Windows 10 Creators Update security enhancements include improvements in Windows Defender Advanced Threat Protection. These enhancements would keep the users protected from threats like Kovter and Dridex Trojans, says Microsoft. Explicitly, Windows Defender ATP can detect code injection techniques associated with these threats, such as Process Hollowing and Atom Bombing. Already used by numerous other threats, these methods allow malware to infect the computers and engage in various despicable activities while remaining stealthy.
Process Hollowing
The process of spawning a new instance of a legitimate process and “hollowing it out” is known as Process Hollowing. This is basically a code injection technique in which the Legitimate code is replaced with that of the malware. Other injection techniques simply add a malicious feature to the legitimate process, hollowing results in a process that appears legitimate but is primarily malicious.
Process Hollowing used by Kovter
Microsoft addresses process hollowing as one of the biggest issues, it is used by Kovter and various other malware families. This technique has been used by malware families in file-less attacks, where the malware leaves negligible footprints on the disk and stores and executes code only from the computer’s memory.
Kovter, a family of click-fraud Trojans that have very recently been observed to associate with ransomware families like Locky. Last year, in November Kovter, was found accountable for a massive spike in new malware variants.
Kovter is delivered mainly through phishing emails, it hides most of its malicious components via registry keys. Then Kovter uses native applications to execute the code and perform the injection. It achieves persistence by adding shortcuts (.lnk files) to the startup folder or adding new keys to the registry.
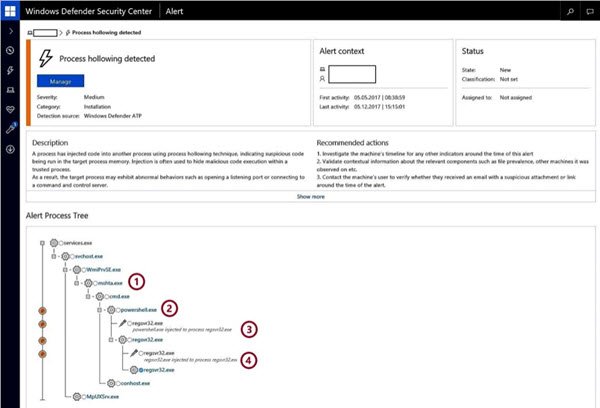
Two registry entries are added by the malware to have its component file opened by the legitimate program mshta.exe. The component extracts an obfuscated payload from a third registry key. A PowerShell script is used to execute an additional script that injects shellcode into a target process. Kovter uses process hollowing to inject malicious code into legitimate processes through this shellcode.
Atom Bombing
Atom Bombing is another code injection technique that Microsoft claims to block. This technique relies on malware storing malicious code inside atom tables. These tables are shared memory tables where all applications store the information on strings, objects, and other types of data that require daily access. Atom Bombing uses asynchronous procedure calls (APC) to retrieve the code and insert it into the memory of the target process.
Dridex an early adopter of the atom bombing
Dridex is a banking trojan that was first spotted in 2014 and has been one of the earliest adopters of atom bombing.
Dridex is mostly distributed via spam emails, it was primarily designed to steal banking credentials and sensitive information. It also disables security products and provides the attackers with remote access to the victim’s computers. The threat remains surreptitious and obstinate by avoiding common API calls associated with code injection techniques.
When Dridex is executed on the victim’s computer, it looks for a target process and ensures user32.dll is loaded by this process. This is because it needs the DLL to access the required atom table functions. Following, the malware writes its shellcode to the global atom table, further it adds NtQueueApcThread calls for GlobalGetAtomNameW to the APC queue of the target process thread to force it to copy the malicious code into memory.
John Lundgren, the Windows Defender ATP Research Team, says,
“Kovter and Dridex are examples of prominent malware families that evolved to evade detection using code injection techniques. Inevitably, process hollowing, atom bombing, and other advanced techniques will be used by existing and new malware families,” he adds “Windows Defender ATP also provides detailed event timelines and other contextual information that SecOps teams can use to understand attacks and quickly respond. The improved functionality in Windows Defender ATP enables them to isolate the victim machine and protect the rest of the network.”
Microsoft is finally seen addressing code injection issues, hope to eventually see the company adding these developments to the free version of Windows Defender.
Is Microsoft Defender and ATP the same?
Microsoft Defender ATP was originally launched as Windows Defender ATP. In 2019, the product was renamed Microsoft Defender ATP. At Ignite 2020, we launched the Microsoft Defender for Cloud XDR suite. The Microsoft Defender for Endpoint component was renamed Microsoft Defender for Endpoint.
What happened to Microsoft’s advanced threat protection?
Office 365 Advanced Threat Protection has been renamed Microsoft Defender for Office 365. However, Microsoft’s commitment to providing the best possible protection against attacks targeting Office 365 remains unchanged.