Cyber threats are on the rise and with increased complexity in targets, Microsoft aims at making the user aware of the sources and types of malware that can affect his/her computer from anywhere in the world. This lets consumers and enterprise alike be knowledgeable before the attack takes place. In this post, we will explain what is a Trojan Virus in computers.
What is a Trojan virus?

A Trojan horse is a type of malware disguised as useful software. The aim is that the user executes the Trojan, which gives it full control of your PC and the possibility to use it for its purposes. Most of the time, more malware will be installed in your systems, such as backdoors or key loggers.
The delivery method used is normally social engineering. Malicious code is hidden within legitimate software. Once it is downloaded to your computer disguised as a legitimate program its gets to work.
How do Trojans work
Like the famous Trojan horse, software Trojans hide inside files or images or videos and then download malware on the host system.
They typically work like this:
- Backdoor Trojans provide attackers with remote unauthorized access to and control of infected computers
- Downloaders or Droppers are Trojans that install other malicious files to a computer they have infected, either by downloading them from a remote computer or by obtaining them directly from copies contained in their own code.
Now that you know what trojans are and how they can infect systems, you need to be extra aware and keep a look out for fishy and ‘clickbait’ material on the Internet. Apart from that, you can encourage people in your organization to use personal devices for social media and web surfing instead of using devices connected to your corporate network.
What are Remote Access Trojans
Remote Access Trojans (RAT) have always proved to be a big risk to this world when it comes to hijacking a computer or just playing a prank with a friend. A RAT is malicious software that lets the operator attack a computer and gain unauthorized remote access to it. RATs have been here for years, and they persist as finding some RATs is a difficult task even for the modern Antivirus software out there.
Trojan use is on the rise
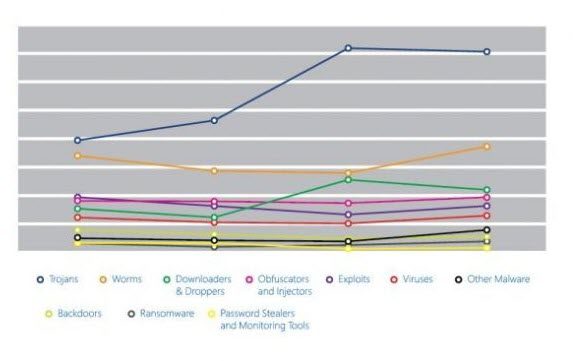
Trojans, the study reveals, are the biggest form of malware that has been used by attackers. Research showed that encounters involving Trojans increased by fifty-seven percent and stayed elevated through the end of the year. Trojans accounted for five of the top ten malware groups encountered by Microsoft real-time antimalware products.
The increase was due in large part to Trojans known as Win32/Peals, Win32/Skeeyah, Win32/Colisi, and Win32/Dynamer. Also, a pair of newly detected Trojans, Win32/Dorv, and Win32/Spursint, helped account for the elevated threat level.
An important observation in the report was that although the total number of attacks were more frequent on client platforms, the incidence of Trojans was more on server platforms, used by enterprises. Trojans accounted for three of the top ten malware and 4 of the top 10 malware and unwanted software families most commonly encountered on supported Windows server platforms were categorized as Trojans.
These observations show that all kinds of malware attacks have varying effects on the different operating system and their versions. Although the frequency could depend on how popular or not popular a certain OS is, it is mostly a random and varying factor.
You can read the difference between Virus, Trojan, Worm, Adware, Spyware, Rootkit, Malware, Backdoor, etc. here.
Leave a Reply