Imagine … The FBI checked your computer and browsing traffic. It now has details of all sites you visited and what you did using your computer. And it knows more laws than you ever thought existed. When you open your browser, instead of your homepage, you get a notice from the FBI saying you violated so and so laws. Further, you have to pay a fine of $350 to avoid jail. That does look genuine, right? It is not, however. It is just the FBI Ransomware that is still doing rounds, and you can do little to remove the ransomware virus. I managed to get a copy of the browser screen lock of the FBI malware. Click on the image below to enlarge it.
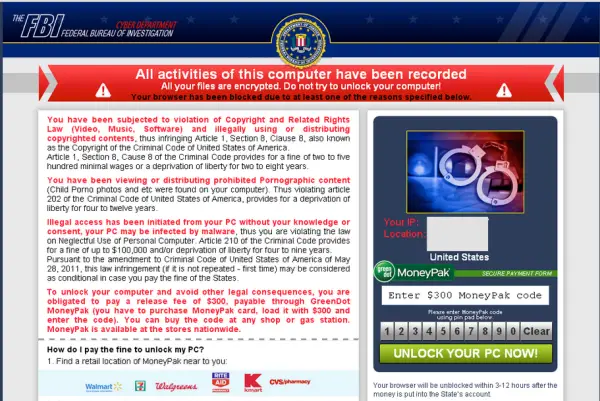
FBI Ransomware
The ransomware has had many preys. It has been successful in getting people to pay up the $350 it demands as fine for your supposedly “illegal” browsing habits. And, it does not stop there. It demands an additional fee of $450 to remove your “criminal” records from its database so that you are not fined again. What would you do in such circumstances? Panic, and pay off the additional money too?
Many have done that, and many will continue to do so until it occurs to them that they could get a confirmation from the local police station that the FBI is indeed asking for criminal browsing and record deletion fee. Else, simply write to the FBI asking you got such a message and ask whether it is indeed true.
How to Identify Ransomware
Ransomware and phishing malware have always counted on the fear of law and society within individuals. You might have noticed you get mail from Microsoft, Yahoo, and other biggies in your Outlook that promise you direct placements. When you take a closer look at the email ID, it has nothing to do with the companies and thus, reveals that it is a phishing attempt.
For example, I often receive emails from different subdomains of wisdomjobs.com with names of bigger corporations: microsoft@wisdomjobs.com is not Microsoft and can NEVER be as Microsoft has its own widely used domain called microsoft.com. Likewise, something like paypal.info@xyz.com will NEVER be PayPal as the main domain is not PayPal as evident from the email ID.
In the case of FBI ransomware, you can just check the address in the browser’s address bar. Find out the last word just before .com/.net/.org etc. You will notice that the first two subdomains are FBI and GOV while the others are different domains that are not even remotely related to – forget FBI, – any of the federal or state agencies.
Who is Behind FBI Ransomware
The cybercrime cell is investigating from what I know. What makes it hard is that it won’t accept the general methods of paying by credit cards directly to the agency or state units. You pay to different accounts and in most cases, you have to pay the money in parts. That is, you paid $350 to account number XYZ, $200 to acct number ABC, and the balance to another account. All these accounts are fake and are emptied, closed as soon as money is transferred. Thus, the scope of narrowing down the search of this FBI ransomware racket/gang goes down. As of now, no one except the people involved in running the gang, know about who is operating it. Whoever it is, the person is pretty smart to keep the cyber police on their toes.
Remove FBI Ransomware
As of now, the only sure-shot method to eliminate the FBI ransomware virus is to clean format your system drive and reinstall the operating system. That done, increase your Firewall protection by using a hardware firewall as far as possible. These days, all modems and routers come with firewall firmware. Log into your router/modem page and enable the firewall. You may then decide whether or not to use an additional software firewall.
I am told using image backups of the system does not work. That is, if you are infected with this malware and you go restore an older system image, it does not provide any relief. If you have heard or used any effective method to eliminate the FBI ransomware virus, please share with us for the benefit of all.
HitmanPro.Alert is a free Ransomware Protection & Browser Intrusion Detection Tool. CryptoPrevent is another handy tool that provides your computer a shield against Cryptolocker or any other kind of ransomware. Anvi Rescue Disk for Windows will assist in ransomware removal. HitmanPro.Kickstart will help remove Ransomware.
First off, there are all kinds of instructions available from many credible sources on “how to remove FBI Ransomware”. And NONE of them include formatting your hard drive and reinstalling everything.
Although, with some ransomware, even when the malware is otherwise comparatively “stunned” or removed by AV/manually, the disk(s) remain(s) encrypted with keys that cannot be broken; in such cases, of course clean reinstalling the OS is necessary…restore points can’t interface with encrypted files.
HitmanPro Alert and CryptoPrevent speak to those with any Windows OS version which doesn’t have a group policy editor (where one can access local security setting beyond firewalls and specifically block certain types of activity on one’s own at the file system level).
I understand from its developer’s site that CryptoPrevent free version is a one-shot install of alleged “artificial gpe settings” which keep a user safe from CryptoLocker and similar malware…but if one wants to be able to add to such type of protection as malware evolves, one must buy (a seemingly small price) the “pro” version of CryptoPrevent to get new “artificial gpe” additions.
I have been using HitmanPro Alert 2.5.1 beta since its release the other week, on a 64 bit Windows 7 Home Premium SP1 updated re OS/everything on it to current (including Javascript jre,.Net framework 4.5, and other runtime stuff like Visual Studio); HitmanPro alert beta seems to be working just fine across Comodo Dragon and IE11 for Windows 7; the only perceivable issues I face are that Keyscrambler (which outputs random characters re loggers) isn’t allowed to run by the Alert beta, and this beta also impedes operation of my HP Officejet 6700 scan-to-computer function; other than that all seems well; there is no “off” or “pause” or “make exception” utility in HitmanPro Alert beta, so I would have to remove/reinstall it if I wish to scan to PC; I don’t find much yet about how HitmanPro will go about use/updates once out of beta.
Hope this info helps somebody somehow; thanks for another great report!
Thank you for sharing the above. I too, will try Hitman Pro. :)
I would want to check out those credible sources. As far as I know, most antimalware have failed to remove the FBI ransomware that takes control of your operating system in a way that it triggers on “http open” event. That could be also achieved using an eye on all the ports of the infected computer for outgoing data packets. It won’t send you an email if you don’t open browser and manage to open Outlook instead (never came across such report).
Anyway, the above is my opinion. If there are options, people may go for them. I would – however – for maximum security, format and reinstall the OS.
I have removed it from, literally, a couple of thousand customer computers and not once has it ever required formatting the hard drive. Not only is your information about 3 years out of date….it is completely inaccurate.
I can’t work after such an attack assuming that all is well. If I am affected with such malware, I will certainly clean install the OS – just to make sure there are no traces left that are collecting and sending my data to someone somewhere. “Better safe than sorry” is my point of view and yes, it is quite old but trusted information.
Only thing worse than an out of date and inaccurate article about
computers…is an inaccurate comment giving piss poor advice about
computers.
Not a single variant of the FBI ransomer encrypts the victims files. In fact, there is only one known malware that encrypts files, cryptolocker…and it is extremely easily remove from the infected system WITHOUT formatting the drive, but there is no way to decrypt the files. Lost files must be restored using a secondary backup such as a flash drive or DVD.
CryptoPrevent works well to prevent cryptolocker infections…and DOES NOT require use of the paid version. The free version DOES OFFER FULL PROTECTION.The ONLY difference in the free version and the Pro is that the free version does not offer an auto-update function.
HitmanProAlert beta…is a completely useless piece of bloat ware that offers absolutely no protection against crytptolocker or the FBI ransomware variants. You would be better off using a higher quality of junk software like Norton.
I would like to see your sources, Jim. Criticizing is good but then, please provide material supporting your criticism. I already said I won’t be able to work on a computer that has been
compromised. And that is the reason I will go for a clean reinstall of
the OS. Now, let’s see your reasons!
You say article is outdated, HitmanPro is useless and Norton is junk etc. I understand you do not like them. But is there a valid reason for your comments? If yes, may we have the links and material supporting your views.
Honestly, I’ve cleaned this malware off of a lot of people’s computers also.
I used Kaspersky Rescue Disc and got rid of the old variants. The newer ones I manually went into the Program Data and removed it, using either Ubuntu Live CD or Hiren’s Boot CD.
Kaspersky Rescue Disc is an amazing piece of software.
I read on BitDefender that the following files are to be removed:
C:Documents and SettingsStart MenuProgramsStartup ctfmon.lnk
C:Documents and SettingsStart MenuProgramsStartup.lnk
C:UsersAppDataRoamingMicrosoftWindowsStart MenuProgramsStartup ctfmon.lnk
C:UsersAppDataRoamingMicrosoftWindowsStart MenuProgramsStartup .lnk
C:UsersAppData.exe
C:Documents and SettingsLocal SettingsTemp.exe
C:UsersAppDataRoaming.exe
C:Program Datalsass.exe
C:Program Data.exe
That is, once you boot into safe mode or boot through a boot disk of Reflect etc. The only thing is convince self that the malware is gone. If you can, it is fine else go ahead and perform a clean reinstall.
Thank you, for sharing the information.
Most welcome, AK! BTW, Alert beta doesn’t interfere with my MS security features or any of the other layered security softwares…and Zemana antilogger, outputting blank anyway, isn’t affected in operation…just anti-loggers outputting scrambled.
Mr. Boyd, thanks for letting me know that when I say CryptoPrevent free version doesn’t auto-update but paid does, I’m giving “piss-poor info” but when YOU say the identical about it we’re at the feet of the Master…you didn’t say I was “piss poor” about most ransomware blockers working at the gpe level rather than file system itself, or that Win7 Home doesn’t have gpe to protect users. Probably why my clients aren’t known for catching too many infections TO be removed in the first place…I’m not as intellectually remote as haters would opine. I prepare as possible for more when say a “Zeus” is the only banking bot, and before all the other bots say Kaspersky’s TDSS Killer now scans for exist…one gets going, they morph and then more strains catch on. Could be why “heuristics”/”zero day” are such buzzwords in AV today.
Krebs On Security this month on topic Cryptolocker said it can silently install drive-by style even if all routine AV/OS up to date; I myself last week said IF one has VSS enabled AND a new strain of Cryptolocker, as referenced in Bleeping Computer’s “CryptoLocker Ransomware Information Guide and FAQ”, HASN’T disabled previous versions, files might be restored simply by (if one by one) right-clicking file Properties and returning to previous versions, or perhaps using restore points especially if backed up apart from encrypted drives. But if Cryptolocker shuts off backups… .
The point seems to be not who’s the smartest person in the universe, myself included, or who handles the most corporate WANs, but in protecting everyday consumers with a minimum of trauma to their learning curve, time, and budgets. In that regard, unless credible industry tests can show HitmanPro Alert beta doesn’t protect against Cryptolocker and other types of spyware/malware as it claims at its site and therein included video, or that it will seriously interfere with most consumer users, it cannot simply be yelled, foot-stomped, commanded, willed or wished into being a bad recommendation for consumers to check into as an option.
As far as I’m concerned, what would I need to say further in my defense? I just believe that when something WE see as ultra-simple to fix visits many people who DON’T know how to prevent or fix it, and they actually pay ransom or us to get OS/files back, it seems bad form to accept money in either case.
The FBI rasomware has been around for more than 3 years now. It is not necessary to format the HDD to get rid of it as it can be easily removed manually and there are several tools available for automated removal …easily confirmed with a simple Google research.
Hitman Pro has been around a very long time, and you will not find a single credible source that will tell you it can prevent either the FBI or Cryptolocker ransomwares…again do a little research and you will get your confirmation.
Really? I have talked people through the removal procedure over the phone…people who know nothing about virus removal or any other form of computer repair, and even they managed to remove the FBI bug without any issue.
Seriously…with 90% of the cases involving the FBI bug, simply restarting in safe mode and running SuperAntiSpyware resolves the problem in a matter of minutes. With some of the variants, removal is a little more complex…but formatting is still not necessary.
I have serviced computers professionally for 27 years…and in my experience, anyone who suggest formatting a drive “as the only sure-shot method” to solve a problem…simply does not know how to do anything else.
Formatting is ALWAYS a LAST RESORT for any true computer professional.
Your admitted lack of ability to defeat this simplest of computer
bugs any other way…seriously disproves your qualifications to offer advice on this matter into
question.
I removed my browser and all related files, then reinstalled and the ransomeware was gone.
hey romove virus from internet site can u unblocked
I didn’t make nothing wrong in the world to block my internet site for nothing u shy to blame who is watch to put bad stuff on internet why u leave it to put internet what is not good to watch