There is a lot of talk on Internet censorship. The US almost blocked several sites meant to share things. It took millions of phone calls and protests – both online and offline – to stop the Senate from passing the Internet Censorship bill (SOPA, as it was called). Internet censorship already exists in China where even Google is censored. Iran is building its Internet to keep its citizens away from happenings in the world. India too makes noises, on and off, about monitoring the Internet and thereby the freedom of speech. You can see the list at the end of this post.
Surf Internet Anonymously
We had posted a few reviews of tools that help you bypass any kind of censorship while protecting your privacy on the Internet. Different methods exist to protect your privacy and identity when you are online. Some are simple browsers while others are dedicated channels that encrypt data during transmission.
For example, SpotFlux is a free VPN service that creates a secure channel between your computer and Spotflux servers after masking your IP address so that anyone snooping on your Internet usage is misguided.
One more such software is TOR (The Onion Router) browser. War journalists and bloggers from countries like China, Iran, and Afghanistan use it to protect their identity. Even the Anonymous group recommends TOR as a measure to keep yourself secure on the Internet – especially if you are blogging or reporting against the federal agencies, other government, or militant agencies.
We had also discussed the Jumpto Browser, but since they offer only 100MB bandwidth per month for free, it is not feasible for many. Of course, you can go for paid versions but then, all of us love freebies, don’t we? Also, Jumpto looks as if more suited for kids.
CyberGhost VPN is another anonymity tool for Windows that completely hides and protects your identity online.
There are many more products out there. Just run a search with “security” keyword on The Windows Club or click this link to check out articles on Online Security.
The only thing you need to consider is how these companies treat your data. While TOR won’t (or rather, CANNOT) give out your data even to the legal authorities, others may compromise and share your data with others. Your favorite search engine is one such company that easily gives out your data and even sells it to advertising companies. In the endeavor to search for tools providing security online, I came across UltraSurf. The following aims to present a review of UltraSurf.
UltraSurf Review
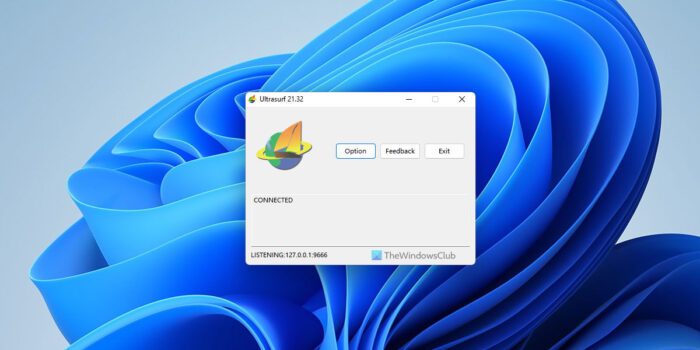
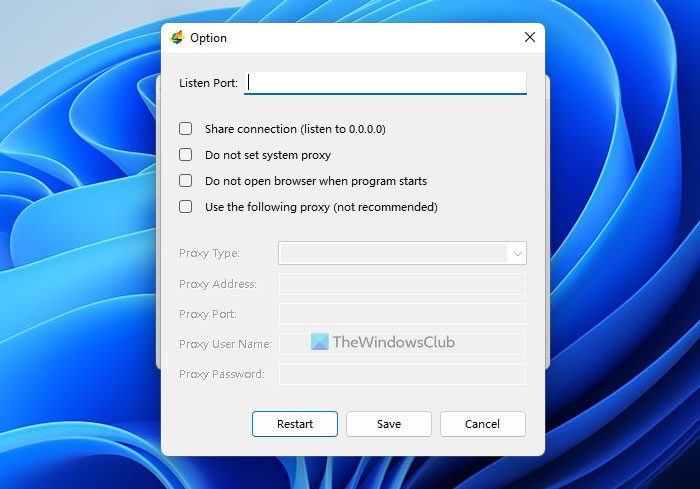
Though the name sounds more like a browser, it is a software that employs Internet Explorer for browsing – after hiding your IP address. Though it works with other browsers as well, it opens IE when you launch UltraSurf. You can turn off this feature using the UltraSurf Control Panel (See image below: options are self-explanatory).
The home page of UltraSurf says that it was designed to help people of countries like China, where the Internet is heavily censored. Since they cannot get to most of the social networking sites and International news websites, UltraSurf came into existence to provide them with an on-demand proxy. Since this proxy is established each time you connect to the Internet (given that Ultra-Surf is set up as a startup program), it allows you to bypass any kind of Internet censorship – allowing you to view blocked websites.
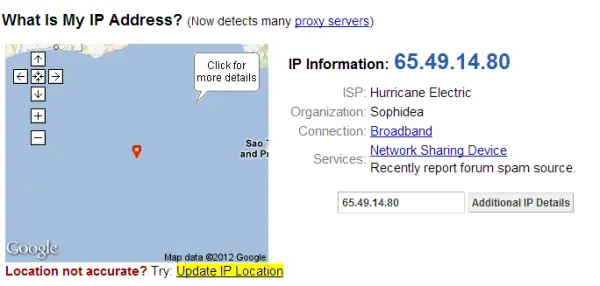
I searched my IP after launching UltraSurf and found the result as shown in the following image. The IP masking part does work!
It also says that though the original target of Ultra Surf was China residents, people across the world have recognized the kind of security it provides and use it to protect both their identity and privacy on the Internet.
In other words, if you use Ultra Surf to blog about anything, no authorities can find out who blogged as the IP would be different. You must, however, be using a public blogging service. In case your blog on a custom domain, it is easy for authorities to find out your identity by contacting your registrar whose information is always visible in WHOIS search.
How To Use UltraSurf For Best Protection
The best thing here is that you do not have to install it. When you download it, you get it as a ZIP file. You can extract the ZIP anywhere to your hard disk and even copy it to your Pen Drive. Carry the Pen Drive to a cyber coffee, copy the software to the desktop, launch it and perform the tasks you wish to do: send emails anonymously, a blog from behind a firewall and more. Do you want to get into war reporting?!
After you are done with your work, remove the program from cyber café’s desktop to erase any traces of you using a Proxy software. This is just like TOR, only that the TOR network is much stronger allowing you to change proxies to any country you wish.
How does UltraSurf work?
When you click on the file after extracting it, you get a folder named utmp – which – I suppose contains temporary files. These files do not have any extension and are about 1KB each. I opened a few of them using NotePad and Microsoft Word. They did not make any sense until I selected Taiwan Wang as language, which then showed some Chinese symbols.
When you delete the UltraSurf folder after usage at public cybercafes, make sure you shred the utmp folder too. If you are in a country where blogging is risky or if you are reporting anonymously, you should not simply delete files and folders. Use shredders to erase files permanently and remove traces in case of risky anonymous reporting and blogging.
Problem or rather, the advantage of UltraSurf is that you won’t get a Startup Menu entry or Desktop icon. Remember that you did not have to install it. You need to remember the location where you unzipped it. Each time you wish to start the program, you have to navigate to the program and open it. You can create a desktop shortcut by right-clicking on the program icon and selecting “Send To” > Desktop.
Though it is fine for casual use, a desktop shortcut is not recommended for risk blogging and anonymous reporting in which case; you would be secure erasing the entire UltraSurf folder after each use. At this point, I would like to bring your attention to a reporter who reported from Libya anonymously. I am not sure how she got caught, but the result was her elimination – and the TV Channel she worked for, had nothing to say about her. If you are in such a job or are risk-blogging, using tools like TOR helps more than anything else.
UltraSurf is more about protecting your privacy, and it does not keep on changing your IP address during the current session. It means you have to be real quick in completing tasks. There are some programs designed to provide more security by changing your IP address every few minutes while you are working. Such a program makes it impossible to trace who is blogging and from where.
UltraSurf does provide a fake IP address per session. If you wish to change your IP address when in the middle of composing a mail or blogging, close and restart the program as it won’t change it on its own when being used. TOR is better in this case, and even FreeGate comes on top of UltraSurf in my list of identity protectors.
If all you need is encryption and simply privacy, UltraSurf is good for you. You get the option to turn off the Internet Explorer using the UltraSurf Control Panel Options. You also get to select from three different servers of UltraSurf in case you need to get better speed for browsing.
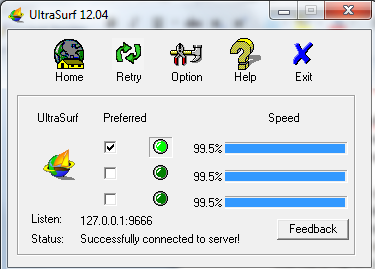
The highlight of the program is a golden lock that appears over the system tray when you open UltraSurf and stays there until you close UltraSurf. When you quit UltraSurf, you get the option of keeping Internet Explorer open. Alternatively, you can ask UltraSurf to close IE before quitting.
I do not know the exact use of that golden lock over the system tray. I can only guess that it is placed there to make it clear that UltraSurf is running. It does provide shortcuts to options, help and quit but then, the taskbar icon is always there, and it too takes you to the control panel having the same options. Maybe the UltraSurf authorities can shed some light on the usage of the icon.
My Verdict
UltraSurf is good for protecting privacy and handy too, as you can take it anywhere on your pen drives. It may also help with anonymous reporting and risk-blogging to some extent, but do not count on it if your kind of blogging and reporting poses a risk to your life. Protecting privacy is something very little compared to identity protection. In the latter case, you need many more additional steps to keep your identity hidden from authorities: using portable proxies and browsers, offline composing, shredding of files on local disks after usage. In short, identity protection is all about safe operations while removing all traces of that operation from computers – be it private or public.
Scope For Improvement:
- Incorporating a system of changing IP addresses randomly even while the session is in progress.
- Alternatively, allow users to select the proxies manually to change them while the session is still in progress.
Otherwise, the program is excellent!
Link of Countries Implementing Internet Censorship
Below is a rough list of countries that I compiled after researching a little. Many of these countries censor bad or violent websites. Though I believe such sites should be taken care of by people using different tools, like the Family Safety Center in Windows, many governments take over the role of Internet Nanny.
Among other types of censorship is a blackout of news – for good or for bad; altering news and events to highlight or suppress something; slowing down the Internet deliberately so that you cannot view videos or audios that require higher speeds.
Among the countries known for Internet censorship are:
- China (topping the list with different types of censorship),
- Myanmar (blocks opposition and human rights websites)
- Iran (blocking the Internet as a whole to create its own version of the Internet; I don’t know if it will be successful, but it is trying);
- Saudi Arabia (filters Internet through a custom-made software that blocks anything against the government)
- India (manipulation of news and events; blocking social media accounts, blogs, and websites that act against the government of India.
I will come up with an article with a complete list of countries implementing censorship of what is called freedom of speech. The Anonymous Group has been actively involved in protesting against such censorships, but ultimately, it is the federal authorities who have the upper hand given the amount of power they hold.
Stay safe!
Is UltraSurf trustworthy?
Yes, UltraSurf is a reliable, safe, and secure application that you can use on your Windows computer. It works like a VPN on your PC. In other words, it redirects your incoming and outgoing traffic to a tunnel, allowing users to browse the internet anonymously. For your information, it works flawlessly on Windows 11 and Windows 10.
What is UltraSurf proxy used for?
You can use UltraSurf for almost anything. From accessing blocked content on the internet to opening regionally blocked websites, you can do almost all the things with the help of UltraSurf. Before getting started with this proxy app, you must know that it is a proxy client. It implies that you must have valid proxy settings in order to use this app.
NOTE: We are not related to The Anonymous Group in any way except that their material helped the author learn about staying safe and secure online.