Sometimes, novice or innocent users can be tricked into unwittingly participating if sends information to another resource. This may add a privacy risk. For instance, HTML5 has added a feature to the web called Hyperlink Auditing. If you are not aware of this feature, Hyperlink auditing is added to a web page or created by an area element that has a ping attribute.
Hyperlink Auditing Pings in Chrome & Firefox browsers
It is normally used by sites to track link clicks but has also been found to be abused by cyber-criminals to pass the massive amount of web requests to sites in an attempt to take them offline. So, how to disable this feature in your Chrome or Firefox browser? Also, let us try to answer a few questions related to it.
We’ll proceed in 2 steps-
- Disable Hyperlink auditing
- Determine if Hyperlink auditing good or bad
Hyperlink auditing is an HTML standard that allows the creation of special links that ping back to a specified URL when they are clicked on. These pings are done in the form of a POST request to the specified web page that can then examine the request headers to see what page the link was clicked on.
1] Disable Hyperlink auditing
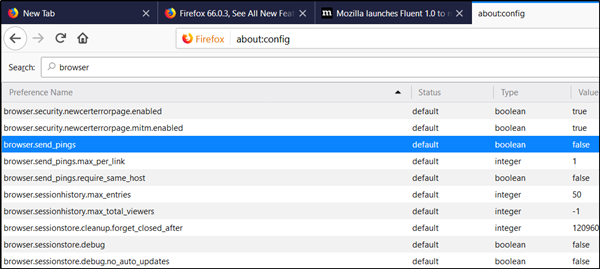
Firefox is one of the few browsers that have the ping attribute disabled by default. You can verify it by opening the browser and taking a look at about:config > browser.send_pings entry value. See the screenshot below for more information.
Chrome is planning to remove this ability in future versions. However, you can still disable it by opening chrome://flags#disable-hyperlink-auditing and setting the flag to Disabled.
For your information in newer versions, Hyperlink ping tracking feature will be enabled by default, and so you may not see these flags in your browser.
2] Is Hyperlink auditing good or bad
There was a report sometime earlier; it suggested that a new type of DDoS attack abuses the HTML5 Ping-based hyperlink auditing feature.
The attack primarily involves users innocently visiting a crafted web page with two external JavaScript files. One of which includes an array containing URLs (believed to be targets of the DDoS attack. The second JavaScript file had a function that randomly selected an URL from the array, created the <a> tag with a ‘ping’ attribute, and pro-grammatically clicked the link every second. This enabled attackers to send hyperlink auditing ping to the target so long the web page was opened. As such, rather than vulnerability, the attack relied on turning a legitimate feature into an attack tool.
This is a worrying trend, and so Hyperlink auditing is generally not considered as a good idea.