All system administrator users have one very genuine concern – securing credentials over a Remote Desktop connection. This is because malware can find its way to any other computer over the desktop connection and pose a potential threat to your data. That is why Windows OS flashes a warning “Make sure you trust this PC, connecting to an untrusted computer might harm your PC” when you try to connect to a remote desktop.
In this post, we will see how the Remote Credential Guard feature, which has been introduced in Windows 10, can help protect remote desktop credentials in Windows 11/10 Enterprise and Windows Server.
Remote Credential Guard in Windows 11/10
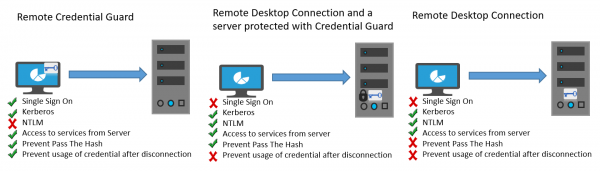
The feature is designed to eliminate threats before it develops into a serious situation. It helps you protect your credentials over a Remote Desktop connection by redirecting the Kerberos requests back to the device that’s requesting the connection. It also provides single sign-on experiences for Remote Desktop sessions.
In the event of any misfortune where the target device is compromised, credentials of the user are not exposed because both credential and credential derivatives are never sent to the target device.
The modus operandi of Remote Credential Guard is very similar to the protection offered by Credential Guard on a local machine except for Credential Guard also protects stored domain credentials via the Credential Manager.
An individual can use Remote Credential Guard in the following ways-
- Since Administrator credentials are highly privileged, they must be protected. By using Remote Credential Guard, you can be assured that your credentials are protected as it does not allow credentials to pass over the network to the target device.
- Helpdesk employees in your organization must connect to domain-joined devices that could be compromised. With Remote Credential Guard, the helpdesk employee can use RDP to connect to the target device without compromising their credentials to malware.
Hardware and software requirements
To enable smooth functioning of the Remote Credential Guard, ensure the following requirements of Remote Desktop client and server are met.
- The Remote Desktop Client and server must be joined to an Active Directory domain
- Both devices must either joined to the same domain, or the Remote Desktop server must be joined to a domain with a trust relationship to the client device’s domain.
- The Kerberos authentication should have been enabled.
- The Remote Desktop client must be running at least Windows 10, version 1607 or Windows Server 2016.
- The Remote Desktop Universal Windows Platform app doesn’t support Remote Credential Guard so, use Remote Desktop classic Windows app.
Enable Remote Credential Guard via Registry
To enable Remote Credential Guard on the target device, open Registry Editor and go to the following key:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa
Add a new DWORD value named DisableRestrictedAdmin. Set the value of this registry setting to 0 to turn on Remote Credential Guard.
Close the Registry Editor.
You can enable Remote Credential Guard by running the following command from an elevated CMD:
reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa /v DisableRestrictedAdmin /d 0 /t REG_DWORD
Turn on Remote Credential Guard by using Group Policy
It is possible to use Remote Credential Guard on the client device by setting a Group Policy or by using a parameter with Remote Desktop Connection.
From the Group Policy Management Console, navigate to Computer Configuration > Administrative Templates > System > Credentials Delegation.
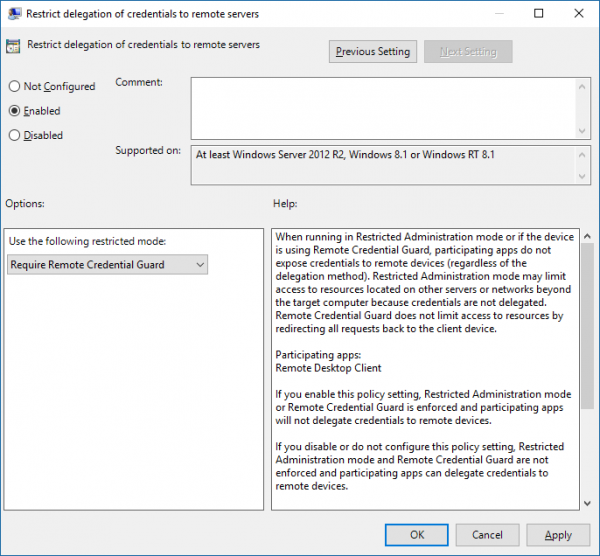
Now, double-click Restrict delegation of credentials to remote servers to open its Properties box.
Now in the Use the following restricted mode box, choose Require Remote Credential Guard. The other option Restricted Admin mode is also present. Its significance is that when Remote Credential Guard cannot be used, it will use Restricted Admin mode.
In any case, neither Remote Credential Guard nor Restricted Admin mode will send credentials in clear text to the Remote Desktop server.
Allow Remote Credential Guard, by choosing ‘Prefer Remote Credential Guard’ option.
Click OK and exit the Group Policy Management Console.
Now, from a command prompt, run gpupdate.exe /force to ensure that the Group Policy object is applied.
Use Remote Credential Guard with a parameter to Remote Desktop Connection
If you don’t use Group Policy in your organization, you can add the remoteGuard parameter when you start Remote Desktop Connection to turn on Remote Credential Guard for that connection.
mstsc.exe /remoteGuard
Things you should keep in mind when using Remote Credential Guard
- Remote Credential Guard cannot be used to connect to a device that is joined to Azure Active Directory.
- Remote Desktop Credential Guard only works with the RDP protocol.
- Remote Credential Guard does not include device claims. For example, if you’re trying to access a file server from the remote and the file server requires device claim, access will be denied.
- The server and client must authenticate using Kerberos.
- The domains must have a trust relationship, or both the client and the server must be joined to the same domain.
- Remote Desktop Gateway is not compatible with Remote Credential Guard.
- No credentials are leaked to the target device . However, the target device still acquires the Kerberos Service Tickets on its own.
- Lastly, you must use the credentials of the user who is logged into the device. Using saved credentials or credentials that are different than yours are not permitted.
You can read more on this at Technet.
Related: How to increase the number of Remote Desktop Connections in Windows 11/10.
Leave a Reply