A cybersecurity risk assessment evaluates threats to your organization’s IT systems and data and identifies opportunities for improvement in information security programs. It also helps companies communicate risks to other users and make informed decisions about deploying resources to mitigate security risks. In this post, we will discuss how to perform a Cybersecurity Risk Assessment.
Perform Cybersecurity Risk Assessment
There is no right and wrong way to perform a Cybersecurity Risk Assessment, however, we are going through a simple route and lay down a step-by-step guide on how to assess your environment.
Follow the steps mentioned below to assess your organization’s cybersecurity prowess.
- Separate your assets based on their criticality
- Assess and analyze the risk
- Add tools and security controls
Let us discuss them in detail.
1] Separate your assets based on their criticality
The first crucial step is to classify your assets based on their criticality to your business. Imagine building a security wall around your most valuable resources.
This approach ensures that most resources are allocated to protect the most important data. It’s essential to establish a clear standard for determining asset importance, taking into account factors such as legal implications, potential financial penalties, and overall business value. You need to draft an information security policy that adheres to a standard that you have set where each asset should be classified as critical, major, or minor based on its importance.
2] Assess and analyze the risk
Certain types of information are more sensitive than others. Not all vendors offer the same level of security. Therefore, after identifying the information assets, it is crucial to evaluate their associated risks and the overall enterprise. So, you need to take into account system, network, software, information, devices, data, and other related factors into account when accessing the risk
Next up, you need to analyze the risk. Where you need to score based on the Probability of the occurrence and Impact. Based on this, you can decide which screw to tighten first. So, for example. if you are managing a data warehouse that stores public information, you will most probably allocate fewer resources to secure it as the information is inherently public. Whereas, if you are managing a database that has customer health information, you will try to integrate as many security screws as possible.
3] Add tools and security controls
Next, it’s crucial to define and implement security controls. These controls are vital for effectively managing potential risks by either eliminating them or significantly reducing the chance of occurrence.
Controls are indispensable when it comes to addressing every potential risk. Therefore, the entire organization must implement and ensure that risk controls are continuously enforced.
Now, we will discuss some of the risk assessment tools that you must use.
- NIST Framework
- Network Security Assessments
- Vendor Risk Assessment tool
Let us talk about them in detail.
1] NIST Framework
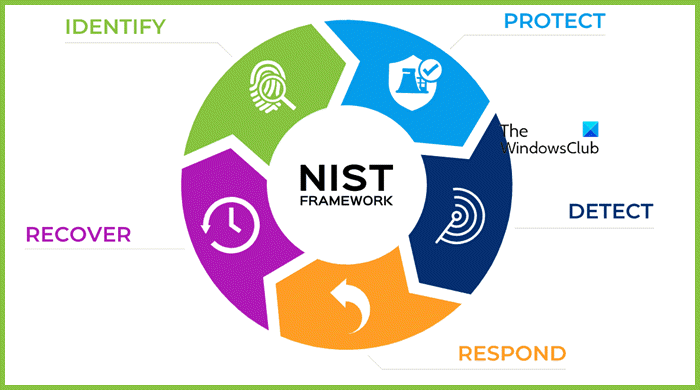
The NIST Cybersecurity Framework is a process for monitoring, assessing, and responding to threats while maintaining data security. It offers guidelines for managing and reducing cybersecurity risks and improving communication about cyber risk management. It identifies the threat, detects it, protects your assets from it, responds, and recovers when needed. It is a proactive solution that allows you to tweak and set your organization’s cybersecurity approach. Go to nist.gov to learn more about this framework.
2] Network Security Assessment Tools
A network security assessment is like a check-up for your network’s security. It helps find weaknesses and risks in your system. There are two types of assessments: one shows weaknesses and risks, and the other simulates real attacks. The goal is to find potential entry points for expensive cyberattacks, whether they come from inside or outside the organization.
There are a few tools that can help you in Network Security Assessments such as NMAP and Nikto.
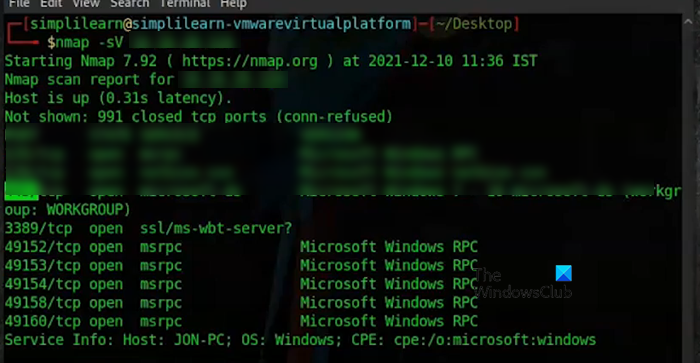
Let us first talk about NMAP. It is an open-source free security scanner, port scanner, and network exploration tool. It identifies and removes devices, firewalls, routers, and open and vulnerable ports, and assists in network inventory, mapping, and asset management. Go to nmap.org to download and use this tool.

NIKTO is another open-source tool that scans your website and jots down potential security vulnerabilities. It searches and finds loopholes, misconfigured uploads, and other errors in the script. You download Nikto from github.com.
3] Vendor Risk Assessment tool
You should not just think about the security of your organization, but also that of your vendor. Vendor Risk Management (VRM) tools help identify, track, analyze, and mitigate potential risks in third-party relationships. Third-party Risk Management Software ensures smooth onboarding and thorough due diligence.
To assess the risk from your vendors, you can use VRMs such as Tenable, Sprinto, OneTrust, BitSight, and more.
Read: What are the Best Cybersecurity Practices for Small Business?
What are the 5 steps of security risk assessment?
The five risk management steps include determining the scope of the assessment, identifying threats and vulnerability, analyzing risk and impact, prioritizing risk, and documenting it. However, if you want to know more about this in detail, and just want a basic guide on how to do risk assessment, check out the guide above.
Read: Cybersecurity threats you should take note of
What is the risk assessment matrix for cybersecurity?
The 5×5 risk assessment matrix has five rows and columns. It categorizes risks into 25 cells based on severity and likelihood. You can and should make a 5×5 matrix when doing your risk assessment.
Also Read: Microsoft Cybersecurity Awareness Kit offers employee training simulations.