Any security policy plays a key role in defining the set of controls within the specified subscription. This same applies to Microsoft Azure Security Center. It lets you define policies for your Azure subscriptions by taking into consideration your company’s security needs and the type of applications.
By default, Azure Security Center recommends its users to enable a network security group (NSG) to experience improved Azure Networking. If it is not enabled you may experience trouble in controlling access inside the Azure network. Network Security Groups, also known as NSGs, contain a list of Access Control List (ACL) rules that allow or deny network traffic to your VM instances in a Virtual Network.
Microsoft Azure Security Center
It has been found that NSGs are associated with either subnets or individual VM instances within that subnet. When an NSG is associated with a subnet, the ACL rules apply to all the VM instances in that subnet. Traffic to an individual VM can be limited by associating an NSG directly to that VM.
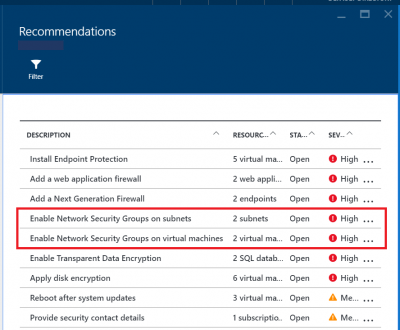
So, if an Azure service user does not have NSGs enabled, Azure Security Center will recommend 2 things to him.
- Enable Network Security Groups on subnets
- Enable Network Security Groups on virtual machines
A user can use his discretion in deciding which level, subnet or VM he should use and apply NSGs. For enabling Network Security Groups in Azure Security Center, follow the steps outlined below.
Access the recommendation table of Azure Security Center and under the Recommendations blade, select ‘Enable Network Security Groups’ on subnets or on virtual machines.
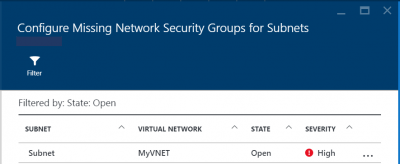
This action opens the blade ‘Configure Missing Network Security Groups’ for subnets or for virtual machines, depending on the recommendation that you selected.
Thereafter, simply select a subnet or a virtual machine to configure an NSG on.
Now, when ‘Choose network security group’ blade appears on your screen, select an existing NSG or select ‘Create new’ to create an NSG.
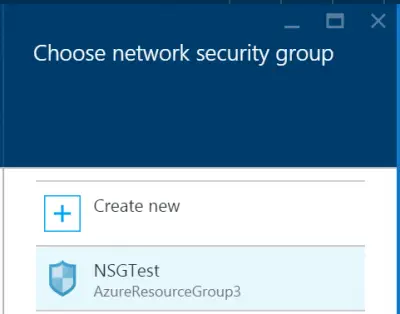
This is how you can enable and configure Network Security Groups in Azure Security Center to manage access to Azure Network.
For a full read visit docs.microsoft.com.