A Kill Switch or Vaccination for the Petrwrap or NoPetya or NotPetya Ransomware has been found that can stop the ransomware in its tracks and save your computer from being infected. The NotPetya Ransomware has already created havoc in most parts of the world.
NotPetya uses the EternalBlue vulnerability (WannaCry technique) that infects computers using SMBv1. It also uses Windows WMIC and PSExec processes. If the WannaCry vulnerability is patched on your system, it uses PsExec or LSADUMP and the Windows Management Interface to spread.
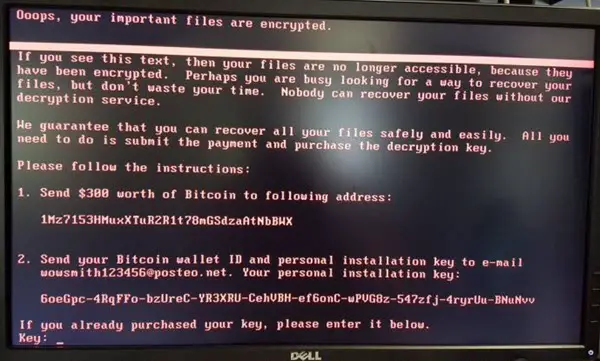
The ransomware is capable of attacking and infecting all Windows systems. It overwrites the Master Boot Record and on reboot, infects the computer blocking access to it. Once it hacks your computer, it demands a ransom amount of $300 in Bitcoin.
If your computer reboots and you see this ‘false check disk’ message, power off immediately!
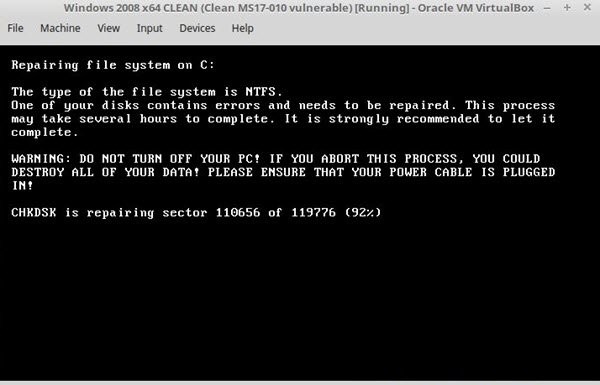
This is the NotPetya encryption process taking place. If you power off immediately or do not power on, your data will remain safe.
If the encryption process is allowed to continue, you will lose your data to theis ransomware!
There are however some basic precautions you can take, and they are:
- Install all Windows patches
- Block SMB1 across your network
- Disable default ADMIN$ accounts and communication to Admin$ shares
- Use a tool like MBR filter to block write access to the Master Boot Record
More details about how this ransomware operates can be found on Cybereason.com.
NotPetya Ransomware Vaccination
Cybereason Principal Security Researcher Amit Serper tweeted that he has discovered a vaccination that stops NotPetya ransomware in its tracks.
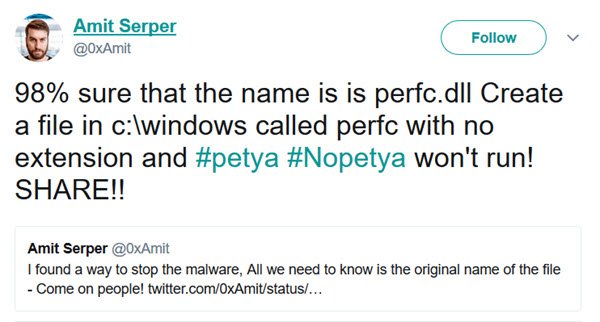
To activate the vaccination mechanism you have to create a file named perfc, with no extension and place it in the C:\Windows\ folder.
When NotPetya ransomware runs, it searches for this file in the C:\Windows\ folder, and if it is found, it ceases its operation.
UPDATE: Eset recommends that you create three blank files with the following filenames and extensions:
- C:\Windows\perfc
- C:\Windows\perfc.dat
- C:\Windows\perfc.dll
Ransomware attacks are on the rise, and all computers users need to take some basic precautions to secure their systems. One can also consider some free anti-ransomware software like RansomFree as an additional security layer.
You might want to also check out CyberGhost Immunizer.
This vaccine guy’s message is so confusing. First he says the name is perfc.dll. Then he tells people to create a file perfc without a file extension. These two statements contradict each other. No one on earth exactly knows what he means. If you browse different reports of this same story, they all come up with different interpretations. Hilariously, this reporter amends the story by recommending three different filenames at the end. Is it a scam or what? Really suspicious.
IMO the reason there is no file extension is that petya must just go looking for the perfc fileby name and not the extension.
I have checked out the ESET website to see whjat they suggested. And as above they reccomend the 3 files as above. Note the first file is perfc without an extension. The other two files must be what they think are also required.
So Anand is correct in what he says.
He thinks that the file should be perfc.dll – but he is only 98% sure – hence make one without an extension.
Later on Eset – after some time and additional research maybe – says, create the 3 files as a matter of abundant precaution.
And BTW, have better things to do than trying to scam people! :)
This SMB1 fix caused caused me to lose access to my home network drive. There has to better a way to do this.