Any URL is basically an IP address that you can remember easily. In other words, every working URL on the Internet is actually an IP address. The concept of IP addresses goes beyond URLs and extends to all the peripherals and computers on your network. This article is about what Proxy Auto-Config or PAC files are, what the risks are, and how to protect your browser from deliberate redirections that are malicious in most cases. For that, you need to understand the IP addresses and DNS (see next paragraph to learn about local caches). Any device in your network has an IP address. Click the link ahead to know more about DNS and how DNS works.
Between you and the website you are visiting, there are at least two caches. One is the ISP cache that contains IP addresses of most visited sites, and the other is a local file on your disk. The HOSTS file contains IP records of the websites you frequent. This caching is done to speed up access to the websites/URLs you intend to wish. Though HOSTS may also be compromised by changing the IP address assigned to the related URL, the most dangerous method is malicious PAC files. In the latter case, you do not even know for days that your machine has been compromised.
What are PAC or Proxy Auto Config Files
PAC files contain configuration for proxies used by your organization. They contain predefined values of the proxy: URL, port number, etc., details. When you launch your browser, it reads the configuration information and configures itself on its own – saving you time and effort.
Thus, PAC files intend to ease the proxy configuration. If you add a new browser to your computer or update an older version, you won’t need to configure the proxy from scratch. If its location is specified under Control Panel -> Internet Options, it will auto-configure and work accordingly.
Dangers of PAC Files
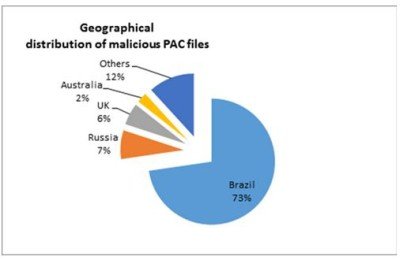
PAC files redirect your browser to some proxy URL. Microsoft came up with a blog saying PAC files are increasingly being used to compromise users – especially in Brazil. What can happen is that you downloaded some malware that creates or manipulates your PAC files in a way that you are redirected to phishing sites instead of the real sites.
The mimic sites of different types collect different types of data – your bank account number and password, secondary authentication for bank sites, and your credit card data other than your personal details. Using these details, hackers can not only empty your bank account and credit card, they can also use your identity to get loans that you will have to repay. This is called Online Identity Theft.
How to know if your PAC file is compromised
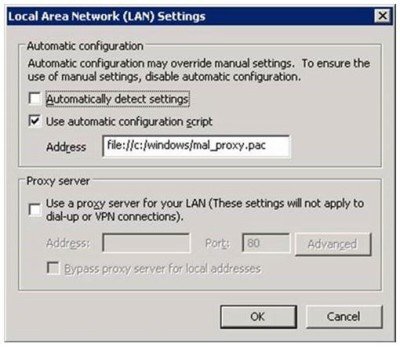
The manual method is to open Internet Options -> Connection tab -> LAN settings. If “Use Automatic Configuration Script” is checked and you know you did not install any such thing, you are in a problem. See the image below to get a complete idea of a PAC compromised computers.
You can also download Phrozensoft Auto Config Risk Protecter from phrozen.io and run it to see if your PAC files are malicious. You don’t have to install it. You just download the pack, unzip it and run ACRP.exe.
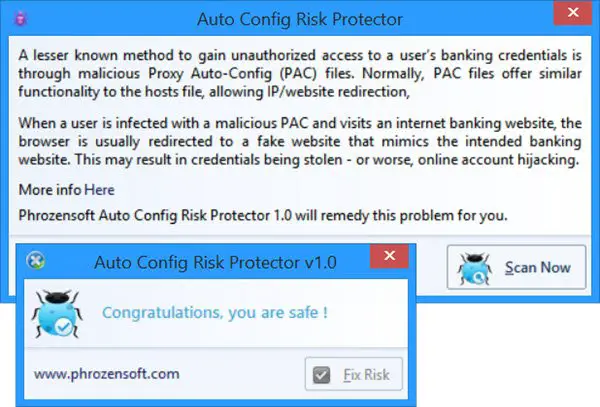
This checks your computer for PAC files and if found, check their integrity to inform you about files being corrupt/compromised
How to clean the computer
The manual method is to open Internet Options -> Connection tab -> LAN Settings. See the path of the file specified under “Use Automatic Configuration Script”, go to that folder, and delete the .pac file. Then uncheck the option in LAN settings.
For those who want to use the easier method, run Phrozensoft Proxy Protector. It will scan and present you with the list of .pac files found. Click on Fix to clean the computer.
The above explains what is PAC file/Proxy Auto-Config File. It also explains how to remove malicious PACs to prevent unwanted redirection of your browser. If you have any doubts or have had any experience, please share it with us.
GRAZIE…ARUNKUMAR…..LA TUA ECCELLENTE RECENSIONE…SECURITY….MI HA AIUTATO A NORMALIZZARE IL PROXY.CORDIALMENTE. DR.ADAMO ADAMAS KADMON