Most of the web services that require a login have a specified number of consecutive invalid login attempts allowed, after which you are restricted from further login attempts for a certain time period. This is to prevent a hacker from guessing your password by entering random characters continuously.
Restrict number of Login attempts in Windows 11/10
With the use of Local Security Policy, you can easily implement this feature in Windows 11/10, via the Local Security Policy. Do note that the Local Security Policy is only available in select versions of Windows.
To implement this security measure in your Windows 11/10/8/7, type Local Security Policy in the search box in the Start menu and press Enter.
Read: Most important Group Policy settings for preventing Security Breaches
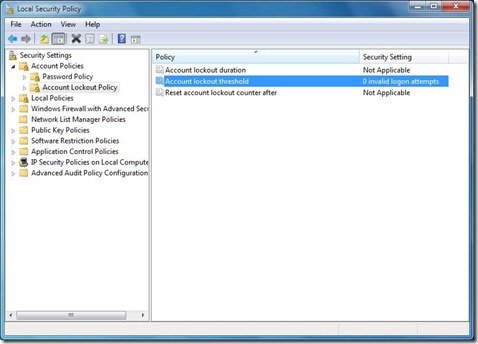
Account lockout threshold policy
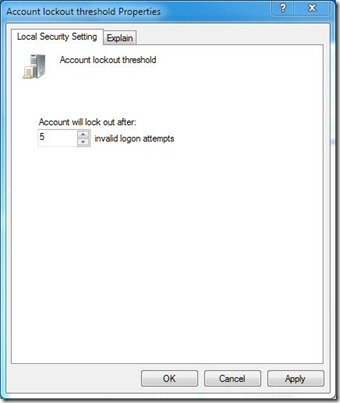
Now in the LHS pane, select Account Lockout Policy from under Account Policies as shown below. Double-click Account Lockout Threshold.
The Account lockout threshold security setting determines the number of failed logon attempts that causes a user account to be locked out. A locked-out account cannot be used until it is reset by an administrator or until the lockout duration for the account has expired. You can set a value between 0 and 999 failed logon attempts. If you set the value to 0, the account will never be locked out.
Now select the number of invalid login attempts after which you want to lock the computer. Click OK.
Account lockout duration policy
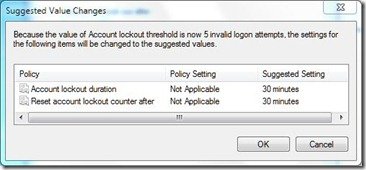
Next Windows will notify you that Account lockout duration and Reset account lockout counter will be set to default. You can either choose the default value or change it later. After you are done, click OK.
The Account lockout duration security setting determines the number of minutes a locked-out account remains locked out before automatically becoming unlocked. The available range is from 0 minutes through 99,999 minutes. If you set the account lockout duration to 0, the account will be locked out until an administrator explicitly unlocks it. If an account lockout threshold is defined, the account lockout duration must be greater than or equal to the reset time.
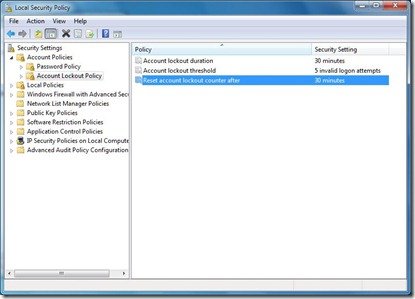
To change the default values of the above-mentioned settings, just double-click the setting that you want to change and set the desired value.
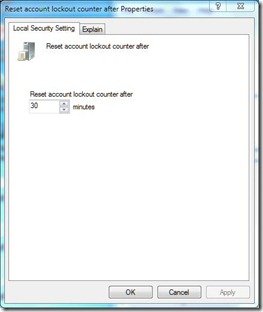
The Reset account lockout counter after security setting determines the number of minutes that must elapse after a failed login attempt before the failed logon attempt counter is reset to 0 bad logon attempts. The available range is 1 minute to 99,999 minutes. If an account lockout threshold is defined, this reset time must be less than or equal to the Account lockout duration.
Click OK once the desired values are set!
Now if anyone enters the wrong password for more than the set number of times, the user account will get locked out, and the Administrator will have to unlock it.
Read: How to Restrict or set Time Limit for User Account in Windows
Incidentally, to see your Current Account Lockout Threshold Setting, type ‘net accounts’ in an elevated CMD and hit Enter.
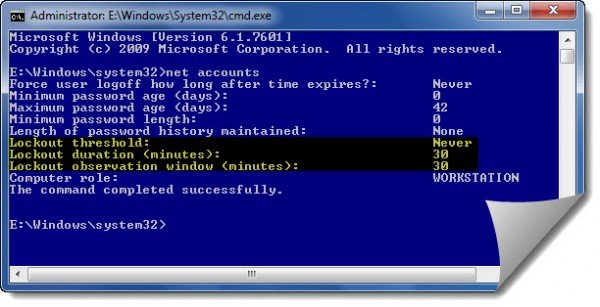
Here you will see your current values.
For users that do not have Group Policy, there is still a way to set the values via the command prompt
Open an elevated Command Prompt and use the following to set the values (replace X with the value you wish).
net accounts /lockoutthreshold:X
net accounts /lockoutwindow:X
net accounts /lockoutduration:X
Afterward, type in ‘net accounts‘ to view the applied changes.
Now see how you can Harden Windows Login Password Policy.