Back in the 1990s, Internet was a luxury. We never knew when and how our computers became part of the Internet instead of Internet being a part of computing. Even faster than that and before we knew, we found that not only computers but several things of our routine life are also part of the Internet.
It is the Internet of Things – AC, Cooler, Thermostat, Surveillance, CCTVs, trackers, shoes, cars and what not. Everything is or will be connected to the Internet for remote control and for observations. But they are not secure! We’ve written and read many articles on how even an amateur can hack Internet of Things (IoT) devices. While security is still a huge question mark, the issue of Ransomware in IoT too has arisen, thanks to two hackers who demoed ransomware on a thermostat.
Hacking a thermostat – First IoT device affected by ransomware

This happened in August 2016 when two white hat hackers working for a security company were able to exploit some vulnerability in a thermostat. They simply froze it and posted a message saying pay a Bitcoin to regain control. This could have got bad if they were criminals. They could have increased the temperature so that the house melts under heat and utility bills. In such a case, the owner of the thermostat would have had to pay whatever amount the criminals asked.
Other than serving as an example, the above tells you to secure your smart devices. We have an article on the security of Internet of Things that may guide you. In the case of the thermostat, there was an LCD screen big enough to display messages. Not all IoT devices will have LCDs so you may receive ransom emails from temporary IDs or calls from disposable phones. What I mean is Ransomware can affect any IoT device – whether or not it has a display. You’ll have to care for anything that you connected or intend to connect to the Internet.
IoT Ransomware is more dangerous
By normal ransomware, I mean the kind that affects computers and servers – not the ones for IoT. In the case of such ransomware, only the data on your computer is affected. You either pay up the ransom to the cyber criminals so that data files are unlocked or you clean install your computer with the data backups you already have.
Anyway, coming to the Ransomware in IoT, we can categorize devices into two:
- Simple smart devices or consumer devices like smart toaster, surveillance system, etc
- Corporate and government ventures that perform different heavy tasks such as railway management, electricity distribution, docks unloading and loading things. Basically, this category belongs to smart devices that control operations that if they fail, will affect entire cities or parts of it.
Talking about the first type – smart consumer devices – they are still not lucrative targets as the money cybercriminals ask will be much less than they can earn by hacking the IoT devices that control major operations.
For example, a smart device is used for electricity distribution for different areas. It does so in real time so that none of the areas know it is cycling. Suddenly one of the cybercriminals takes it over and stops it. All the areas covered by that grid would be darkness – until the ransom is paid.
The major difference between normal ransomware and ransomware in IoT is that while the regular ones target data files and have chances of ignoring the ransom demands. In the ransomware in IoT devices, it is not the data the hackers are interested in. They are more interested in taking control of the device. Imagine you get ready for office and turn on the car. Before you could key in GPS, you get a message saying you’ll have to pay up $300 to be able to use your car. No data is involved here (maybe minimal and you don’t care about it). But stopping the car from functioning would sure irritate you. And if the
Imagine you get ready for office and turn on the car. Before you could key in GPS, you get a message saying you’ll have to pay up $300 to be able to use your car. No data is involved here (maybe minimal and you don’t care about it). But stopping the car from functioning would sure irritate you. And if the cyber criminals add that they are going to spoil the functions of the car if you don’t pay up, you have no options but to agree for paying the ransom. You cannot make a backup copy of the car, can you? Take a look at this comic.
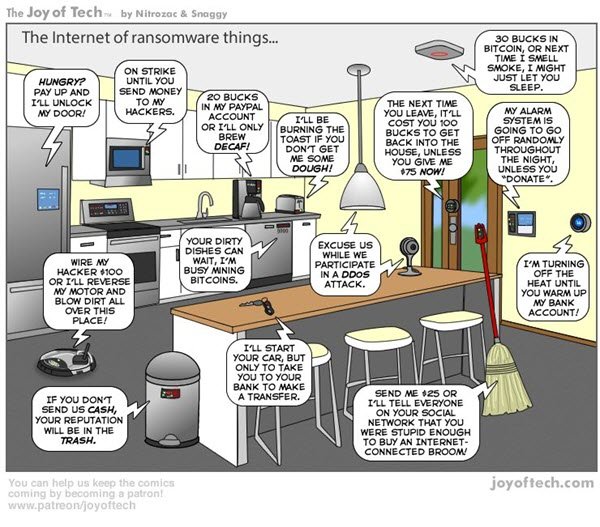
In the words of Neil Cawse, the owner of Geotab that is into IoT industry,
“In fact, due to the many practical applications of IoT technology, its ransomware can shut down vehicles, turn off power, or even stop production lines. This potential to cause far more damage means that the hackers can charge much more, ultimately making it an appealing market for them to explore.”
For consumer IoT devices, there are a few precautions you can take on your own as neither the manufacturer nor the buyers are interested in security. It is the last thing they bother about. But when it comes to projects like Smart Cities, the people involved in building them should be extremely careful. They have to use all possible precautions to avoid ransomware in IoT.
You can use the Internet of Things Scanner to check if any of your IoT devices are compromised or known publicly.
How difficult could it be for the default passwords to be randomly generated for each device?
Passwords do help. But people buying these devices continue with the default passwords in most cases. Probably, they do not realize the risks or maybe the dealer never told them about passwords in the devices.
The end user can use something that generates random and strong passwords. They should. It is not difficult – they can keep the password somewhere secure if required later. But at this moment, I guess there is not enough awareness of risks. I do not see any other reason why people ignore that part.
smart devices is suck than dummy devices :D
I’m back… Nice post, Dottie. Must be the same guys that did the IRS scam.