Do you have issues with Secure Boot and notice Event ID 1032 with an error message The Secure Boot update was not applied due to a known incompatibility with the current BitLocker configuration? If so, this post will help you resolve the issue.
Event ID 1032, The Secure Boot update was not applied due to a known incompatibility with the current BitLocker configuration
This event is generally logged when conflicts arise between the computer’s boot security system, Secure Boot, and the hard drive’s encryption system, Bitlocker.
In UEFI-based firmware systems, when Secure Boot tries to update its recognition system, it may interpret the Bitlocker as a potential security threat. This forces Bitlocker to enter recovery mode, leading to the abovementioned event in the log entry.
Meaning of Event ID 1032
In simple terms, Secure Boot can be considered a firmware-based guard for the computer. It allows only authorized or trusted software to be executed during the booting phase. It validates the applications by comparing the software’s digital signature to a predefined set of keys stored in the UEFI.
This set of predefined keys is stored in the Secure Boot DB or database. However, the firmware also maintains a database of keys or signatures not authorized to run on the platform in a Security Boot Forbidden Signature Update Database or DBX.
Through the KB5012170 Security Update, Microsoft has updated the DBX database to enhance the system’s security.
Resolution to Event ID 1032
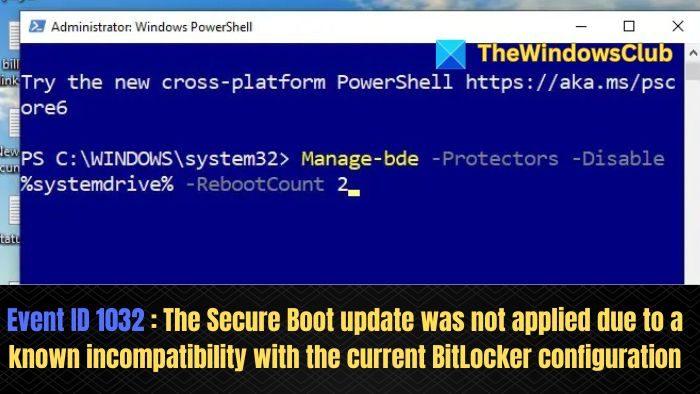
To resolve the issue, Bitlocker can be suspended for 2 restart cycles, allowing KB5016061 to install. The following steps can be executed to temporarily suspend Bitlocker:
- Open Windows Terminal as an Administrator.
- Enter the below-mentioned command at the Terminal prompt:
Manage-bde –Protectors –Disable %systemdrive% -RebootCount 2
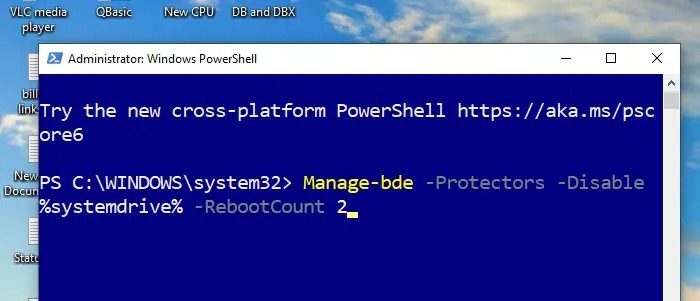
In the above command:
Manage-bde: is the command-line tool for managing Bitlocker Drive Encryption (BDE).
Protectors: specifies that we want to manage the passwords, keys, etc., also known as Protectors used in Bitlocker encryption.
Disable %systemdrive% -RebootCount 2: Disables the Bitlocker encryption for the system drive or C: for 2 reboots before it starts the decryption process.
The two reboots window allows us to ensure a secure backup of the recovery key before the decryption process starts. In short, 2 reboots can be regarded as a safety option to prevent any data loss as the system rushes through disabling the Bitlocker.
- Enter the below-mentioned command to ensure that the Bitlocker protection is active again after the system is restarted twice:
Manage-bde –Protectors –enable %systemdrive%
- Check to see if the above error is logged again.
I hope the post was easy to follow and that you were able to resolve the issue.
Leave a Reply