In earlier days, if someone had to hijack your computer, it was usually possible to get hold of it by physically being there or using remote access. While the world has moved ahead with automation and computer security has tightened, one thing that hasn’t changed is human mistakes. That is where the Human-operated Ransomware Attacks come into the picture. These handcrafted attacks find a vulnerability or a misconfigured security on the computer and gain access. Microsoft has come up with an exhaustive case study that concludes that IT admin can mitigate these human-operated Ransomware attacks by a significant margin.
Mitigating Human-operated Ransomware Attacks
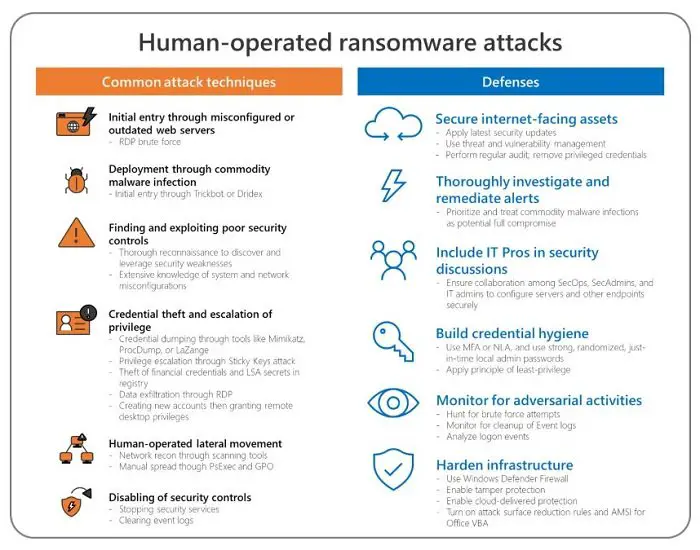
According to Microsoft, the best way to mitigate these kinds of ransomware, and handcrafted campaigns is to block all unnecessary communication between endpoints. It is also equally important to follow best practices for credential hygiene such as Multi-Factor Authentication, monitoring brute force attempts, installing the latest security updates, and more. Here is the complete list of defense measures to be taken:
- Make sure to apply Microsoft recommended configuration settings to protect computers connected to the internet.
- Defender ATP offers threat and vulnerability management. You can use it to audit machines regularly for vulnerabilities, misconfigurations, and suspicious activity.
- Use MFA gateway such as Azure Multi-Factor Authentication (MFA) or enable network-level authentication (NLA).
- Offer least-privilege to accounts, and only enable access when required. Any account with domain-wide admin-level access should be at the minimum or zero.
- Tools like Local Administrator Password Solution (LAPS) tool can configure unique random passwords for admin accounts. You can store them in Active Directory (AD) and protect using ACL.
- Monitor for brute-force attempts. You should be alarmed, especially if there is a lot of failed authentication attempts. Filter using event ID 4625 to find such entries.
- Attackers usually clear the Security Event logs and PowerShell Operational log to remove all their footprints. Microsoft Defender ATP generates an Event ID 1102 when this occurs.
- Turn on Tamper protection features to prevent attackers from turning off security features.
- Investigate event ID 4624 to find where accounts with high privileges are logging on. If they get into a network or a computer that is compromised, then it can be a more significant threat.
- Turn on cloud-delivered protection and automatic sample submission on Windows Defender Antivirus. It secures you from unknown threats.
- Turn on attack surface reduction rules. Along with this, enable rules that block credential theft, ransomware activity, and suspicious use of PsExec and WMI.
- Turn on AMSI for Office VBA if you have Office 365.
- Prevent RPC and SMB communication among endpoints whenever possible.
Read: Ransomware protection in Windows.
Microsoft has put up a case study of Wadhrama, Doppelpaymer, Ryuk, Samas, REvil
- Wadhrama is delivered by brute-force attacks on servers with Remote Desktop. The attackers usually discover unpatched systems and use disclosed vulnerabilities to gain initial access or elevate privileges.
- Doppelpaymer is manually spread through compromised networks using stolen credentials for privileged accounts. That’s why following the recommended configuration settings for all computers is essential.
- Ryuk distributes payload over email (Trickboat) by tricking the end-user about something else. Recently hackers used the Coronavirus scare to trick the end-user. One of them was also able to deliver the Emotet payload.
The common thing about each of them is that they are built based on situations. They seem to be performing guerilla tactics, moving from one machine to another to deliver the payload. It is essential that IT admins not only monitor the ongoing attack, even if it’s on a small scale, but also educate employees about how they can help protect the network.
I hope all IT admins can follow the suggestion and mitigate human-operated Ransomware attacks.
Related read: What to do after a Ransomware attack on your Windows computer?
Leave a Reply