If you think the only form of terrorism is the one daily shown on our television sets where they show blood, you are wrong. There is much more to terrorism used by militant and terrorist outfits as well as people into the business of destruction and obstruction. Also known as digital terror, Internet terrorism comprises of methods that can lead to serious loss of data, crashing of networks and websites, and in rare cases – heating systems to an extent where they blow off as if some bomb exploded.
What is Internet Terrorism

Broadly put, the term Internet Terrorism or Cyber Terrorism relates to any activity performed using the Internet with the intent to destroy something valuable or to disable any service for a limited or indefinite period.
There are two faces to this. Internet hackers and malicious users of the Internet actively use one. The other is not very visible but is used by regular terror elements. We cannot say which one is more dangerous, but in most cases, the latter often leads to loss of lives.
How Terrorist Use Internet For Terrorism
The early known case of Internet Terrorism was using cryptography to transmit messages by some terrorist groups. Their language symbols look like pieces of art and they used them actively to transmit messages coded as images. It was shocking when one of my Arabic friends back there in North India gave me a CD containing some of the Middle East language symbols. He even showed me how to put up symbols artistically to produce the impression that a particular file is just a digital image.
I do not know if they still use such tactics as I never heard of such things for past few years. But sure, they are using the Internet to provoke people and bring in discontent. Such instruments or resources exist on the Internet, and I do not know why the authorities are not taking them down. Of course, the Internet is just one of the many mediums to spread terror! If you are interested in how terrorists use the Internet for terrorism, please read this piece on Wikipedia (Check citation #13).
Internet Explosives – Email Bombs; Logic Bombs; and ZIP Bombs
Leaving the second aspect of Internet Terror to the authorities, let us talk more about the first aspect – the one being used by malicious users to target websites, company databases whether on personal servers or the cloud, email systems, and sometimes an entire network – or rather, the Intranet of different organizations.
DDoS (Distributed Denial of Service) is one of the most common methods practiced using one or more of the following techniques. This list is not comprehensive; it contains only the elements that I know and found important enough to inform you. In fact, you might already know some or all of these:
- Email Bombs – Used to bring down websites and email servers
- Logic Bombs – Used to trigger off actions that can lead to damaging databases; wiping off hard disks, etc – In other words, this method is mostly used to destroy data completely or partially to make it irrecoverable
- Zip Bombs – A zip bomb or the Zip of Death is a malicious archive file designed to crash or render useless the system reading it. It is often employed to disable antivirus software to create an opening for more traditional viruses. One of its kind, the method is very interesting and can be implemented for both DDoS and rendering computers/servers and entire networks unusable. Depending upon the design of the Zip bombs, the whole Intranets of organizations can be brought down causing temporary or permanent damage.
What are Logic Bombs
You may remember one Pipeline blast. It is said that a Logic Bomb triggered off certain series of events that led to overheating that resulted in a historic, non-nuclear blast.
A logic bomb, as evident by its name, is based on a condition being met. You must have programmed using the IF-THEN-ELSE parameters as a kid. A logic bomb is the same – except that, the person using the software does not know that something “UNEXPECTED” will happen in case a certain condition is met. A known example of logic bombs was the deletion of the employee database when an employee was fired (that is, when the record containing his information was deleted). I cannot recall the exact instance (Name of company, employee, etc.) but am sure you can find more information about it on the Internet.
What are Email Bombs
Email bombs are easier to make and as such, are easier to identify. Usually, an individual or an organization’s email address is at the receiving end. In this case, the primary aim is to send so many emails to an address that the email server crashes. In some cases, if the same server is used to host email and websites/databases, the damage would be more than just email IDs crashing. That is probably why there is a limit to how many emails you can send to anyone using any of the email services – public or private. You can use email marketing companies but they too, take care of distributing of your email list in a way that nothing is affected in a negative way.
What is a ZIP Bomb
Among the most unsuspecting Internet bombs are the ZIP bombs. They are actually a ZIP file containing a very huge file that is encrypted in five or more rotations. If you zip the actual file once and then create a ZIP of the ZIP file – it is one rotation. Usually, five rotations are enough to compress a text file containing any single letter – such as “A” – billions and billions of times, to a very small size, that looks totally innocent. There is no way a human can create such a text file. It would be created using a special program and such programs are easy to create. For example, you can create a loop in C language and keep on writing the letter “A” until the file reaches the desired size.
The core is often a text file because such files are easiest to compress to 1/K+ times of their original size. For example, compression of some 4.5 petabytes (each letter being a byte) can lead to a ZIP file just 42 kb – for transmission over the Internet. This example is known as the 42.zip bomb. Even if you employed (notice the past tense and see next paragraph) a good anti-malware, it would get engaged in an infinite loop for scanning the contents of such ZIP bomb. And if you decide to extract them as such (giving up on scanning), where would your hard disk get the space required to store the contents of the multi-compressed file? This results in a hard disk crash and eventually, into system or server crash.
It is not that our most loved anti-malware companies are not aware of such bombs – actually digital files – with the potential to bring down and destroy any digital (and sometimes physical) assets of any individual or company – private or federal. While learning about the ZIP bombs created a kind of scare in my mind, it is soothing to know that most of the reputed anti-malware software are capable of identifying such bombs and stop them before they “explode”!
One method I found that these anti-malware use to identify and stop Internet Explosives is as follows:
Only few layers of recursion are performed on archives to help prevent attacks that would cause a buffer overflow, an out of memory condition, or exceed an acceptable amount of program execution time.
While the above would apply mostly to ZIP bombs, the anti-spam filters these days are more than enough for email bombs. Still, you need to take precautions as usual—do not give out your email ID at public places. If you receive any message asking for confirmation on whether you subscribed to some service or mailing list and cannot recall subscribing, deny it. And if you are using your own servers for email, keep them separate and well-equipped with the latest anti-spam filters!
Among the three types of Internet Explosives or Digital Bombs explained here, Logic bombs are the most difficult ones with the potential to… you know what happened to the Trans-Siberian Pipeline!
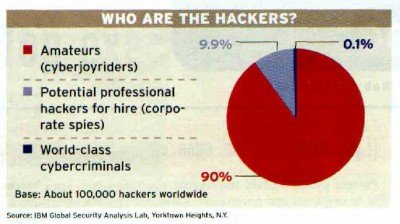
Further Reading: Paper On Internet Terrorism from etsu.edu. Image Credits: Euro Police Organization, World News Network, IBM Global Security, NY.
What is cyber terrorism?
Cyber terrorism refers to deliberate attacks on information systems, programs, or data, driven by political motives, that can lead to harm or violence. These acts aim to disrupt services or cause fear by targeting critical infrastructure or stealing sensitive information.
What is the meaning of online terrorism?
Online terrorism, also known as cyberterrorism, involves the use of illegal threats and attacks on computers, networks, and stored information. These actions aim to intimidate or coerce governments or societies to achieve political or ideological goals.
Leave a Reply