Tor is an acronym that stands for The Onion Router. While the name suggests it is a router, it is actually a browser. Tor is the browser that stands for anonymity and privacy on the Internet. This review of Tor talks about how Tor works and how it provides anonymity when you are browsing the Internet.
Tor Browser Review
Tor vs. Other Browsers
While Microsoft Edge, Mozilla Firefox and Google Chrome offer the feature where you can browse anonymously (InPrivate and InCognito modes), they still lag behind when intermediaries are sitting between the source and destination of web traffic. When you browse the web, send an email or download audio/video or anything, data is sent in the form of packets.
Each data packet has a header that tells about the source and destination of the data packet. Even if you are using an encrypted connection, the packet headers are vulnerable. Anyone sitting between the source and destination can read the packet header to know about you and your browsing habits. The people snooping include your ISPs, ad agencies and sometimes even the government agencies. As such, your browsing and what you see on the Internet is affected by the information others have gathered about you.
Why do you need Tor
Tor has been developed with a total concentration on the privacy of users. People use Tor to send confidential emails. The high-level security of Tor makes it impossible for hackers to know the origination of emails and thereby the location of the sender. Following are some uses of Tor that make it clear as to who all need the safest browser available on the planet:
- You can send data anonymously.
- You can surf the web without leaving any traces as the traces are deleted as soon as data is forwarded from one relay to another. I will come to relays in a moment – in the next section.
- You can view the websites that are otherwise censored in your country – because the ISPs won’t know what you are trying to access.
- You can host websites that will be difficult to censor because nobody knows who is hosting the website.
There are many uses of Tor – especially in a world where user privacy has been under the prying eyes of different ad agencies, social networks, and government agencies. Also, your ISPs intercept your connection requests before you actually connect to a website. Using Tor, you won’t leave any data for such agencies.
The Tor Relay Network – How Tor Works
Tor Network works on a network of relays formed by people who have volunteered for the project. Unlike other browsers that have fixed routers that receive data packets to forward them to their destinations, Tor browser uses a number of relays. To be clearer, here is the procedure:
- When you enter a URL in Tor address bar, a random route is formed using the relay computers in the Tor network.
- Each relay computer in the network works as a router. It receives data packets, forwards it to the next relay computer in the network after deleting information about the previous router.
- Once the data packet leaves the relay computer, any information about the data packet is removed from the relay computer.
- Approximately every ten minutes or so, a new relay is set up to further protect your privacy.
The below figure shows how Tor works:
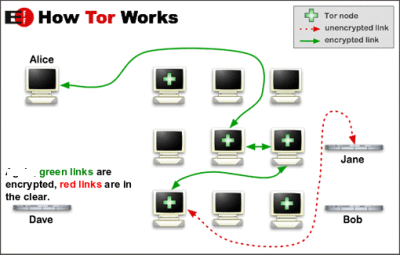
The aim is clear – to create a maze of relays so that all the information about the original source is lost in the network. This makes it impossible for the scripts on the destination website to track who sent the request/data and from where.
Read: Best Tor alternatives for anonymous browsing
What Is The Tor Bundle
When you download the Tor bundle, you get three essential programs:
- Vidalia graphical Interface
- Tor Browser
- Tor Button
When you first download the Tor bundle, you are required to extract the files. You do not need any installation. This means you can carry the extracted files on a USB drive for use with any computer running any kind of operating system.
Read: Best Privacy browsers for Windows PC.
Once you have extracted the Tor Browser Bundle, you find an executable that says “Start Tor Browser.Exe”. When you double-click this file, it launches the Vidalia graphical interface. Other than launching Tor after creating a Tor relay network, the graphical interface lets you:
- Change the default settings for the Tor browser
- View the computers acting as a relay in the Tor network
- Check out the bandwidth
- Start and stop the Tor browser (connect and disconnect the Tor connection)
- Check out the help files and About
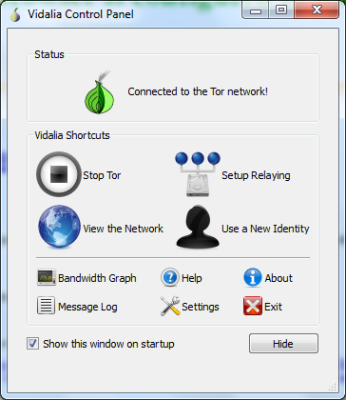
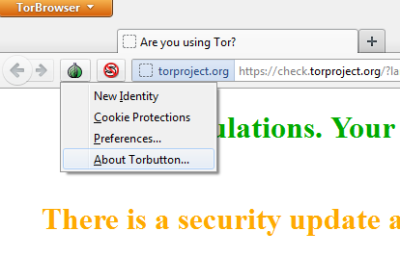
Once the relay is set up, you get the Tor browser, as shown in the first image in the above section. The Tor button is located before the address bar, and it allows you to allow/block cookies from running on the webpage you are visiting. You can also change your preferences using the Tor button. If you wish, you can start a new session (a new relay) using the Tor button.
Note that you need to download all the components using the Tor bundle. You cannot and should not try to download and use individual components as your computer may become unstable.
Read: List of free Proxy software for Windows PC.
How To Use Tor Browser
As with any browser, you just enter the URL in the address bar and hit enter to visit the website you want. The bar next to the address bar is a Quick search bar. It allows you to select websites such as Google, Amazon, Bing, Twitter, Wikipedia and more. After selecting the website that you wish to search, enter the search term and hit the Enter key.
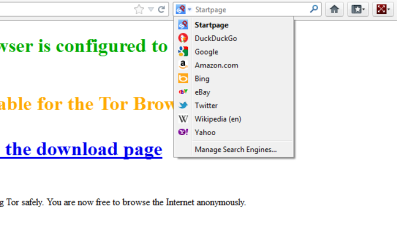
You can click on the Tor button (onion icon towards the left of the Tor browser) to set up Tor cookies and other preferences.
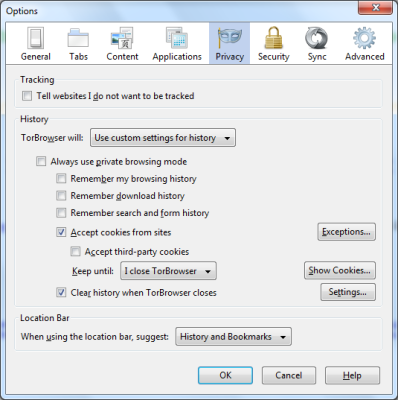
You can further customize your preferences about privacy by selecting Tor’s behavior when it comes to InCognito browsing. Click on the Tor Browser button on the title bar of Tor Browser and in the resulting sub-menu, click on Options and again on Options. In the resulting dialog box, click the Privacy tab. In this tab, you can set whether you want to save cookies, download history, passwords, etc. You can also set Tor mode where “websites should not try to track you” (Though this is not very reliable as ad agencies and especially government agencies will continue to track you irrespective of your will).
You can access the Dark Web using the TOR browser.
Drawbacks Of Tor Browser
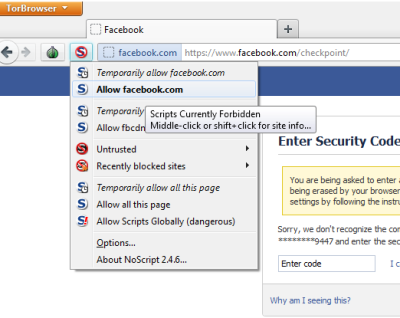
There is only one – the browser gets slower at times. This is because of the fact that the data packets are routed through a good number of relay points in the Tor browser. I could not find any other negatives while browsing with Tor. Also, on some sites, you may have to allow scripts using the S icon just before the address bar. Sites such as Facebook and Twitter make extensive use of scripts so you may face problems if you run Tor with scripts blocked. You can toggle blocking/allowing scripts using the S button.
Tor Browser Download
The above review of Tor covers just the most important features of the browser. You can download it or get more details on the Tor website. If you have anything to add, please leave a comment below.
Related: TOR browser not opening or working in Windows.
Is Tor browser safe?
Tor browser is safe! But if you use it to browse .onion sites, you must be careful. While Tor’s encryption will keep your identity and destination secret, bad actors can still find a way to identify you or push malware onto your computer.
Read: How to enable and use Tor in Brave browser
How to uninstall Tor browser
You may not see the Tor browser entry in the Control Panel or Settings. Removing Tor Browser from your system is simple:
- Search for Tor using the Start Search
- Locate your Tor Browser folder or application
- Delete the Tor Browser folder or application
- Empty your Trash
- That’s it!
Browzar, another privacy-minded browser for Windows, may also interest you. You might also want to check out this link, which talks of alternate web browsers for your Windows computer, each offering a different set of features or this one about portable browsers. You might want to also check out Epic Privacy Browser.