After a successful deployment of Windows 11/10 and you notice that the Trusted Platform Module (TPM) is in reduced functionality mode, then this post will help you. In this post, we identify some potential known causes for this behavior and then provide the troubleshooting guide for this issue as well as the measures you can take to prevent the issue from occurring during the deployment of Windows 11/10.
You might encounter this issue based on the following scenario.
You use Microsoft Deployment Toolkit (This can be any version of MDT that supports the OS) to deploy Windows by using the “Enable BitLocker (offline)” step (ZTIBDE.wsf script) to pre-provision BitLocker during Windows PE in the “Preinstall” group and the deployment is successful.
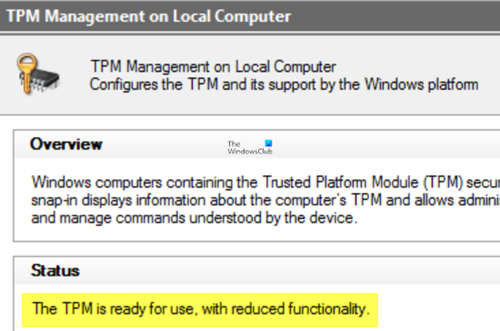
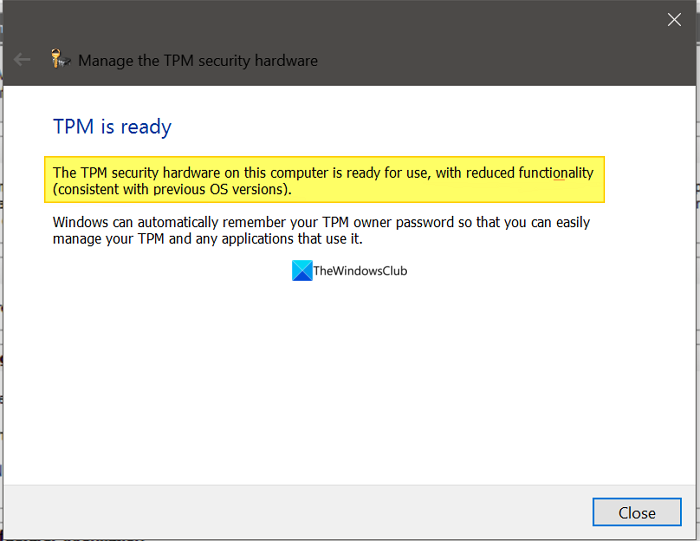
However, in this scenario, you notice that the Trusted Platform Module (TPM) is in reduced functionality mode. In this situation, the TPM Management console (TPM.msc) reports the following issue:
The TPM is ready for use, with reduced functionality. Information Flags: 0x900
The TPM owner authorization is not properly stored in the registry.
Windows’s registry information about the TPM’s Storage Root Key does not match the TPM Storage Root Key or is missing.
The TPM is ready for use, with reduced functionality
If you’re faced with the TPM reduced functionality issue, you can work around this issue for new deployments until a new version of MDT is available – add the command below to the ZTIBDE.wsf script at the start of the “Function Main” section:
reg add hklm\system\currentcontrolset\services\tpm\wmi -v UseNullDerivedOwnerAuth -t REG_DWORD -d 0x01 -f
It is worth noting that for devices in which the TPM is already in reduced functionality mode, the TPM must be cleared before you can mitigate this issue.
To prevent this issue from occurring, you’ll need to not pre-provision BitLocker, instead, wait to enable the full system. Be aware that the deployment will take longer to complete by using this method.
According to Microsoft, the TPM reduced functionality issue occurs because the TpmValidate function in the ZTIBDE.wsf script takes ownership of the TPM from Windows PE unnecessarily. Windows should be able to correctly take ownership of the TPM before Out-of-Box Experience (OOBE) to provision it by using the correct parameters.
When this change in ownership of the TPM from Windows PE occurs, the TPM is given parameters that Windows does not understand. Therefore, the key hierarchies in the TPM are disabled and made permanently unavailable to Windows.
Also read: TPM missing or not showing in BIOS
What is TPM functionality?
TPM or Trusted Platform Module is a security technology that is embedded in the computer’s motherboard or the processor. It enables platform authentication and is critical in storing and securing of important information using cryptography. Windows 11 strictly needs TPM authentication to install and run the operating system. Though there are ways to bypass TPM to install Windows 11, it is much needed for security.
How do I make my TPM ready for use?
You can use TPM using the Windows Security app as well as the Microsoft Management Console. In the Windows Security app, click on the Device Security tab. In the Device security options, you will find the Security processor. Click on Security Processor details. If you are already running Windows 11, it will be enabled by default. If there are any issues, you can troubleshoot TPM with the TPM diagnostics tool.
Related read: How to Run TPM Troubleshooter in Windows 11.