You may often come across the Event ID 4624, An account was successfully logged on message in the Event Viewer during your routine audit. However, there’s nothing to worry about since this is a regular Windows security log generated whenever you successfully log into the computer. So, if at any time you need to check the user login history, you need to look for the Event ID 4624.
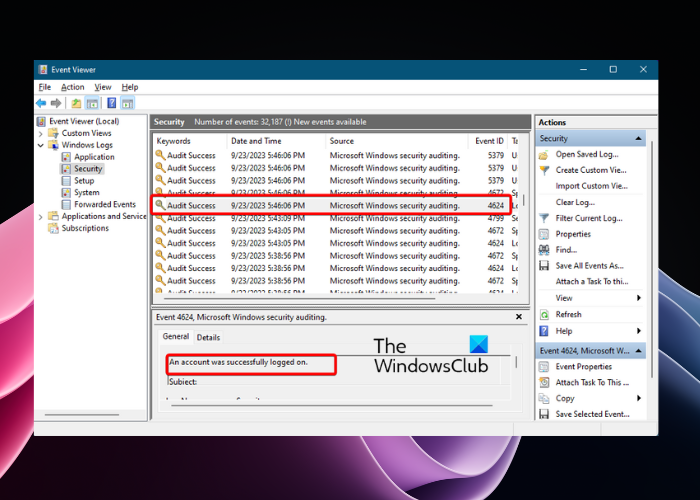
However, it can be a concern if an account does not appear familiar to you or if you suspect that your account may have been hacked. In such a case, you need to review the Windows Security Log in the Event Viewer properly to identify any threats and eliminate them accordingly.
Event ID 4624, An account was successfully logged on
Having said that, we have a detailed guide to help you understand everything about Windows Event ID 4624 and how to detect any problems.
What is the 4624 Event ID?
Event ID 4624 in the Windows Event Log indicates every successful login session on the destination computer. This audit setting generates on the machine you accessed and where you created the session. So, if anyone is snooping around on your computer, this is the Event ID you need to look for.
Besides, this is a piece of highly valuable information that tells you exactly who (user) logged on and from which account. For this, you can check the New Logon field that shows the following details:
- Security ID
- Account Name
- Account Domain
- Login ID
However, we will also explain the other properties related to Event ID 4624 below.
Note – You can configure this audit setting in the Local Security Policy or Group Policy Editor (gpedit.msc). Then, you can alter the auditing options to observe successful login attempts for security purposes. However, these settings can only record events on the local computer and not on the domain controller.
Windows Event ID 4624 properties
You can find the properties of an Event ID under the General tab. Here, you will find the below fields:
1] Subject
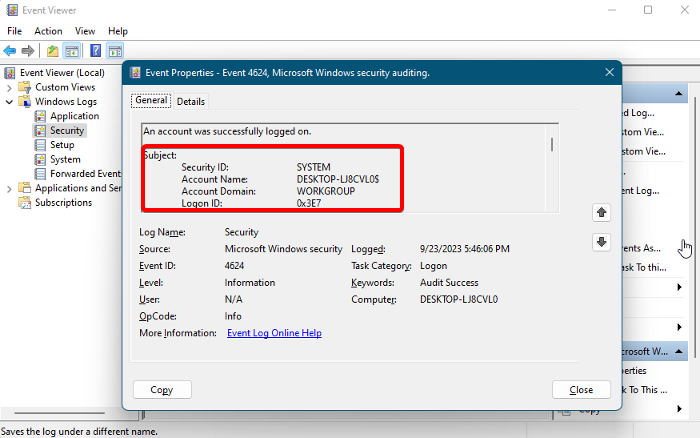
Security ID (SID):
It denotes that there was a successful login.
Account name
Name of the account that recorded a successful login. This helps you to identify if it’s a legitimate account.
Account Domain
The domain of the account/the computer name that recorded the event is useful for troubleshooting.
Logon ID
Denotes a hexadecimal value that can be helpful to associate this event with any of the recent events that may have the same Logon ID. Moreover, it also helps you identify any issues with the events and troubleshoot accordingly.
Read: How to disable Windows Event Log
2] Logon Information
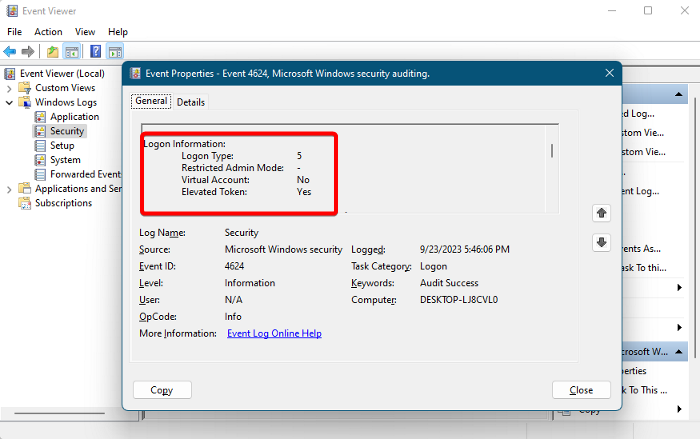
This property includes the following:
Logon Type
| Logon Type | Logon Title | Description |
|---|---|---|
| 0 | System | Used solely by the System account, such as, during the system startup. |
| 2 | Interactive | A user logged on to this computer. |
| 3 | Network | A user or computer logged on to the current workstation from the network. |
| 4 | Batch | Used by batch servers, where processes may be running on behalf of a user without their direct involvement. |
| 5 | Service | A service was started by the Service Control Manager. |
| 7 | Unlock | This computer was unlocked. |
| 8 | NetworkCleartext | A user logged on to this computer from the network. The user’s password was then passed to the authentication package in its unhashed form. The built-in authentication packages all hash credentials before sending them across the network. The credentials do not traverse the network in plaintext (also called cleartext). |
| 9 | NewCredentials | A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity but uses different credentials for other network connections. |
| 10 | RemoteInteractive | A user logged on to this computer remotely using Terminal Services or Remote Desktop. |
| 11 | CachedInteractive | A user logged on to this computer with network credentials that were stored locally on the computer. The domain controller was not contacted to verify the credentials. |
| 12 | CachedRemoteInteractive | Same as RemoteInteractive. This is used for internal auditing. |
| 13 | CachedUnlock | Workstation logon. |
*Data courtesy – Microsoft
Restricted Admin Mode
You only see this when a user successfully logs on remotely via the Terminal Services or Remote Desktop. The value of Restricted Admin Mode is a boolean, that is, Yes or No.
Virtual Account
Again, the value of a Virtual Account is either a Yes or No. This indicates whether the account that documented the successful logon is a virtual account or not. For example, Managed Service Account.
Elevated Token
This is again a Yes or No field, denoting whether the account that initiated the successful logon (event ID 4624) is an admin account or not.
3] Impersonation Level
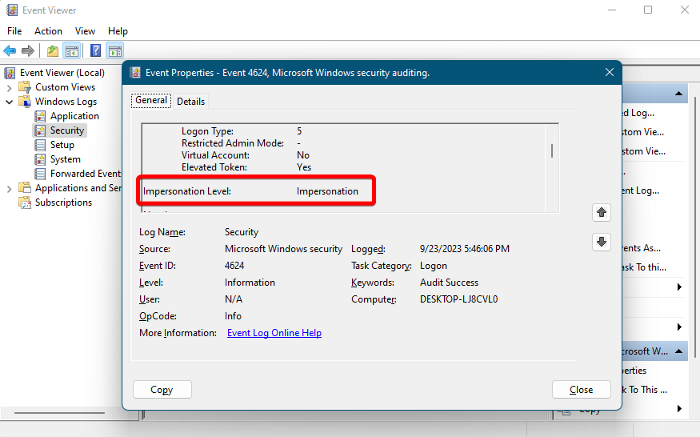
This field indicates how much a process in the login session impersonates (simulates). It’s the level of authority permitted by the server to mimic a client on his behalf. The 4 different levels are Anonymous, Identification, Impersonation, and Delegation.
Read: The security log is now full (Event ID 1104)
4] New Logon
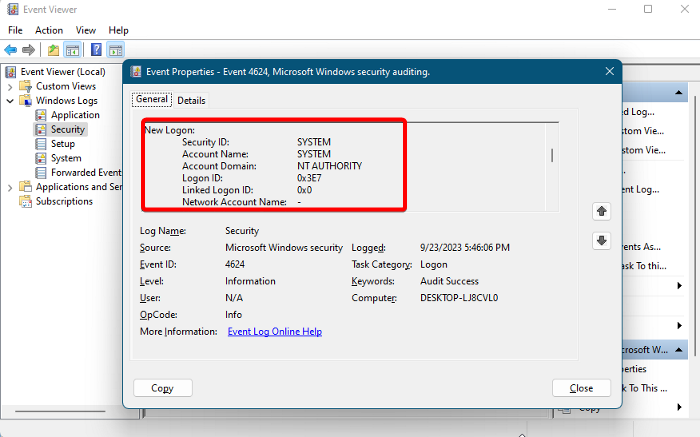
This is the account that actually logged on and for which the logon session was created. You can compare the computer name with the account domain to identify if it’s local or domain. If it matches, it’s local; if not, then it’s the domain account.
Furthermore, it’s divided into two categories: Account and Network Information:
Account Information
- Security ID – SID that recorded the successful logon of the Windows Security Event ID 4624.
- Account Name – Carries out the successful logon.
- Account Domain – The domain name could be in either of the following formats: NeTBIOS name of the domain, in lowercase, or in uppercase formats. But if the Account Domain shows NT AUTHORITY, it means that the logon account is a LOCAL SERVICE or ANONYMOUS LOGON.
- Logon ID – It displays a hexadecimal value that’s useful for troubleshooting.
- Linked Logon ID – Again a hexadecimal value relative to the Logon session. If there are no related logon events, the value is 0x0.
- GUID – Allows you to link two events one of which is the Event ID 4624 and the other with the same GUID, thus, helping you to identify a potential threat.
Network Information
- Network Account Name – Only relevant to the NewCredentials logon type, however, if the logon type is something else, then the Network Account Name is documented as “–“.
- Network Account Domain – Only applicable to the NewCredentials logon type. If the user wants to create a network connection, they will need to use the domain name as specified in this field. But if the logon type is something else, it would be recorded as “–“.
5] Process Information
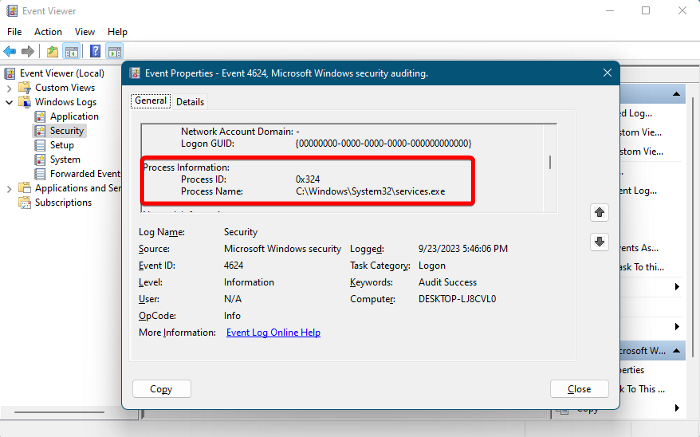
This field provides details regarding the process that documented the successful logon event.
- Process ID – It displays a hexadecimal value that Windows and other OS use to identify a process exclusively. To view the Process ID of all processes that are currently running on your Windows PC, launch PowerShell, run the Get-Process command and hit Enter. Now, change the hexadecimal value of the Process ID into decimal in the event ID 4624. This helps you to compare the process ID to one of the IDs generated by the Get-Process PowerShell command.
- Process Name – Documents the successful logon.
Read: Event ID 1101, Audit events have been dropped by the transport. 0
6] Network Information
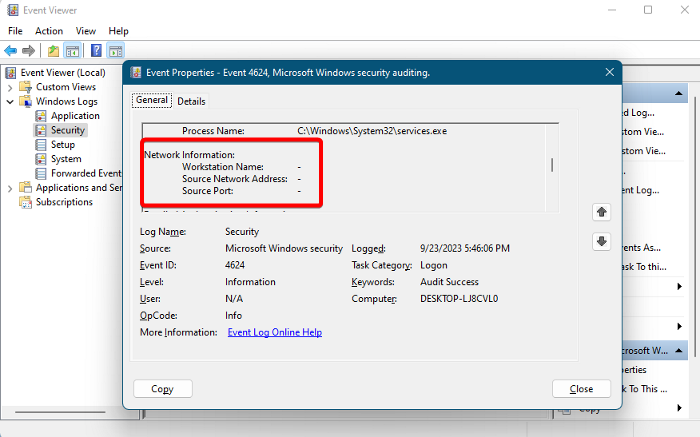
This section offers you important information related to troubleshooting purposes. For example, which computer the user logged in from, the IP address of the PC and the port used.
- Workstation Name – Documents the PC name from which the user logged in.
- Source Network Address – Registers the IP address of the PC from which the user logged in.
- Source Port – Records the original TCP port of the remote machine which was used to log in.
7] Detailed Authentication Information
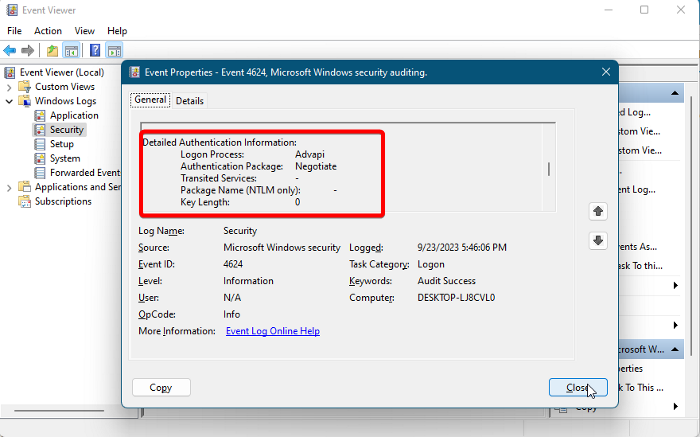
This field represents how the authentication process is initiated. It maintains a record of the process in which the authentication and the package was used. It also shows other details like Transited Services, Package Name, and Key Length.
- Logon Process – It displays the name of the authenticated logon process the user used to logon when the system recorded the Windows Event ID 4624.
- Authentication Package – Registers the authentication package type that was used to logon to this computer.
- Transited Services – Shows only transmitted services (for only Kerberos).
- Package Name – It documents the NTLM version if the logon request was authenticated by the NTLM protocol.
- Key Length – Only applicable for NTLM authentication Protocol. For others, the field returns 0.
In addition, for Event ID 4624, Microsoft has some additional recommendations for the type of monitoring required based on the situation.
What is Event ID 4625?
Event ID 4625 registers whenever the user fails to log in to a local computer. This event is populated on the device from where the user tried to log in. Moreover, to identify failed logons, you can create a PowerShell script that can help you find the Windows Event logs with the Event ID 4625.
What is Event ID 4634?
Event ID 4634 indicates that an account was logged off. This means that whenever a logon session is ended (logged out), Event 4634 is generated. However, this differs from the Event ID 4647, which denotes that a user started the logoff. In this case, it simply registered that a session is no longer running and has ended.
Leave a Reply