To help troubleshoot problems, the Event Viewer, native to the Windows operating system, shows event logs of system and application messages which include errors, warnings, and information about certain events that can be analyzed by the administrator to take the necessary actions. In this post, we discuss the Audit Success or Audit Failure in Event Viewer.
What is Audit Success or Audit Failure in Event Viewer
In Event Viewer, Audit Success is an event that records an audited security access attempt that is successful, whereas Audit Failure is an event that records an audited security access attempt that fails. We will discuss this topic under the following subheadings:
- Audit Policies
- Enable Audit Policies
- Use Event Viewer to find the source of failed or successful attempts
- Alternatives to using Event Viewer
Let’s see these in detail.
Audit Policies
An audit policy defines the types of events that are recorded in the Security logs and these policies generate events, which can either be Success events or Failure events. All audit policies will generate Success events; however, only a few of them will generate Failure events. Two types of audit policies can be configured viz:
- Basic Audit Policy has 9 audit policy categories and 50 audit policy subcategories that can be enabled or disabled per requirement. Below is a list of the 9 audit policy categories.
- Audit account logon events
- Audit logon events
- Audit account management
- Audit directory service access
- Audit object access
- Audit policy change
- Audit privilege use
- Audit process tracking
- Audit system events. This policy setting determines whether to audit when a user restarts or shuts down the computer or when an event occurs that affects either the system’s security or the security log. For more information and the related logon events, refer to the Microsoft documentation at learn.microsoft.com/basic-audit-system-events.
- Advanced Audit Policy which has 53 categories, ergo recommended as you can be able to define a more granular audit policy and log only the events that are relevant which is particularly helpful if generating a large number of logs.
Audit failures are typically generated when a logon request fails, although they can also be generated by changes to accounts, objects, policies, privileges, and other system events. The two most common events are;
- Event ID 4771: Kerberos pre-authentication failed. This event is only generated on domain controllers and is not generated if the Do not require Kerberos preauthentication option is set for the account. For more information about this Event and how to resolve this problem, refer to the Microsoft documentation.
- Event ID 4625: An account failed to log on. This event is generated when an account logon attempt failed, assuming the user was already locked out. For more information about this Event and how to resolve this problem, refer to the Microsoft documentation.
Read: How to check the Shutdown and Startup Log in Windows
Enable Audit Policies
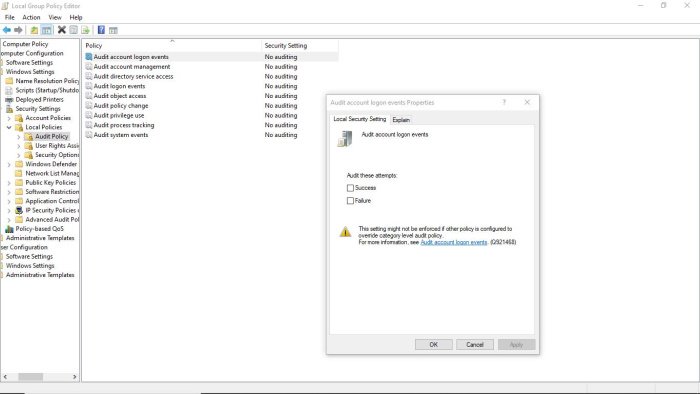
You can enable audit policies on the client or server machines via Local Group Policy Editor or Group Policy Management Console or Local Security Policy Editor. On a Windows server, on your domain, either create a new group policy object or you can edit an existing GPO.
On a client or server machine, in the Group Policy Editor, navigate to the path below:
Computer Configuration > Windows Settings > Security Settings > Local Policies > Audit Policy
On a client or server machine, in Local Security Policy, navigate to the path below:
Security Settings > Local Policies > Audit Policy
- In Audit policies, on the right pane double-click the policy you want to edit its properties.
- In the properties panel, you can enable the policy for Success or Failure per your requirement.
Read: How to reset all Local Group Policy settings to default in Windows
Use Event Viewer to find the source of failed or successful attempts
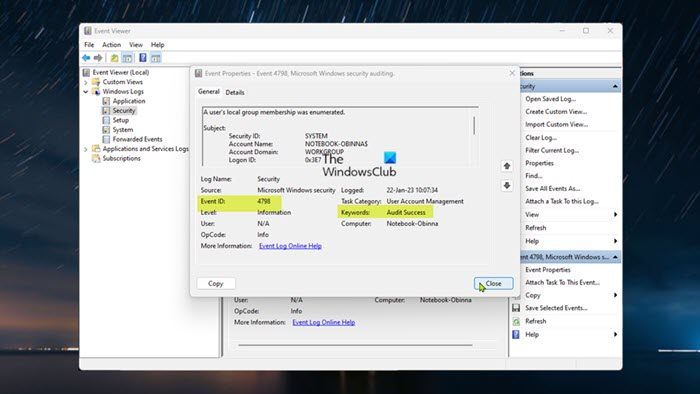
Administrators and regular users can open the Event Viewer on a local or remote machine, with the appropriate permission. The Event Viewer will now record an event every time there is a failed or successful event whether on a client machine or in the domain on a server machine. The Event ID that is triggered when a failed or successful event is registered differs (see the Audit Policies section above). You can navigate to Event Viewer > Windows Logs > Security. The pane in the center lists all the events that have been set up for auditing. You will have to go through events registered to look for failed or successful attempts. Once you find them, you can right-click on the event and select Event Properties for more details.
Read: Use Event Viewer to check unauthorized use of Windows computer
Alternatives to using Event Viewer
As an alternative to using Event Viewer, there are several third-party Event Log Manager software that can be used to aggregate and correlate event data from a wide range of sources, including cloud-based services. A SIEM solution is the better option if there’s a need to collect and analyze data from firewalls, Intrusion Prevention Systems (IPS), devices, applications, switches, routers, servers, etcetera.
I hope you find this post informative enough!
Now read: How to enable or disable Protected Event Logging in Windows
Why is it important to audit both successful and failed access attempts?
It is vital to audit logon events whether successful or failed to detect intrusion attempts because user logon auditing is the only way to detect all unauthorized attempts to log in to a domain. Logoff events are not tracked on domain controllers. It is also equally important to audit failed attempts to access files as an audit entry is generated each time any user unsuccessfully attempts to access a file system object that has a matching SACL. These events are essential for tracking activity for file objects that are sensitive or valuable and require extra monitoring.
Read: Harden Windows Login Password Policy & Account Lockout Policy
How do I enable audit failure logs in Active Directory?
To enable audit failure logs in Active Directory, simply right-click the Active Directory object you want to audit, and then select Properties. Select the Security tab, and then select Advanced. Select the Auditing tab, and then select Add. To view audit logs in Active Directory, click Start > System security > Administrative tools > Event viewer. In Active Directory, auditing is the process of collecting and analyzing AD objects and Group Policy data to proactively improve security, promptly detect and respond to threats, and keep IT operations running smoothly.
Read: Event ID 1101, Audit events have been dropped by the transport. 0.
Leave a Reply