Microsoft recently made available for download, the Enhanced Mitigation Experience Toolkit 5.5. EMET is one of the best security tools for Windows 10/8/7, that helps prevent vulnerabilities in installed software from being exploited by malware and malicious processes. This is achieved with the help of security mitigation technologies, which function as special protections and obstacles that an exploit author must defeat to exploit software vulnerabilities.
If you are using Windows 10 v1709 or later, you do not have to use EMET as the built-in Exploit Protection features in Windows Defender Security Center performs the same function.
Enhanced Mitigation Experience Toolkit EMET
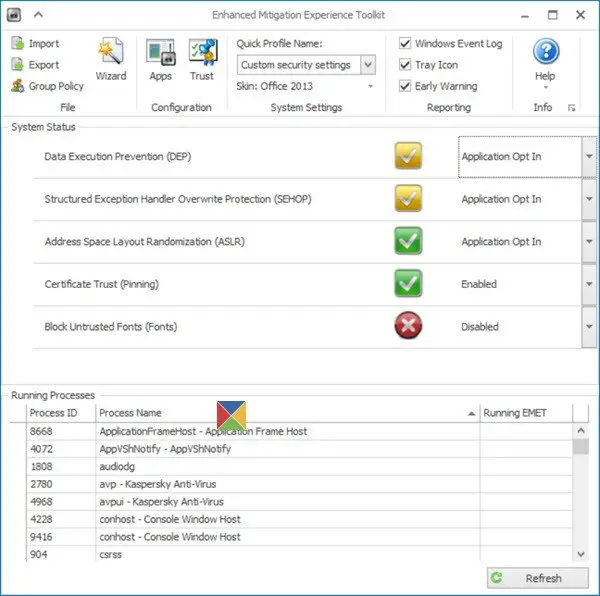
Today, software vulnerabilities and exploits have become a part of life, what with vulnerabilities being found in every commonly used software every other day. Security mitigation technologies can help keep you protected even before the updates are released by the software vendors, as they make it more difficult for an attacker to exploit vulnerabilities. It basically does this by letting users force applications to use key security defenses like Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP). You can use it to protect Microsoft as well as non-Microsoft applications.
The latest iteration of the Microsoft security tool – Microsoft Mitigation Experience Toolkit (EMET) 5.5 is designed to prevent exploits and allow administrators control when third-party plugins should be launched. This is because it has been observed that third-party applications, plugins and programs have become preferred route for attackers since finding vulnerabilities in the Windows OS has become a difficult task. EMET also provides a configurable SSL/TLS certificate pinning feature that is called Certificate Trust. This feature is intended to detect man-in-the-middle attacks that are leveraging the public key infrastructure (PKI).
Applications that are vulnerable to attacks by cybercriminals include Java applications as well as applications from Adobe systems. Enhanced Mitigation Experience Toolkit (EMET) by Microsoft is designed to strengthen the security of non-Microsoft applications by using defense capabilities built within Windows, such as ASLR (Address Space Layout Randomization) and DEP (Data Execution Prevention). This, makes your machine more secure and immune to attacks.
Some features incorporated in Enhanced Mitigation Experience Toolkit (EMET):
- Attack Surface Reduction – Blocks an application’s modules or plugins that might be abused
- Export Address Table Filtering Plus (EAF+) – This new capability added to mitigation tool introduces new methods for intercepting and disrupting advanced attacks. For example, EAF+ adds a new “page guard” protection to help prevent memory read operations, commonly used as information leaks to build exploitations.
- New Blocking Mode – EMET now has a blocking mode that will convey its communication to Internet Explorer to halt an SSL connection if an untrusted certificate is detected without sending session data.
- Improved Certificate Trust feature – Another improvement to EMET deals with digital certificates, which are used to secure a SSL (Secure Socket Layer) connection. It enables a user to block navigation to websites with untrusted, fraudulent certificates, helping protect from Man-In-The-Middle attacks. EMET has also been configured by default to block Adobe’s Flash plugin from being loaded by Word, Excel and PowerPoint.
- Deep Hooks capability – EMET’s Deep Hooks capability helps secure the interactions between an application and the operating system. In EMET 5.0, Deep Hooks is turned on by default. In addition, the default setting is compatible with a wider range of software.
EMET 5.5 includes new functionality and updates, including:
- Windows 10 compatibility
- Untrusted font mitigation for Windows 10
- Improved configuration of various mitigations via GPO
- Improved writing of the mitigations to the registry, making it easier to leverage existing tools to manage EMET mitigations via GPO
- EAF/EAF+ perf improvements
- The updated version of EMET comes with a new feature CFG (Control Flow Guard) which prevents the attempts of code hijacking. It is supported by Windows 8.1 and Windows 10.
- An improved Attack Surface Reduction which might mitigate the powerful exploitation technique VBScript God Mode used in the recent hack attempts. The improved ASR will stop the processes running VBScript extension Internet Explorer’s script engine.
- The Enhanced Protected Mode enabled which further supports alerting and reporting from Modern Internet Explorer and desktop IE.
Installation is so simple!
Once you have downloaded and installed the Enhanced Mitigation Experience Toolkit, you will see a wizard. You have to configure its settings by providing the name and location of the executable file that you want to protect. If you go in for the default recommended settings, then most common programs like Internet Explorer, Oracle Java, Microsoft Office, Adobe, etc. will be protected.
You may use the Recommended Settings, if you do not know what to do. But if you are familiar with the working of the tool, you may Configure it manually, or use Existing settings, if you are upgrading your EMET. If you are a beginner, I suggest you stick with the default recommended settings.
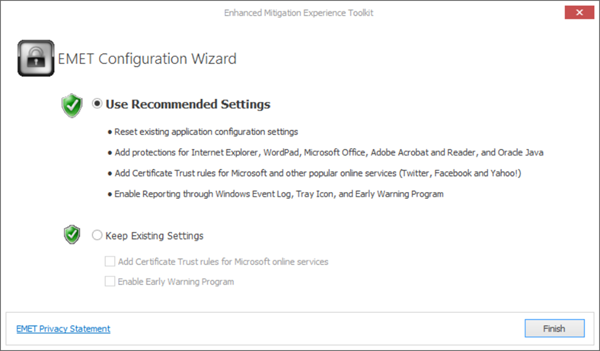
EMET is highly configurable and allows granular plugin blacklisting within applications. It helps harden legacy applications and also verify SSL certificates trust while surfing websites. You will see its notifications being displayed in the taskbar.
EMET free download
The new Microsoft EMET Service is another feature our enterprise customers will find helpful in monitoring status and logs of any suspicious activity. You can download the latest version of Enhanced Mitigation Experience Toolkit from Microsoft. The latest version as on 18th April 2017 is EMET v 5.52.
EMET 5.5 supports Windows Vista, Windows 7, Windows 8, Windows 8.1, Windows Server 2003, Windows Server 2008, Windows Server 2012 – as well as Windows 10. The download also contains a PDF User Guide, which will be very helpful if you plan to deploy EMET on your Windows system.
Don’t let the name scare you away. Microsoft has a penchant for long complicated names. I use the Enhanced Mitigation Experience Toolkit on my Windows 10, and so should you. Just download it, install it, use the recommended settings and make your computer more secure with this free anti-exploit tool from Microsoft!
Good article Anand. I tried EMET 5.2 yesterday on Windows 10 and found that I had to clear EAF and EAF+ to allow Internet Explorer to run. Further investigation into this MS site https://support.microsoft.com/en-us/kb/2458544 that describes the various EMET versions and which versions of Windows are required. EMET 5.2 is not supported on Windows 10 but EMET 5.5 Beta is supported. I installed the 5.5 Beta version and it works out of the box, i.e. no changes are required.
“Sorry, the page you requested cannot be found” is all I get when trying to download.
It was working for me. Anyway, here is its direct download link: https://www.microsoft.com/en-us/download/confirmation.aspx?id=50766
Thank you, that worked.
does it block pirated software?
and thank you