Windows 11/10 and Windows Server include a command-line tool called Audit Policy Program, AuditPol.exe, situated in the System32 folder that allows you to manage and audit policy sub-category settings in a more precise way.
Setting audit policy at the category level will override the new subcategory audit policy feature. A new registry value introduced in Windows Vista, SCENoApplyLegacyAuditPolicy, allows audit policy to be managed by using subcategories without requiring a change to Group Policy. This registry value can be set to prevent the application of category-level audit policy from Group Policy and from the Local Security Policy administrative tool.
What is AuditPol used for?
Auditpol.exe is a command-line utility in Windows OS that can be used to configure and manage audit policy settings from an elevated command prompt. It allows you to manage and audit policy sub-category settings in a more precise way.
How to enable AuditPol in Windows 11/10?
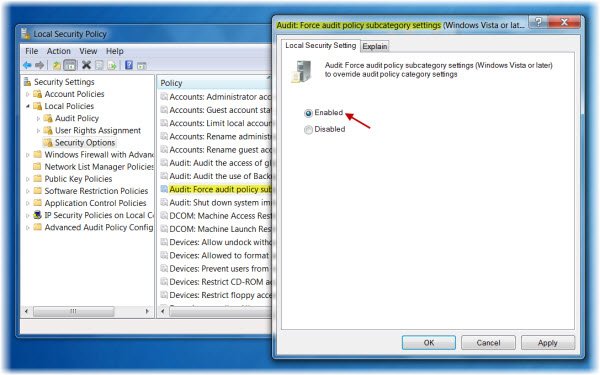
If you wish to enable this AuditPol option:
- Open Local Security Policy > Local Policies > Security Options.
- Now in the right panel, double-click on Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings.
- Select Enabled > Apply/OK.
AuditPol command line switches
AuditPol has several switches that allow you to display, set, clear, backup, and restore settings. Especially, it can be used to:
- Set and query a system audit policy.
- Set and query a per-user audit policy.
- Set and query auditing options.
- Set and query the security descriptor used to delegate access to an audit policy.
- Report or back up an audit policy to a comma-separated value (CSV) text file.
- Load an audit policy from a CSV text file.
- Configure global resource SACLs.
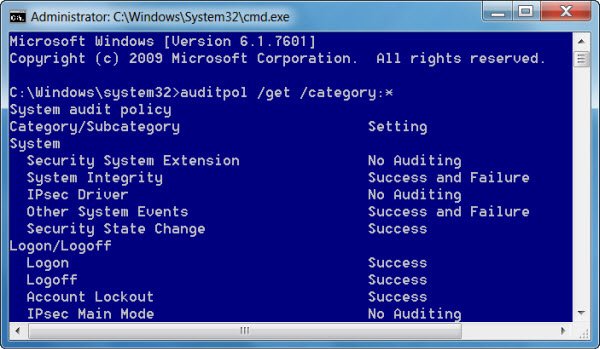
If you open a command prompt as an administrator, you can use AuditPol to view the defined auditing settings by running:
auditpol /get /category:*
A point to be noted is that while viewing audit policy settings with AuditPol and the Local Security Policy viz secpol.msc, the settings may show different results. KB2573113 explains the reason for this:
AuditPol directly calls authorization APIs to implement the changes to the granular audit policy. Secpol.msc manipulates the Local Group Policy Object, which results in writing the changes to system32\GroupPolicy\Machine\Microsoft\Windows NT\Audit\Audit.csv. The settings saved to the .csv file are not applied directly to the system at the time of modification, but are instead written to the file and read later by the client-side extension (CSE). At the next group policy refresh cycle, the CSE applies the modifications that are present in the .csv file. Secpol.msc displays what is set in the local GPO. There is no “effective settings” view in secpol.msc that will merge granular AuditPol settings and what is defined locally as seen with secpol.msc.
For more details visit AuditPol on TechNet.