If you use Office 365 Threat Intelligence, you can set up your account to run simulations of real-time phishing and brute-force attacks on your corporate network. It helps in preparing for such attacks in advance. You can teach your employees to identify such attacks using Office 365 Attack Simulator. This article checks out some methods to simulate phishing attacks.
The types of attacks you can simulate using Office 365 Attack Simulator include the following.
You can access the Attack Simulator under Threat Management in Security and Compliance Center. If it is not available there, the chances are that you don’t have it yet.
Keep the following in mind:
- In many cases, the older subscriptions won’t auto-include Office 365 Threat Intelligence. It has to be purchased as a separate add-on
- If you are using a custom, on-premise mail server instead of the regular Exchange Online, the simulator will not work
- The account that you use for running the attack should be using multi-factor authentication in Office 365
- You need to be logged in as global administrator to launch the attack
Attack Simulator for Office 365
You need to get creative and think like a hacker for proper attack simulations. One of the focused phishing attacks is the spear phishing attack. Generally, people indulging in spear phishing, research a bit before attacking and use a display name that sounds familiar and trustworthy. Such attacks are mainly executed for obtained users’ credentials.
How to carry out phishing attacks using Attack Simulator Office 365
The method of carrying out phishing attacks using Attack Simulator in Office 365 depends on the type of attack you are attempting. However, the user interface is self-explanatory and thus adds to the ease of attack simulation.
- Start with Threat Management > Attack Simulator
- Name the project with a meaningful phrase that will help you later when processing data
- If you wish to use a readymade template, you can do so by clicking on Use Template
- In the box below Name, select the email template that you want to send to your target recipients.
- Click NEXT
- In this screen, specify the target recipients; it can be individuals or a group
- Click NEXT
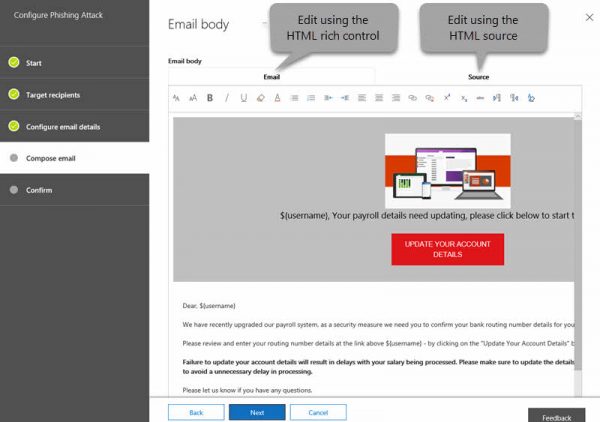
- The third screen allows for configuring the email details; here is the place to specify the display name, email ID, phishing login URL, custom landing page URL, and email subject
- Click FINISH to launch the spear phishing attack
There are few other types of attacks available in the Office 365 Attack Simulator, such as Password-Spray and Brute-Force attacks. You can check them out simply by adding or inputting one or more common passwords to see if there are chances of the network being compromised by hackers.
The drills will help you educate your employers on different types of Phishing attacks. You can also use the data later to figure out things in your office.
If you have doubts about Attack Simulator in Office 365, please leave a comment. You can read more on this at docs.microsoft.com.
Leave a Reply