Windows Applocker was introduced in Windows 7 and includes some new features in Windows 11/10. With AppLocker, an administrator can block or allow certain users or user groups from installing or using certain applications. You can use blacklisting rules or whitelisting rules to achieve this result. AppLocker helps administrators control which applications and files users can run. These include executable files, scripts, Windows Installer files, DLLs, Packaged apps, and Packaged app installers.
Windows AppLocker prevents users from installing or running applications
AppLocker helps administrators create rules to allow or deny specific applications based on criteria like file attributes, publisher names, file paths, and more. This can be useful for preventing unauthorized software from running, ensuring compliance with licensing agreements, and maintaining a standard software environment across an organization
In Windows 11 and Windows 11, Applocker has evolved and lets you block legacy as well as Windows Store apps.
How to use AppLocker in Windows 11/10
To prevent users from installing or running Windows Store Apps with AppLocker in Windows, type secpol.msc in Run and hit Enter to open the Local Security Policy Editor.
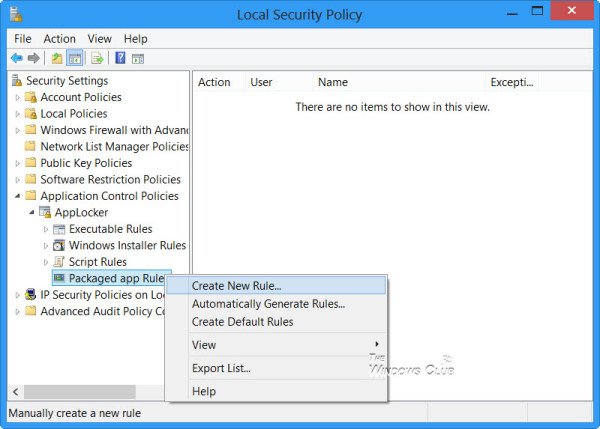
In the console tree, navigate to Security Settings > Application Control Policies > AppLocker.
Select where you want to create the rule. This could be for an Executable, Windows Installer, Scripts or in the case of Windows 10, a Windows Store packaged app.
Let us say you want to create a rule for Packaged apps. Right-click on Packaged apps and select Create Rule. You will see a Before You Begin page.
Click Next to reach the Permissions page.
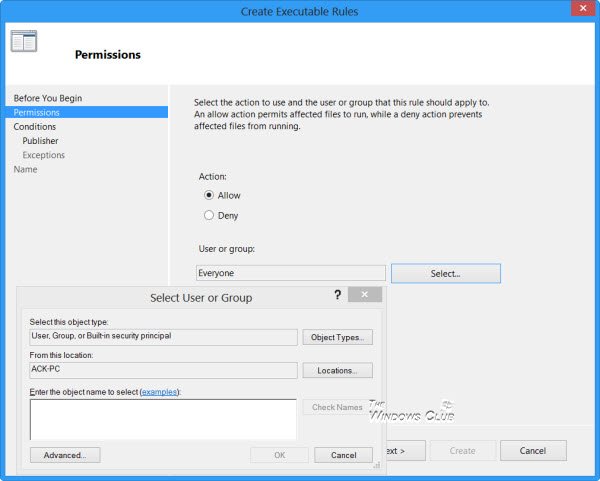
On this page, select the action viz. Allow or Deny and the User or User Group you want the rule to apply. Click Next to reach the Conditions page.
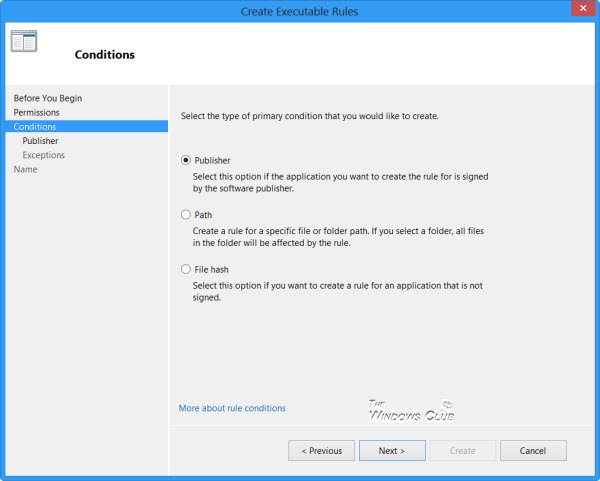
Select how you want to create the rules – base on Publishers, File Path, or Has. I have selected Publishers, which is the default.
Click Next to reach the Publisher page.
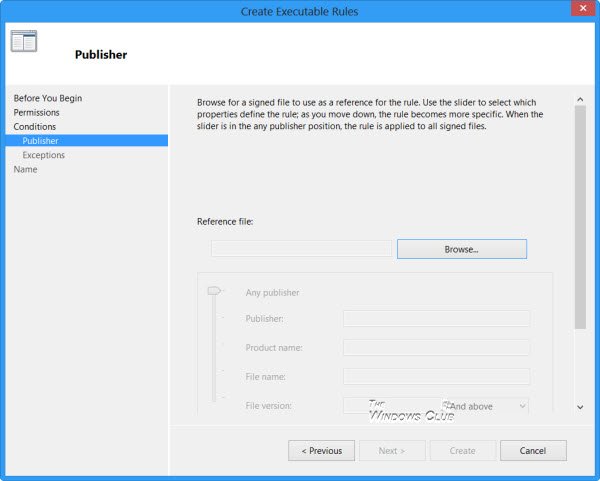
Here you can browse for and select a Reference for the Packaged app and set the Scope for the rule.
Settings for Scope include:
- Applies to Any publisher
- Applies to a specific Publisher
- Applies to a Package name
- Applies to a Package version
- Applying custom values to the rule
The options for Reference include:
- Use an installed packaged app as a reference
- Use a packaged app installer as a reference
After making your selections, click Next again.
If you wish, on the Exceptions page you may specify conditions when to exclude the rules, and on the Name and Description page, you can accept the automatically generated rule name or type a new rule name, and click Create. You can read more about creating rules for Packaged Windows Store apps here at Technet.
Do note that for the AppLocker to work on your system, the Application Identity service must be running on your computer. Also, the Group Policy Client service, gpsvc, required for running AppLOcker, is disabled by default on Windows RT, so you may have to enable it via services.msc.
Difference between AppLocker in Windows 11/10 & Windows 7
The AppLocker in Windows 11/10 allows you to also create rules for Packaged Windows Store apps. Moreover, the Windows 11/10 AppLocker rules can also additionally control the .mst and .appx file formats.
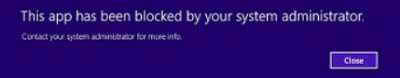
This app has been blocked by your system administrator
If as a user, you find that when you start any Windows Store app (or traditional software) you receive the message: This app has been blocked by your system administrator, you will have to contact your Administrator and ask him to create rules to allow you to use (or install) the software.
To create and enforce AppLocker rules, the computer must be running Windows 11/10, Windows 8 Enterprise, Windows 7 Ultimate, Windows 7 Enterprise, Windows Server 2008 R2 or Windows Server 2012.
You can also block users from installing or running programs using the Registry or Group Policy.
PS: Windows Program Blocker is a free App or Application blocker software to block software from running.
Please enable Applocker for Windows 8 Pro!
Many thanks for the well-written article. In MCSA 70-687, there was a question with four answers, which applocker rule should use to prevent windows store apps. all the four rules were as four answers. I was confused which one to go for. if you have mentioned that windows store apps format is .appx and packaged app rule is the one can block .appx, the article would have been more clear. Anyway thanks for ur nice article.
In an ideal world, Applocker should have been included for all versions of Windows. A good alternative would be SecureAPlus and it skips all the complications inherent with the way Windows is applying it.