Windows Security Team has rolled out Tamper Protection for all Windows users. In this post, we will share how you can enable or disable Tamper Protection in Windows Security or Windows Defender via UI, Registry, or InTune. While you can turn it off it, we highly recommend you keep it enabled at all times for your protection.
What is Tamper Protection in Windows 11/10
In simple English, it makes sure nobody can tamper with the Protection system, aka Windows Security. The onboard software is good enough to handle most of the security threats, including Ransomware. But if it is turned off by third-party software or malware that sneaks in, then you can get into trouble.
Tamper Protection feature in Windows Security prevents malicious apps from changing relevant Windows Defender Antivirus settings. Features like Real-time protection cloud protection are essential to keep you safe from emerging threats. The feature also makes sure that nobody can change or modify the settings via Registry or Group Policy.
Here is what Microsoft says about it:
- To help ensure that Tamper Protection doesn’t interfere with third-party security products or enterprise installation scripts that modify these settings, go to Windows Security and update security intelligence to version 1.287.60.0 or later. Once you’ve made this update, Tamper Protection will continue to protect your registry settings and will log attempts to modify them without returning errors.
- If the Tamper Protection setting is On, you won’t be able to turn off the Windows Defender Antivirus service by using the DisableAntiSpyware group policy key.
Tamper Protection is enabled by default for Home users. Keeping Tamper Protection On doesn’t mean that you cannot install third-party antivirus. It only means no other software can change the settings of Windows Security. Third-party antivirus will continue to register with the Windows Security application.
Disable Tamper Protection in Windows Security
While third parties are blocked from making any changes, you, as an administrator, can make the changes. Even though you can, we will highly recommend you to keep it enabled all the time. You can configure it in three ways:
- Windows Security UI
- Registry changes
- InTune or Microsoft 365 Device Management portal
There is no Group Policy Object to change this setting.
1] Using Windows Security UI to disable or enable Tamper Protection
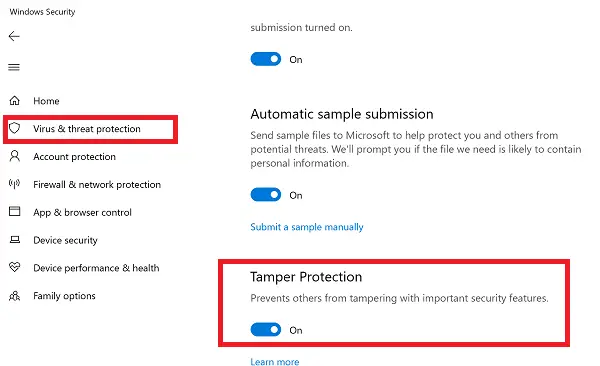
- Click on the Start button, and from the app list, locate Windows Security. Click to launch when you find it.
- Switch to Virus and Threat protection > Manage Settings
- Scroll a bit to find Tamper Protection. Make sure its toggled On.
- If there is a particular need, you may turn it off, but make sure to turn it on again when work is done.
2] Registry changes to disable or enable Tamper protection
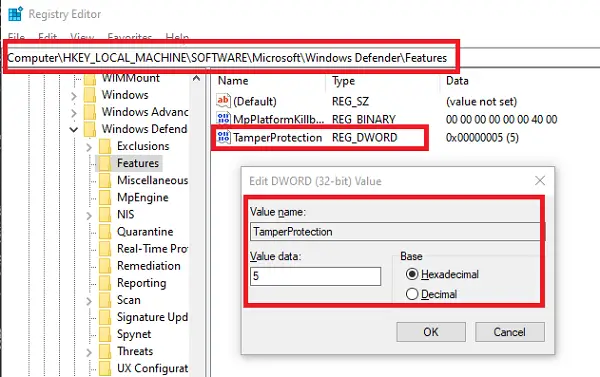
- Open Registry Editor by typing Regedit in the Run Prompt followed by the Enter key
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Features
- Double-click on DWORD
TamperProtectionto edit the value. - Set it to “0” to disable Tamper Protection or “5” to enable Tamper Protection
3] Turn Tamper Protection on or off for your organization using Intune
If you are using InTune, i.e. Microsoft 365 Device Management portal, you can use it to Turn Tamper Protection on or off. Apart from having appropriate permissions, you need to have the following:
If you are part of your organization’s security team, you can turn Tamper Protection on (or off) for your organization in the Microsoft 365 Device Management portal (Intune), assuming your organization has Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP):
- Your organization must have Microsoft Defender ATP E5, Managed by Intune, and running Windows OS 1903 or later.
- Windows security with security intelligence updated to version 1.287.60.0 (or above)
- Your machines must be using anti-malware platform version 4.18.1906.3 (or above) and anti-malware engine version 1.1.15500.X (or above)
Now follow the steps to enable or disable Tamper Protection:
- Go to the Microsoft 365 Device Management portal and sign in with your work or school account.
- Select Device configuration > Profiles
- Create a profile that includes the following settings:
- Platform: Windows 10 and later
- ProfileType: Endpoint protection
- Settings > Windows Defender Security Center > Tamper Protection. Configure it on or off
- Assign the profile to one or more groups
If you do not see this option right away, it is still being rolled out.
Whenever a change occurs, an alert will be displayed on the Security Center. The security team can filter from the logs by following the text below:
AlertEvents | where Title == "Tamper Protection bypass"
No Group Policy Object for Tamper Protection
Lastly, there is no Group Policy available to manage multiple computers. A note by Microsoft clearly says:
Your regular group policy doesn’t apply to Tamper Protection, and changes to Windows Defender Antivirus settings will be ignored when Tamper Protection is on.
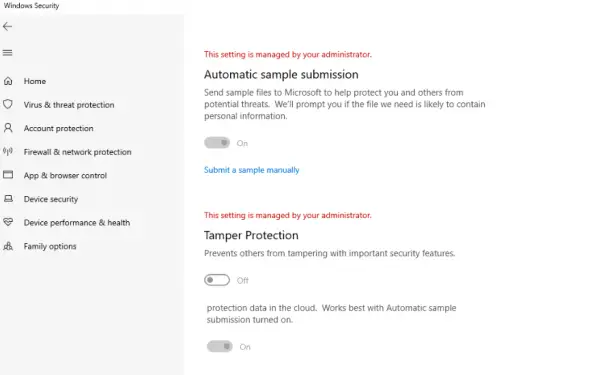
You can use the Registry method for multiple computers by remotely connecting to that computer and deploying the change. Once done, this is how it will look in users individual settings:
We hope the steps were easy to follow and that you could enable or disable Tamper Protection as required.
Tamper Protection, This setting is managed by your administrator
If you see This setting is managed by your administrator message for Tamper Protection, you could enable Tamper Protection using Registry, remove the DisableAntiSpyware Registry entry, or use Microsoft Intune to resolve the issue. Contact your system administrator if this does not help.