If you work in or own an enterprise, then you need to know that there is always a high risk of cyber-attacks & scams taking place. Email Scams are the most common among them. Phishing comes in many flavors like Tabnabbing, Spear Phishing as well as Vishing and Smishing. A few days back, we took a look at Pharming online frauds – today we will take a look at Whaling Scams which is the emerging cyber-security threat.
What are Whaling scams?
In Whaling scams, you are targeted usually by email – it is a specialized Phishing scam. The attacker studies your online activity and obtains useful information about you from other sources. And that information is used to create a professional-looking personalized e-mail. Seeing an official email can cause you to drop your defenses and you are very likely to trust such an email. The idea is to obtain information from you for further fraudulent activities.
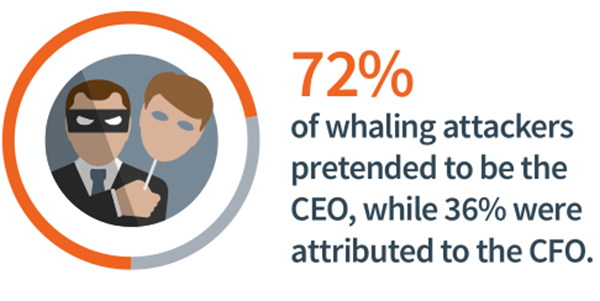
Now you have to realize that there is a thin line of difference between Whaling and Spear Phishing. Whaling typically targets high-level executives, whereas the latter scam targets employees of a company and customers of a company generally. It is called Whaling because the targets are usually large or important. And so Whales are chosen because of their authority and access within an organization.
How does Whaling work, and why are you targeted?
Most of the targets are usually businessmen, entrepreneurs, CEOs, and corporate employees. The targets are usually business specific and attacks are planned for the purpose of obtaining any sensitive information about the activities of an organization.
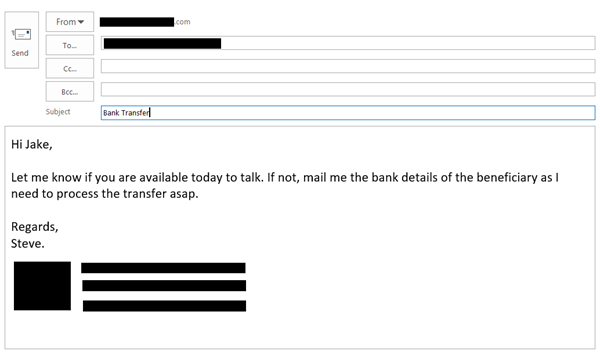
These kinds of socially engineered attacks are very difficult to identify and people usually end up giving data to such scammers. The scammer sends a personalized email from an address you may be familiar with. The scammer may mimic to be your boss or another friendly organization. Or he/she may mimic as your financial consultant or your lawyer. The content of the email is mostly attention seeking so that you may reply promptly and there is the least chance of them getting caught.
The email might require you to transfer some money as a payment to a due bill or it may ask you for some company data that is required at a head office. Or it may ask personal details about the employees of the organization.
The scammer or the attacker has already researched you to create a personalized email for you. And the research may be based on your online activities or upon any information obtained from other sources. Whaling emails just seem normal and perfect and that is the only reason people fall into the trap. The names, logos, and other information used in the email may be real or not. But it is presented in such a way that normal people cannot mark a difference between these emails.
Also, the email address of the sender or the website mentioned is similar to someone you may know. The attachments may or may not be malicious. The sole purpose of these scams is to convince you that the email is completely normal and requires urgent action. And when you follow the instructions in the email, you end up leaking out some confidential data to an unauthorized person or website.
How to stay protected from Whaling attacks
You have to learn to identify Phishing Attacks to know more about protection from phishing in general so that you can avoid Phishing scams.
The key to staying protected is to stay attentive. Read all your work-related emails end to end and keep an eye on something fishy. If you just felt that there is something wrong with the email, contact the organization from which the email is said to be.
1] Verify the sender’s email and then only respond to emails. Usually, the websites or email addresses from where you are receiving emails are almost identical to normal email addresses that you may know. An ‘o’ may be replaced with a ‘0’ (zero) or there may be two ‘ss’ instead of one ‘s’. These kinds of errors are easily overlooked by the human eye, and these form the basis of such attacks.
2] If the email requires some urgent action, then you must look carefully and then take the decision. If there are any outbound website links, verify their address before supplying any information to that website. Also, check for the padlock sign or verify the website’s certificate.
3] Do not provide any financial or contact details to any website or email. Know when to trust a website, take precautions before clicking on any web links and follow the basic internet usage safety norms.
4] Have proper antivirus, and firewall software protecting your computer and do not download any attachments from any of these emails. RAR/7z or any other executable files are most suspected of containing any malware or Trojans. Regularly change passwords and create a backup of important documents at a secure location.
5] Completely destroy your physical documents before disposing of them so that they cannot provide any information about you and your organization.
Whaling attack examples
While you can find a ton of such scam stories online. Even major companies like Snapchat and Seagate have fallen into the traps of these scams. Last year, a high-rank employee of Snapchat was a victim of a scam where an email impersonating the CEO of the company inquired about the payroll of the employees. Take a look at some examples:
- Seagate: A successful whaling attack landed thieves up to 10,000 W-2 tax documents for all current and past employees.
- Snapchat: An employee fell for an email impersonating a request from CEO Evan Spiegel and compromised payroll data for 700 employees.
- FACC: The Austrian aircraft industry supplier lost 50 million euros due to a whaling attack.
- Ubiquiti Networks: This networking tech company suffered a $39.1 million loss as a result of a whaling attack.
- Weight Watchers International: A whaling email allowed thieves to obtain tax data for nearly 450 current and former employees.
Already Scammed?
Do you think that you’ve been a victim of a Whaling scam? Immediately inform the head of your organization and seek legal help. If you provided them with any bank details or any sort of passwords, change them immediately. Consult a cyber-security expert to track back the path and know who the attacker was. Seek out for legal help and consult a lawyer.
There are various online services available where you can report such scams. Please report such scams so that their activity can be disrupted and more people are not affected.
If you are interested in knowing more, there is this excellent eBook titled Whaling, Anatomy of an attack, which you can download free.
Protect yourself, your employees and your organization from such frauds and online scams. Spread the word and help your colleagues, friends, and family stay protected.
Read here about the most common Online and Email scams & frauds.
Very good report!