This post explains what is a Rootkit virus in cybersecurity. While it is possible to hide malware in a way that will fool even the traditional antivirus/antispyware products, most malware programs already use rootkits to hide deep on your Windows PC … and they are getting more dangerous! The DL3 rootkit is one of the most advanced rootkits ever seen in the wild. The rootkit was stable and could infect 32-bit Windows operating systems, although administrator rights were needed to install the infection in the system. But TDL3 has now been updated and can infect even 64-bit versions of Windows!
What is a Rootkit

A Rootkit virus is a stealth type of malware that is designed to hide the existence of certain processes or programs on your computer from regular detection methods so as to allow it or another malicious process privileged access to your computer.
Rootkits for Windows are typically used to hide malicious software from, for example, an antivirus program. It is used for malicious purposes by viruses, worms, backdoors, and spyware. A virus combined with a rootkit produces what is known as full stealth viruses. Rootkits are more common in the spyware field, and they are now also becoming more commonly used by virus authors as well.
They are now an emerging type of Super Spyware that hides effectively & impacts the operating system kernel directly. They are used to hide the presence of malicious objects like trojans or keyloggers on your computer. If a threat uses rootkit technology to hide, finding the malware on your PC is very hard.
A well-known example of a rootkit is NTRootkit, which targeted Windows OS as one of the first malicious rootkits. Another example is HackerDefender, a Trojan that altered the OS at a low level of function calls. Additionally, Machiavelli was the first rootkit targeting Mac OS X appearing in 2009.
Rootkits in themselves are not dangerous. Their only purpose is to hide software and the traces left behind in the operating system, whether normal software or malware programs.
There are basically three different types of Rootkit. The first type, the “Kernel Rootkits” usually add their own code to parts of the operating system core, whereas the second kind, the “User-mode Rootkits” are specially targeted to Windows to start up normally during the system start-up or injected into the system by a so-called “Dropper”. The third type is MBR Rootkits or Bootkits.
The primary objective of rootkits is to effectively conceal and maintain the presence of malware on a system, allowing it to operate with elevated privileges. This includes hiding files, processes, registry keys, user accounts, and even system registries during system startup. Rootkits play a crucial role in masking malware payloads and ensuring their persistence on the compromised system.
When you find your AntiVirus & AntiSpyware failing, you may need to take the help of a good Anti-Rootkit Utility.
RootkitRevealer from Microsoft Sysinternals is an advanced rootkit detection utility. Its output lists Registry and file system API discrepancies that may indicate the presence of a user-mode or kernel-mode rootkit.

Microsoft Malware Protection Center Threat Report on Rootkits
Microsoft Malware Protection Center has released its Threat Report on Rootkits. The report examines one of the more insidious types of malware threatening organizations and individuals today — the rootkit. The report examines how attackers use rootkits and how rootkits function on affected computers. Here is a gist of the report, starting with what are Rootkits – for the beginner.
Rootkit is a set of tools that an attacker or a malware creator uses to gain control over any exposed/unsecured system, which otherwise is normally reserved for a system administrator. In recent years, the term ‘ROOTKIT’ or ‘ROOTKIT FUNCTIONALITY’ has been replaced by MALWARE – a program designed to have undesirable effects on a healthy computer. Malware’s prime function is to withdraw valuable data and other resources from a user’s computer secretly and provide it to the attacker, thereby giving him complete control over the compromised computer. Moreover, they are difficult to detect and remove and can remain hidden for extended periods, possibly years, if gone unnoticed.
So naturally, the symptoms of a compromised computer must be masked and considered before the outcome proves fatal. Particularly, more stringent security measures should be taken to uncover the attack. But, as mentioned, once these rootkits/malware are installed, their stealth capabilities make it difficult to remove it and its components that it might download. For this reason, Microsoft has created a report on ROOTKITS.
The 16-page report outlines how an attacker uses rootkits and how these rootkits function on affected computers.
The sole purpose of the report is to identify and closely examine potent malware threatening many organizations, computer users in particular. It also mentions some of the prevalent malware families and brings into light the method the attackers use to install these rootkits for their own selfish purposes on healthy systems. In the remainder of the report, you will find experts making some recommendations to help users mitigate the threat from rootkits.
Types of Rootkits
There are many places where malware can install itself into an operating system. So, mostly the type of rootkit is determined by its location where it performs its subversion of the execution path. This includes:
- User Mode Rootkits
- Kernel Mode Rootkits
- MBR Rootkits/bootkits
The possible effect of a kernel-mode rootkit compromise is illustrated via a screenshot below.
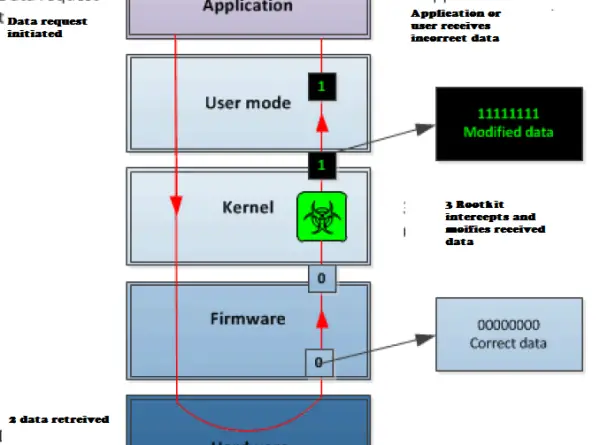
The third type, modify the Master Boot Record to gain control of the system and start the process of loading the earliest possible point in the boot sequence3. It hides files, registry modifications, evidence of network connections as well as other possible indicators that can indicate its presence.
Notable Malware families that use Rootkit functionality
- Win32/Sinowal13 – A multi-component family of malware that tries to steal sensitive data such as user names and passwords for different systems. This includes attempting to steal authentication details for a variety of FTP, HTTP, and email accounts, as well as credentials used for online banking and other financial transactions.
- Win32/Cutwail15 – A Trojan that downloads and executes arbitrary files. The downloaded files may be executed from disk or injected directly into other processes. While the functionality of the downloaded files is variable, Cutwail usually downloads other components that send spam. It uses a kernel-mode rootkit and installs several device drivers to hide its components from affected users.
- Win32/Rustock – A multi-component family of rootkit-enabled backdoor Trojans initially developed to aid in the distribution of “spam” email through a botnet. A botnet is a large attacker-controlled network of compromised computers.
Protection against rootkits
Preventing the installation of rootkits is the most effective method to avoid infection by rootkits. For this, investing in protective technologies such as anti-virus and firewall products is necessary. Such products should take a comprehensive approach to protection by using traditional signature-based detection, heuristic detection, dynamic and responsive signature capability and behavior monitoring.
All these signature sets should be kept up to date using an automated update mechanism. Microsoft antivirus solutions include a number of technologies designed specifically to mitigate rootkits, including live kernel behavior monitoring that detects and reports on attempts to modify an affected system’s kernel, and direct file system parsing that facilitates the identification and removal of hidden drivers.
If a system is found compromised then an additional tool that allows you to boot to a known good or trusted environment may prove useful as it may suggest some appropriate remediation measures.
Under such circumstances,
- The Standalone System Sweeper tool (part of the Microsoft Diagnostics and Recovery Toolset (DaRT)
- Windows Defender Offline may be useful.
For more information, you can download the PDF report from Microsoft Download Center.