Sticky Keys enables users to enter key combinations by pressing keys in sequence rather than simultaneously. This is desirable, especially for users who are unable to press the keys in combination due to some sort of physical challenge. Although enabling Sticky keys helps simplify various tasks, it also opens up a backdoor entry for hackers.
What are Sticky Key Backdoor malware attacks?
The Backdoor attack involves two steps:
- Attackers replace Ease of Access system files like sethc.exe, utilman.exe, osk.exe, narrator.exe, magnify.exe, displayswitch.exe with programs like cmd.exe, or powershell.exe.
- Attackers set cmd.exe or other shell programs as debuggers for the above-listed accessibility programs
Once the executables are switched, you can press the Shift key five times in a row to bypass the login and get a system-level command prompt if sethc.exe has been replaced. It utilman.exe is replaced, then you will have to press Win+U keys.
The attacker then effectively gets a shell without needing to authenticate and since the replacement uses a legitimate Windows binary (cmd.exe) it makes the process of identifying the Sticky Keys attack really difficult.
Once the attack has been identified, the most acknowledged and effective remedial method is to prevent the attacker from getting administrative privileges since modifying or changing the necessary keys or files in this attack requires administrative privileges.
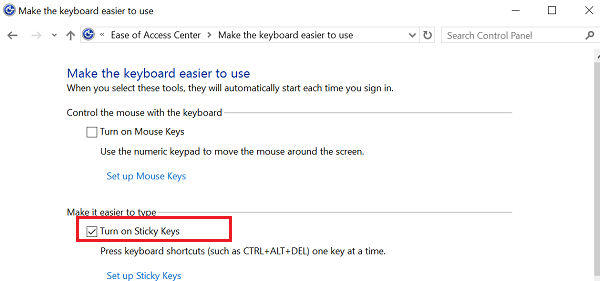
An easy way to prevent such Sticky Key Backdoor attacks is by disabling Sticky Keys on your Windows computer. To do this, open Control Panel > Ease of Access Center > Make the keyboard easier to use > Uncheck the Turn on Sticky keys checkbox as shown above in the image.
There are two ways you can detect such attacks. Match the Hashes or go through the Windows Registry. This can be can consume both, time and effort.
Sticky Keys Backdoor Scanner is a free tool that will scan your system for binary replacements and registry modifications, which can indicate that your computer may have been compromised by a Sticky Key Backdoor.
TIP: See how you can reset Administrator password in Windows using Sticky Keys.
Sticky Keys Backdoor Scanner
Sticky Keys Backdoor Scanner is a PowerShell scanner that scans for the existence of a Sticky Keys backdoor. Once in action, the Sticky Keys Scanner looks for both backdoor variants – binary replacement and registry modification and alerts you.
A user can either import and run this PowerShell function locally on the suspected computer or use PowerShell remoting to run the scanner across multiple computers using the Invoke-Command cmdlet.
It is available for download from Github should you need it.
TIP: Our Ease Of Access Replacer lets you replace the Ease of Access button in Windows with useful tools. It is safe and easy to use.