Microsoft has published guidance for a newly discovered vulnerability in MSDT (Microsoft Support Diagnostic Tool). This security flaw was recently discovered by the researchers and was identified as a Zero-Day Remote Code Execution vulnerability and Microsoft is now tracking it as CVE-2022-30190. This security flaw reportedly can affect all the versions of Windows PCs having the MSDT URI protocol enabled.

As per the blog post submitted by MSRC, your computer becomes vulnerable to this attack when Microsoft Support Diagnostic Tool is called using the URL protocol from calling applications like MS Word. The attackers can exploit this vulnerability through crafted URLs that use the MSDT URL protocol.
“An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application. The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights”, says Microsoft.
Well, the good thing is that Microsoft has released a few workarounds for this vulnerability.
Protect Windows from Microsoft Support Diagnostic Tool Vulnerability
Disable the MSDT URL Protocol
Since the attackers can exploit this vulnerability through the MSDT URL protocol, it can be fixed by disabling the MSDT URL Protocol. Doing this will not launch the troubleshooters as links. You can, however, still access the troubleshooters using the Get Help feature on your system.
To disable the MSDT URL Protocol:
- Type CMD in the Windows Search option and click on Run as Administrator.
- First, run the command,
reg export HKEY_CLASSES_ROOT\ms-msdt regbackupmsdt.regto back up the registry key. - And then, execute the command
reg delete HKEY_CLASSES_ROOT\ms-msdt /f.
If you want to undo this, run the Command Prompt as Administrator again and execute the command, reg import regbackupmsdt.reg. Remember to use the same filename you’ve used in the previous command.
Turn on Microsoft Defender Detections & Protections
The next thing you can do to avoid this vulnerability is to turn on the cloud-delivered protection and automatic sample submission. By doing this, your machine can quickly identify and stop the possible threats using artificial intelligence.
If you are Microsoft Defender for Endpoint customers, you can simply block the Office apps from creating child processes by enabling the attack surface reduction rule “BlockOfficeCreateProcessRule”.
As per Microsoft, Microsoft Defender Antivirus build 1.367.851.0 and later provides detections and protections for possible vulnerability exploitation like-
- Trojan:Win32/Mesdetty.A (blocks msdt command line)
- Trojan:Win32/Mesdetty.B (blocks msdt command line)
- Behavior:Win32/MesdettyLaunch.A!blk (terminates the process that launched msdt command line)
- Trojan:Win32/MesdettyScript.A (to detect HTML files that contain msdt suspicious command being dropped)
- Trojan:Win32/MesdettyScript.B (to detect HTML files that contain msdt suspicious command being dropped)
While the workarounds suggested by Microsoft may stop the attacks, it is still not a fool-proof solution as the other troubleshooting wizards are still accessible. To avoid this threat, we actually have to disable other Troubleshooting Wizards as well.
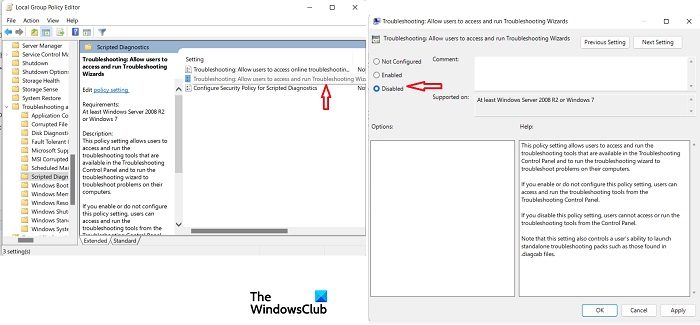
Disable Troubleshooting Wizards Using Group Policy Editor
Benjamin Delphy has tweeted a better solution wherein we can disable the other Troubleshooters on our PC using the Group Policy Editor.
- Press Win+R to open the Run Dialog Box and type gpedit.msc to open the Groups Policy Editor.
- Go to Computer Configuration > Administrative Templates > System >Troubleshooting and Diagnostics > Scripted Diagnostics
- Double-click on Troubleshooting: Allow users to access and run Troubleshooting Wizards
- In the pop-up window check the Disabled box and click on Ok.
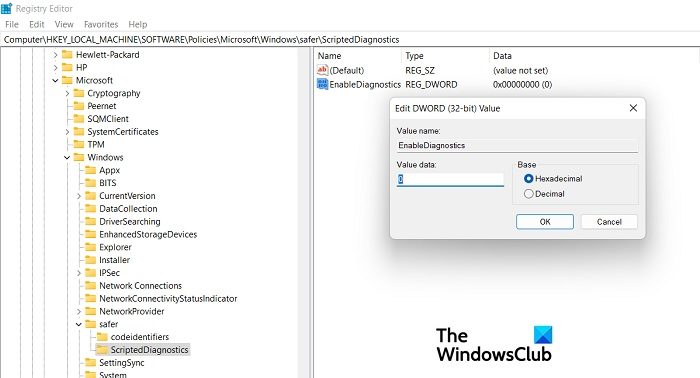
Disable Troubleshooting Wizards Using Registry Editor
In case you don’t have the Groups Policy Editor on your PC, you can use Registry Editor to disable the Troubleshooting Wizards. Press Win+R to
- Run the dialog box and type Regedit to open Registry Editor.
- Go to
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\ScriptedDiagnostics. - If you don’t see the key Scripted Diagnostic in your Registry Editor, right-click on the Safer key and click on New > Key.
- Name it as ScriptedDiagnostics.
- Right-click on Scripted Diagnostics and in the right pane, right-click on the blank space and select New > Dword (32-bit) Value and name it EnableDiagnostics. Make sure its value is 0.
- Close the Registry Editor and Reboot your PC.
Hope this helps.
Leave a Reply