The Registry Editor in Windows stores encrypted data to keep the information safe and secure. It is useful when you want to safeguard sensitive data like user account password, database credentials, etc. into the registry. However, sometimes you might want to peek into the data stored in these encrypted registry keys. EncryptedRegView is a free tool which can decrypt the secret registry data that has been stored in encrypted form.
Decrypt registry data with EncryptedRegView
You can use EncryptedRegView to disclose the crypt data stored in Registry editor or feed any registry file (.reg extension) saved locally. The program need not be installed as you can just download and run the executable file to launch the tool. Available in both 32-bit and 64-bit versions, the utility works smoothly across all versions of Windows.
Upon execution, it searches for the data stored anywhere in the Registry Editor which is encrypted using DPAPI (Data Protection API), a cryptographic API developed by Microsoft and is available in Windows OS for the ages. Let’s take a look at how the tool works.
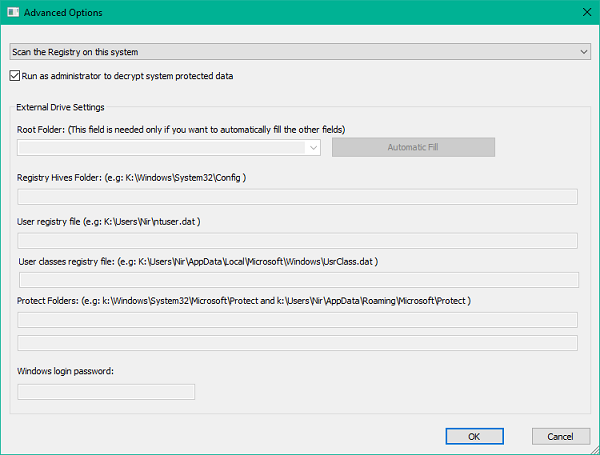
Once you open the utility, you are greeted with the Advanced Options window, where you can choose to scan the system registry editor or the registry of an external drive. You can also choose to run the application as an administrator to decrypt system-protected data that you can’t decipher using normal privileges.
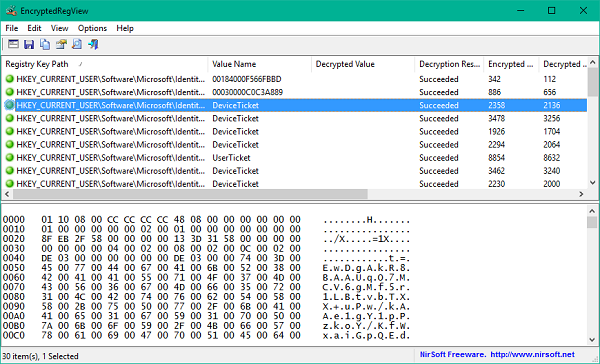
Once all the settings are set, and you click OK to enter main EncryptedRegView window, it starts scanning the registry editor for data encrypted with DPAPI algorithm. If it successfully decrypts the data, you can view the hidden information (in Hex-Dump format) in the lower pane by selecting the respective registry entry from the upper pane.
To decrypt the registry data stored on an external hard drive, you’d need to re-adjust the settings in the Advanced Options window, which you can access by clicking F9 on your keyboard.
Select Scan the registry of external drive from the top drop-down menu and fill in the details for root folder, user registry file, registry hives folder, etc. You can also choose to automatically fill the details by clicking Automatic Fill button. Take note that all the relevant information will be filled as well so if you want to change something, say a registry value for some other user then you’d have to manually enter the path.
EncryptedRegView has several columns in the top pane, and the corresponding fields are auto-filled as it scans through the registry. Let’s take a brief look at what each column means:
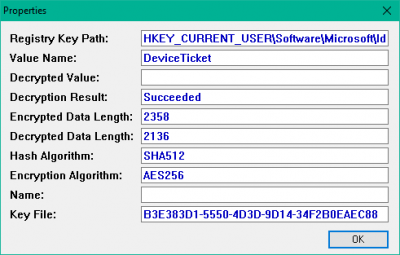
- Registry Key Path: The full path of the Registry key.
- Value Name: The name of the Registry value where the DPAPI encrypted data was found.
- Decryption Result: Result of the decryption – Succeeded or Failed.
- Decrypted Value: If the decrypted data contains a simple string then it’s displayed in this column. The entire decrypted data is displayed in the lower pane.
- Encrypted Data Length: Total length of the encrypted data.
- Decrypted Data Length: Total length of the decrypted data.
- Hash Algorithm: Hash algorithm used in the DPAPI encrypted data. In Windows 7 and later it’s usually SHA512.
- Encryption Algorithm: Encryption algorithm used in the DPAPI encrypted data. In Windows 7 and later it’s usually AES256.
- Name: The name of the DPAPI encrypted data block.
- Key File: Name of the key file that was used to encrypt the data. The key file is located in a ‘Protect’ folder (e.g., C:\ Users\ admin\ AppData\ Roaming\ Microsoft\ Protect )
Using EncryptedRegView, you may find passwords and other secret data stored in the Registry by Microsoft products and third-party products. If you need this tool, you can download it from Nirsoft.