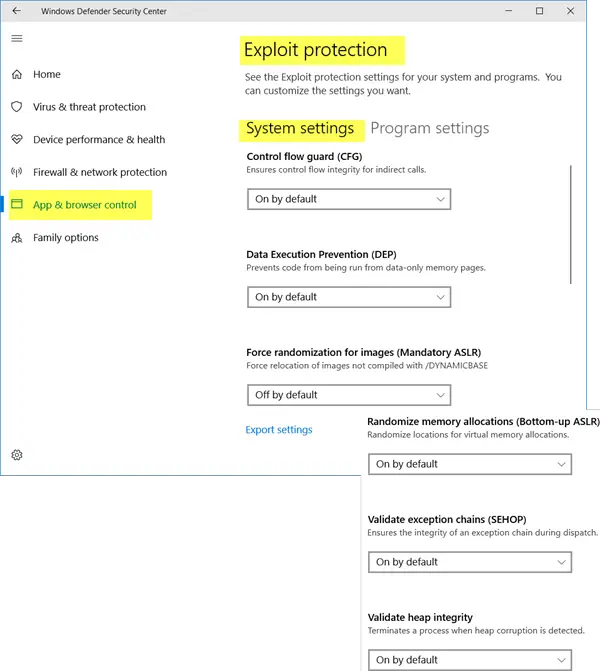
Under Program settings, you will see an option to add a program. Clicking on Add program to customize will offer two options:
- Add by name
- Add by path name.
You may also click on a program in the pre-populated list to add it.
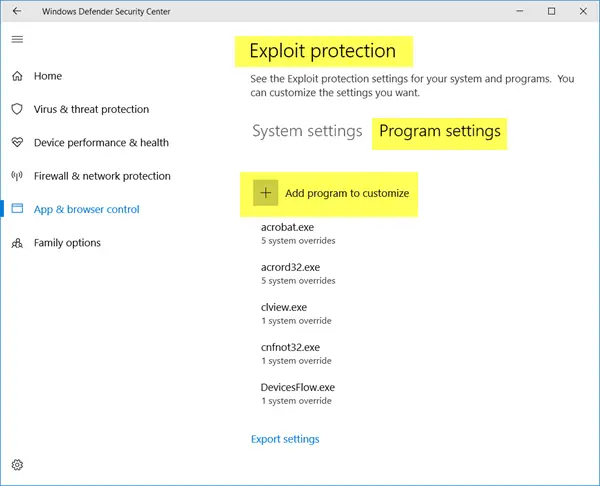
The feature also allows you to Export your settings in an XML file, so that you can save it, using the Export settings link. If you were using EMET and have saved its settings in an XML file, you can also import the settings here.
To import the configuration file, you will have run the following command in PowerShell:
Set-ProcessMitigation -PolicyFilePath myconfig.xml
You have to change file name ‘myconfig.xml’ to the location and name of your Exploit protection configuration file.
Windows Defender does not have to be running for this feature to be active. Exploit Protection is already enabled on your computer and mitigations set by default. But you can customize the settings to suit your organization and then deploy it across your network.
This post will show you how to exclude an app in Exploit Protection of Windows 11/10.
TIP: Read about Controlled Folder Access feature next.
Leave a Reply