When you connect to a domain network or a company network, then Windows Firewall switches to a domain profile. The profile applies to networks where the host system can authenticate to a domain controller. The other two profiles are private and public. Now it may so happen that when you connect to a domain, the Windows Firewall profile does not always switch to Domain. It usually occurs when you are using a third-party virtual private network (VPN) client to connect to a domain network. In this post, we will offer a solution that will make sure the Windows Firewall switches the profile in this situation.
Windows Firewall not recognizing Domain network
It may happen that your Windows Firewall profile does not always switch to Domain when you use a third-party VPN client. The reason behind the failure to change to a domain profile is the time lag in some third-party VPN clients. The delay occurs when the client adds the necessary routes to the domain network. VPNs change the IP address whenever you switch to a new server or make a new connection. As a permanent solution, Microsoft recommends that the VPNs use callback APIs to add routes as soon as the VPN adapter arrives at Windows. These are the three API that a VPN should use for Windows.
- NotifyUnicastIpAddressChange: Alerts callers of any changes to any IP address, including changes in DAD state.
- NotifyIpInterfaceChange: Registers a callback for notification of changes to all IP interfaces.
- NotifyAddrChanget: Notifies the user about address changes.
Workaround to switch Firewall to Domain Profile
If your VPN doesn’t offer such features, and you cannot switch to a different VPN, then here is a workaround. You or the IT admin can choose to disable negative cache to help the NLA service when it retries domain detection.

If you need to create any of these keys, right-click on any the appropriate pane, and select new and then the type of keys. Here you need right-click on the right pane and then select new DWORD.
Add or change Negative Cache Period
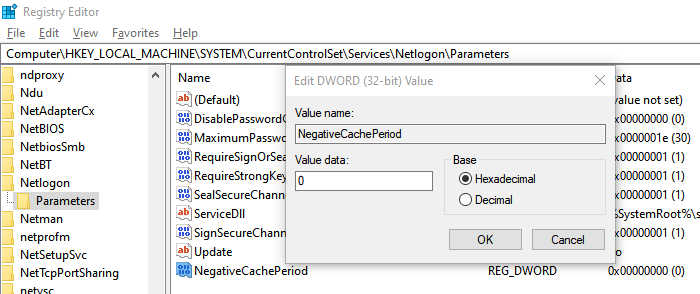
Disable Domain Discovery negative cache by adding the NegativeCachePeriod registry key to the following subkey
- Open Registry Editor and navigate to the following key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NetLogon\Parameters
- Change or create the following DWORD with the suggested value
- Name: NegativeCachePeriod
- Type: REG_DWORD
- Value Data: 0
The default value of the negative cache is 45 seconds. Setting it to zero will disable caching.
Add or change the Max Negative Cache TTL
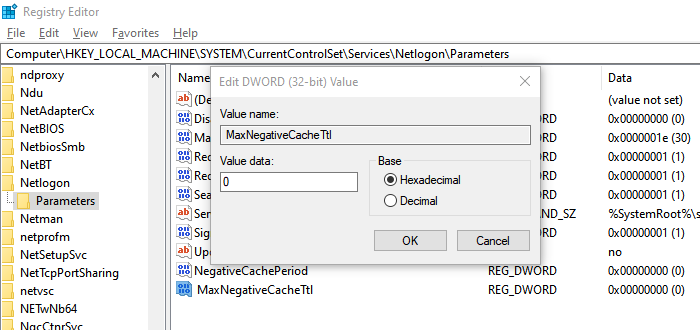
If the issue is still not resolved, the next step is to disable DNS caching. You can achieve this by adding the MaxNegativeCacheTtl registry key.
- Open Registry Editor
- Navigate to the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters
- Change or create the following DWORD with the suggested value
- Name: MaxNegativeCacheTtl
- Type: REG_DWORD
- Value Data: 0
The default value of the max negative cache is five seconds. When you set it to zero, it will disable caching.
I hope the workaround helped the Windows Firewall profile switch to the Domain profile when you use a third-party VPN client. Unless your VPN client supports the callback API to notify you about changes, the Registry changes should help.
Leave a Reply