In Event Viewer, the errors logged are common, and you will come across different errors with different Event IDs. The events that are recorded in the security logs usually will be either of the keyword Audit Success or Audit Failure. In this post, we will discuss The security log is now full (Event ID 1104) including why this event is triggered and the actions you can perform in this situation whether on a client or server machine.
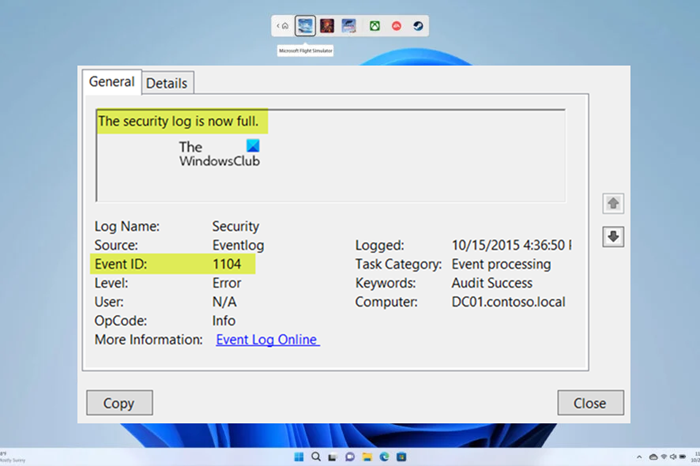
As the event description indicates, this event generates every time the Windows security log becomes full. For example, if the maximum size of the Security Event Log file was reached and the event log retention method is Do not overwrite events (Clear logs manually) as described in this Microsoft documentation. The following are the options in the security event log settings:
- Overwrite events as needed (oldest events first) – This is the default setting. Once the maximum log size is reached, older items will be deleted to make way for new items.
- Archive the log when full, do not overwrite events – If you select this option, Windows will automatically save the log when the maximum log size is reached and create a new one. The log will be archived wherever the security log is being stored. By default, this will be at the following location %SystemRoot%\SYSTEM32\WINEVT\LOGS. You can view the properties of the log-in Event Viewer to determine the exact location.
- Do not overwrite events (Clear logs manually) – If you select this option and the event log reaches the maximum size, no further events will be written until the log is manually cleared.
To check or modify your security event log settings, the first thing you may want to change would be the Maximum log size (KB) – the maximum log file size is 20 MB (20480 KB). Beyond that, decide upon your retention policy as per outlined above.
The security log is now full (Event ID 1104)
When the upper limit of the Security Log Event file size is attained, and there is no room to log more events, the Event ID 1104: The security log is now full will be logged indicating that the log file is full, and you need to perform any of the following immediate actions.
- Enable log overwriting in Event Viewer
- Archive the Windows security event log
- Manually clear the Security Log
Let’s see these recommended actions in detail.
1] Enable log overwriting in Event Viewer
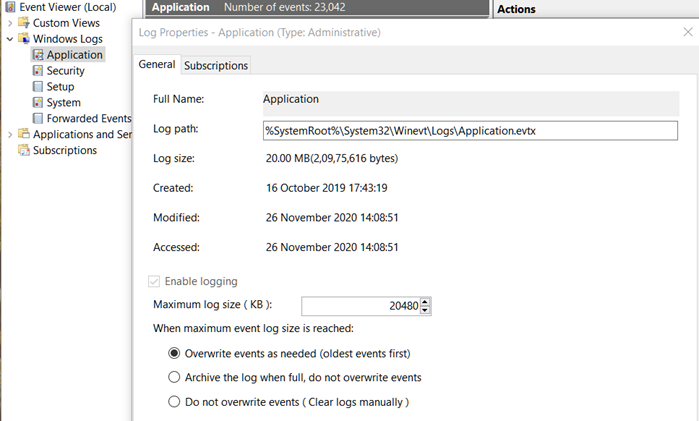
By default, the security log is configured to overwrite events as needed. When you turn on the overwriting logs option, this will allow the Event Viewer to overwrite the old logs, in turn saving the memory from getting full. So, you need to make sure that this option is enabled by following these steps:
- Press the Windows key + R to invoke the Run dialog.
- In the Run dialog box, type eventvwr and hit Enter to open Event Viewer.
- Expand Windows Logs.
- Click Security.
- On the right pane, under the Actions menu, select Properties. Alternatively, right-click on the Security log on the left navigation pane and select Properties.
- Now, under the When maximum event log size is reached section, select the radio button for the Overwrite events as needed (oldest events first) option.
- Click Apply > OK.
Read: How to view Event Logs in Windows in detail
2] Archive the Windows security event log
In a security-conscious environment (especially in an enterprise/organization), it may be necessary or mandated to archive the Windows security event log. This can be done via the Event Viewer as shown above by selecting the Archive the log when full, do not overwrite events option, or by creating and running a PowerShell script using the code below. The PowerShell script will check the size of the security event log and archive it if necessary. The steps performed by the script are as follows:
- If the security event log is under 250 MB, an informational event is written to the Application event log
- If the log is over 250 MB
- The log is archived to D:\Logs\OS.
- If the archive operation fails, an error event is written to the Application event log and an e-mail is sent.
- If the archive operation succeeds, an informational event is written to the Application event log and an e-mail is sent.
Before using the script in your environment, configure the following variables:
- $ArchiveSize – Set to desired log size limit (MB)
- $ArchiveFolder – Set to an existing path where you want the log file archives to go
- $mailMsgServer – Set to a valid SMTP server
- $mailMsgFrom – Set to a valid FROM e-mail address
- $MailMsgTo – Set to a valid TO e-mail address
# Set the archive location
$ArchiveFolder = "D:\Logs\OS"
# How big can the security event log get in MB before we automatically archive?
$ArchiveSize = 250
# Verify the archive folder exists
If (!(Test-Path $ArchiveFolder)) {
Write-Host
Write-Host "Archive folder $ArchiveFolder does not exist, aborting ..." -ForegroundColor Red
Exit
}
# Configure environment
$sysName = $env:computername
$eventName = "Security Event Log Monitoring"
$mailMsgServer = "your.smtp.server.name"
$mailMsgSubject = "$sysName Security Event Log Monitoring"
$mailMsgFrom = "from@email.address"
$mailMsgTo = "to@email.address"
# Add event source to application log if necessary
If (-NOT ([System.Diagnostics.EventLog]::SourceExists($eventName))) {
New-EventLog -LogName Application -Source $eventName
}
# Check the security log
$Log = Get-WmiObject Win32_NTEventLogFile -Filter "logfilename = 'security'"
$SizeCurrentMB = [math]::Round($Log.FileSize / 1024 / 1024,2)
$SizeMaximumMB = [math]::Round($Log.MaxFileSize / 1024 / 1024,2)
Write-Host
# Archive the security log if over the limit
If ($SizeCurrentMB -gt $ArchiveSize) {
$ArchiveFile = $ArchiveFolder + "\Security-" + (Get-Date -Format "yyyy-MM-dd@HHmm") + ".evt"
$EventMessage = "The security event log size is currently " + $SizeCurrentMB + " MB. The maximum allowable size is " + $SizeMaximumMB + " MB. The security event log size has exceeded the threshold of $ArchiveSize MB."
$Results = ($Log.BackupEventlog($ArchiveFile)).ReturnValue
If ($Results -eq 0) {
# Successful backup of security event log
$Results = ($Log.ClearEventlog()).ReturnValue
$EventMessage += "The security event log was successfully archived to $ArchiveFile and cleared."
Write-Host $EventMessage
Write-EventLog -LogName Application -Source $eventName -EventId 11 -EntryType Information -Message $eventMessage -Category 0
$mailMsgBody = $EventMessage
Send-MailMessage -From $mailMsgFrom -to $MailMsgTo -subject $mailMsgSubject -Body $mailMsgBody -SmtpServer $mailMsgServer
}
Else {
$EventMessage += "The security event log could not be archived to $ArchiveFile and was not cleared. Review and resolve security event log issues on $sysName ASAP!"
Write-Host $EventMessage
Write-EventLog -LogName Application -Source $eventName -EventId 11 -EntryType Error -Message $eventMessage -Category 0
$mailMsgBody = $EventMessage
Send-MailMessage -From $mailMsgFrom -to $MailMsgTo -subject $mailMsgSubject -Body $mailMsgBody -SmtpServer $mailMsgServer
}
}
Else {
# Write an informational event to the application event log
$EventMessage = "The security event log size is currently " + $SizeCurrentMB + " MB. The maximum allowable size is " + $SizeMaximumMB + " MB. The security event log size is below the threshold of $ArchiveSize MB so no action was taken."
Write-Host $EventMessage
Write-EventLog -LogName Application -Source $eventName -EventId 11 -EntryType Information -Message $eventMessage -Category 0
}
# Close the log
$Log.Dispose()
Read: How to schedule PowerShell script in Task Scheduler
If you want, you can use an XML file to set the script to run every hour. For this, save the following code to an XML file and then import it into Task Scheduler. Make sure to change the <Arguments> section to the folder/file name where you saved the script.
<?xml version="1.0" encoding="UTF-16"?>
<Task version="1.3" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo>
<Date>2017-01-18T16:41:30.9576112</Date>
<Description>Monitor security event log. Archive and clear log if threshold is met.</Description>
</RegistrationInfo>
<Triggers>
<CalendarTrigger>
<Repetition>
<Interval>PT2H</Interval>
<StopAtDurationEnd>false</StopAtDurationEnd>
</Repetition>
<StartBoundary>2017-01-18T00:00:00</StartBoundary>
<ExecutionTimeLimit>PT30M</ExecutionTimeLimit>
<Enabled>true</Enabled>
<ScheduleByDay>
<DaysInterval>1</DaysInterval>
</ScheduleByDay>
</CalendarTrigger>
</Triggers>
<Principals>
<Principal id="Author">
<UserId>S-1-5-18</UserId>
<RunLevel>HighestAvailable</RunLevel>
</Principal>
</Principals>
<Settings>
<MultipleInstancesPolicy>IgnoreNew</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>true</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>true</StopIfGoingOnBatteries>
<AllowHardTerminate>true</AllowHardTerminate>
<StartWhenAvailable>false</StartWhenAvailable>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<StopOnIdleEnd>true</StopOnIdleEnd>
<RestartOnIdle>false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand>true</AllowStartOnDemand>
<Enabled>true</Enabled>
<Hidden>false</Hidden>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<DisallowStartOnRemoteAppSession>false</DisallowStartOnRemoteAppSession>
<UseUnifiedSchedulingEngine>false</UseUnifiedSchedulingEngine>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>P3D</ExecutionTimeLimit>
<Priority>7</Priority>
</Settings>
<Actions Context="Author">
<Exec>
<Command>C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe</Command>
<Arguments>c:\scripts\PS\MonitorSecurityLog.ps1</Arguments>
</Exec>
</Actions>
</Task>
Read: Task XML contains a value which is incorrectly connected or out of range
Once you have enabled or configured archiving the logs, the oldest logs will be saved and will not be overwritten with newer logs. So now onwards, Windows will archive the log when the maximum log size is reached and save it to the directory (if not the default) you have specified. The archived file will be named in Archive-<Section>-<Date/Time> format, for example, Archive-Security-2023-02-14-18-05-34. The archived file can be now used to trace down older events.
Read: Read Windows Defender Event Log using WinDefLogView
3] Manually clear the Security Log
If you have set the retention policy to Do not overwrite events (Clear logs manually), you will need to manually clear the security log using any of the following methods.
- Event Viewer
- WEVTUTIL.exe utility
- Batch file
That’s it!
Now read: Missing Events in the Event Log
What Event ID is malware detected?
The Windows security event log ID 4688 indicates malware has been detected on the system. For example, if there’s malware present on your Windows system, searching event 4688 will reveal any processes executed by that ill-intentioned program. With that information, you can perform a quick scan, schedule a Windows Defender scan, or run a Defender Offline scan.
What is the security ID for the logon event?
In Event Viewer, the Event ID 4624 will be logged on every successful attempt at logging on to a local computer. This event is generated on the computer that was accessed, in other words, where the logon session was created. The event Logon type 11: CachedInteractive indicates a user logged on to a computer with network credentials that were stored locally on the computer. The domain controller was not contacted to verify the credentials.
Read: Windows Event Log Service not starting or is unavailable.
Leave a Reply