Windows 11/10 offers an inbuilt Network Sniffer Tool — PktMon.exe — to monitor internal packet propagation and packet drop reports. This tool can help you snoop around. The network can help you resolve the cause of network latency, identify impacted applications, and provide insight into top metrics when used with an additional set of tools. This post will show how you can use the new Network Sniffer Tool (PktMon.exe) in Windows 11/10.
Network Sniffer Tool pktmon.exe in Windows 11/10
PktMon.exe or Packet Monitor is the new network sniffer or network diagnostic and packet monitoring tool. It is located in the Systems folder, which means you can invoke it from the Run or Command Prompt or PowerShell.
If the program reminds you about Netsh Trace Command, then you are right. Netsh Trace command helps you enable and configure network tracing to assist you when troubleshooting network connectivity problems.
What can PktMon can do?
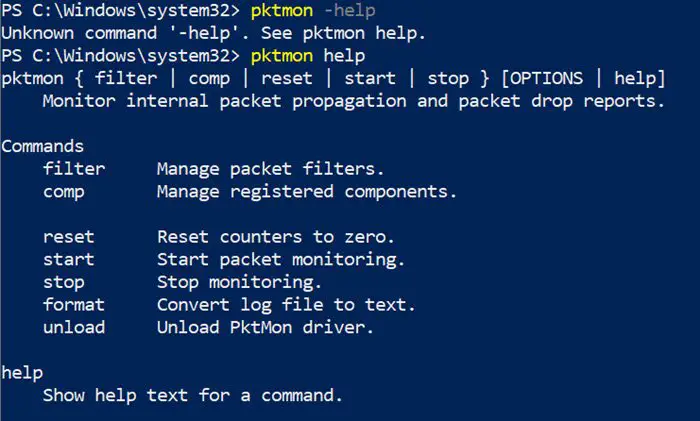
If you run PktMon.exe Help on the command prompt. Here is what you get:
- filter: Manage packet filters.
- comp: Manage registered components.
- reset: Reset counters to zero.
- start: Start packet monitoring.
- stop: Stop monitoring.
- format: Convert log file to text.
- unload: Unload PktMon driver.
And if you want further help on a specific command, then you can run help against that command. Here is how it looks like:
pktmon filter help
pktmon filter { list | add | remove } [OPTIONS | help]
Commands list Display active packet filters. add Add a filter to control which packets are reported. remove Removes all filters.
PktMon.exe also comes with real-time monitoring and support for the PCAPNG file format.
Read: How to enable and test DNS over HTTPS in Windows.
How to use PktMon to monitor network traffic
Here is an example of how to use it with a simple example.
- Create a Filter to monitor a port
- Start Monitoring
- Export Log into a readable format
This example is assuming that you want to monitor a port number on the computer, which might be having issues often.
1. Create a Filter
The primary option that allows you to monitor traffic is —filter. Using this option, you can create a filter to control which packets are reported based on Ethernet Frame, IP header, TCP header, and Encapsulation. If you run the program mentioned below, you will get full details on what you can do with the filter.
pktmon filter add help
So coming back to our topic, let’s assume that we are going to monitor TCP port no 1088. It can be a port used by your custom application, which is crashing, and PktMon can help you figure out if the network is the problem.
Open Command Prompt or PowerShell with admin privileges
Create a packet filter using the command: “pktmon filter add -p [port]”
pktmon filter add -p 1088
You can then run the command “pktmon filter list” to see a list of added filters.
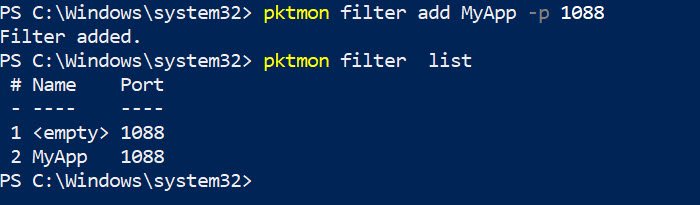
To remove all the filters run the command “pktmon filter remove”
2. Start Monitoring
Since this is not an automated program running in the background but works on-demand, you need to start monitoring manually. Run the following command to start monitoring packets
pktmon start --etw - p 0
It will start the monitoring and created a log file at the mentioned location. You will have to manually stop using the “stop” argument to stop the logging, or it will end when the computer shuts down. If you run the command with “-p 0” then it will only capture 128 bytes of a packet.
Log filename: C:\Windows\system32\PktMon.etl Logging mode: Circular Maximum file size: 512 MB
3. Export Log into a readable format
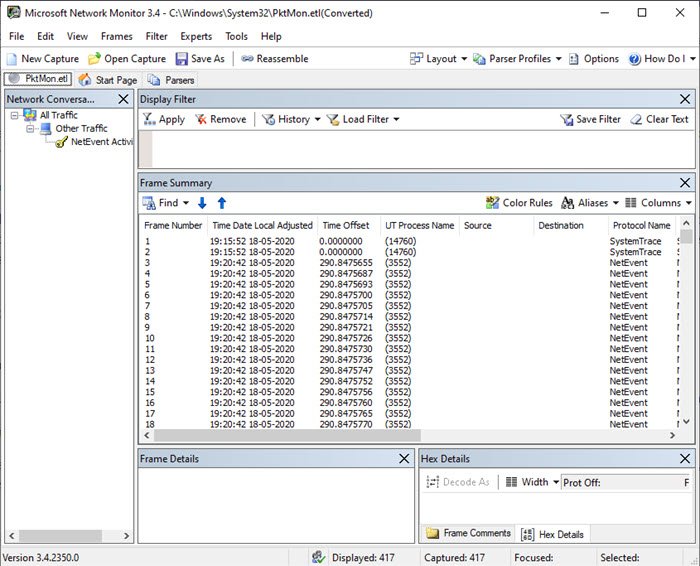
The log file is saved into PktMon.ETL file which can be converted into a human-readable format using the following command
pktmon format PktMon.etl -o port-monitor-1088.txtHaving done that, while you open the file in notepad, and read it, to make sense, you will have to use the Microsoft Network Monitor. It can directly read the ETL file.
Microsoft has rolled out support for real-time monitoring.
Related read: Free Packet Sniffing Tools for Windows.
Is network sniffing illegal?
Network sniffing is illegal when conducted without authorization. Unauthorized packet sniffing is often used by hackers to monitor and steal sensitive data, which constitutes illegal activity. Legal network sniffing is typically done by IT professionals for network monitoring and troubleshooting with proper authorization.
How to trace network traffic in Windows?
To trace network traffic in Windows, you can use the built-in tool called Network Monitor or third-party tools like Wireshark. Open Network Monitor, start a new capture and filter the traffic based on protocols or IP addresses to analyze the data more effectively.