A Security Identifier (SID) is a unique value of variable length that is used to identify a security principal (such as a security group) in Windows 11/10 operating systems. SIDs that identify generic users or generic groups are particularly well-known. Their values remain constant across all operating systems. In this post, we will attempt to understand why some SIDs do not resolve to friendly names and then recommend what can be done to resolve any SID to a friendly name if possible.
This information is useful for troubleshooting issues that involve security. It is also useful for troubleshooting display issues in the Windows Access Control List (ACL) editor. Windows tracks a security principal by its SID. To display the security principal in the ACL editor, Windows resolves the SID to its associated security principal name.
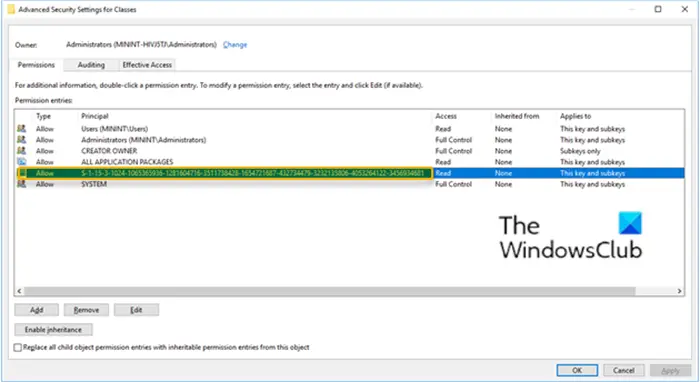
In some places in the Windows UI, as shown in the image above. you see Windows account security identifiers (SIDS) that do not resolve to friendly names. These places include the following:
- File Explorer
- Security Audit reports
- The access control list (ACL) editor in Registry Editor
These unresolved SIDs are so because Windows introduced a type of SID that is known as a capability SID. By design, a capability SID does not resolve to a friendly name.
The most commonly used capability SID is the following:
S-1-15-3-1024-1065365936-1281604716-3511738428-1654721687-432734479-3232135806-4053264122-3456934681
Windows 10, version 1809 uses more than 300 capability SIDs.
SID shows instead of Username or friendly name in Windows
When you are troubleshooting SIDs that do not resolve to friendly names, make sure that it is not a capability SID.
Caution: DO NOT DELETE capability SIDs from either the Registry or file system permissions. Removing a capability SID from file system permissions or registry permissions may cause a feature or application to function incorrectly. After you remove a capability SID, you cannot use the UI to add it back.
To get a list of all of the capability SIDs that Windows has a record of, follow these steps:
Press Windows key + R.
In the Run dialog box, type regedit and press Enter to open Registry Editor.
Navigate or jump to the registry key path below:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SecurityManager\CapabilityClasses\
On the right pane, double-click the AllCachedCapabilities entry.
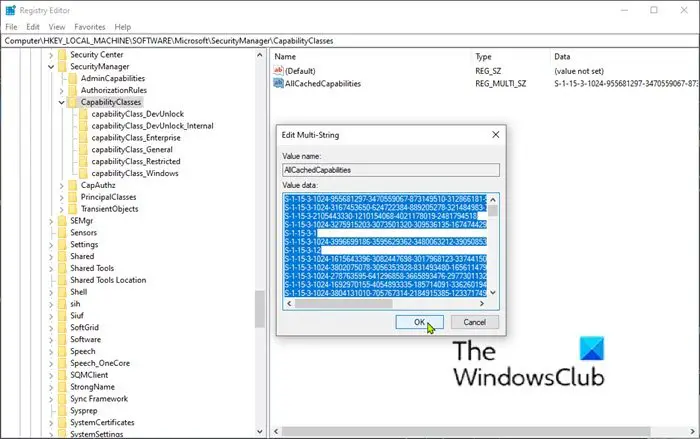
Copy all the data in Value data box and paste it into a text editor of your choice where you can search the data.
This value may not include all capability SIDs that third-party applications use.
Search the data for the SID that you are troubleshooting.
If you find the SID in the registry data, then it is a capability SID. By design, it will not resolve into a friendly name. If you do not find the SID in the registry data, then it is not a known capability SID. You can continue to troubleshoot it as a normal unresolved SID. Keep in mind that there is a small chance that the SID could be a third-party capability SID, in which case it will not resolve into a friendly name.
Capability SIDs
Capability SIDs uniquely and immutably identify capabilities. In this context, a capability is an un-forgeable token of authority that grants a Windows component or a Universal Windows Application access to resources such as documents, cameras, locations, and so forth. An application that “has” a capability is granted access to the resource that is associated with the capability. An application that “does not have” a capability is denied access to the associated resource.