To protect your computer from unauthorized use, Windows 11/10 provides a facility to protect it using a password. A strong password is thus the first line of defense as far as your computer’s security is concerned.
If you wish to enhance the security of your Windows computer, you can strengthen the Windows Login Password Policy using the built-in Local Security Policy or Secpol.msc. Nested among its many settings is a useful set of options that will allow you to configure the Password Policy for your computer.
Harden Windows Login Password Policy
To open and use the Local Security Policy open Run, type secpol.msc and hit Enter. In the left pane, click on Account Policies > Password Policy. In the right pane, you see settings for configuring the Password Policy. Alternatively, you can open gpedit.msc and navigate to:
Local Computer Policy\Computer Configuration\Windows Settings\Security Settings\Account Policies\
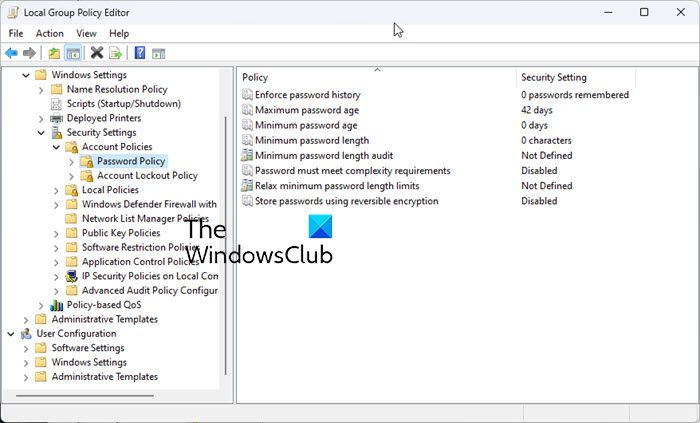
These are some parameters that you can configure. Double-click on each to open their Properties box. From the drop-down menu you can choose and select the desired option. Once you have set them, do not forget to click on Apply/OK.
1] Enforce Password History
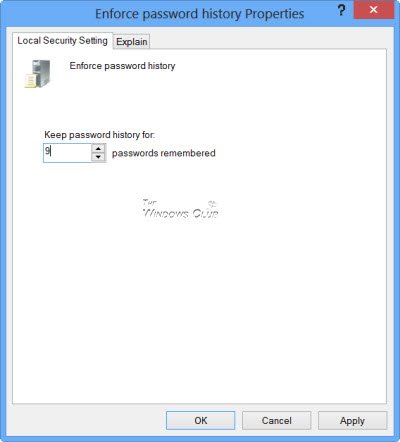
Using this policy, you can ensure that users do not use old passwords again and again after a while. This setting determines the number of unique new passwords that have to be associated with a user account before an old password can be reused. You can set any value between. The default is 24 on domain controllers and 0 on stand-alone servers.
2] Maximum password age
You can force users to change their passwords after a particular number of days. You can set passwords to expire after a number of days between 1 and 999, or you can specify that passwords never expire by setting the number of days to 0. The default is set at 42 days.
3] Minimum password age
Here you can enforce the minimum period that any password must be used before it can be changed. You can set a value between 1 and 998 days, or you can allow changes immediately by setting the number of days to 0. The default is 1 on domain controllers and 0 on stand-alone servers. While this setting may not go towards strengthening your password policy, if you wish to prevent users from changing passwords too frequently, you may set this policy.
4] Minimum password length
This is an important setting and you may want to enforce it to prevent hack attempts. You can set a value of between 1 and 14 characters, or you can establish that no password is required by setting the number of characters to 0. The default is 7 on domain controllers and 0 on stand-alone servers.
You can also choose to Enable two more settings if you wish. Once you have opened their respective Properties boxes, select Enabled and Apply to enable the policy.
5] Minimum password length Audit
This security setting determines the minimum password length for which password length audit warning events are issued. This setting may be configured from 1 to 128. You should only enable and configure this setting when trying to determine the potential impact of increasing the minimum password length setting in your environment.
- If this setting is not defined, audit events will not be issued.
- If this setting is defined and is less than or equal to the minimum password length setting, audit events will not be issued.
- If this setting is defined and is greater than the minimum password length setting, and the length of a new account password is less than this setting, an audit event will be issued.
6] Password must meet complexity requirements
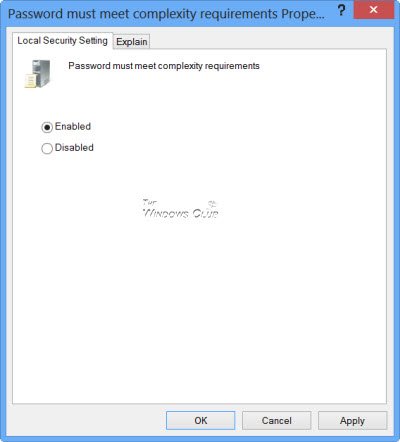
Another important setting you want to use as it will make passwords more complex and therefore difficult to compromise. If this policy is enabled, passwords must meet the following minimum requirements:
- Not contain the user’s account name or parts of the user’s full name that exceed two consecutive characters
- Be at least six characters in length Contain characters from three of the following four categories:
- English uppercase characters (A through Z)
- English lowercase characters (a through z)
- Base 10 digits (0 through 9)
- Non-alphabetic characters (for example, !, $, #, %)
7] Relax minimum password length limits
This setting controls whether the minimum password length setting can be increased beyond the legacy limit of 14.
- If this setting is not defined, minimum password length may be configured to a maximum of 14.
- If this setting is defined and disabled, minimum password length may be configured to a maximum of 14.
- If this setting is defined and enabled, minimum password length may be configured higher than 14.
8] Store passwords using reversible encryption
This security setting determines whether the operating system stores passwords using reversible encryption. Storing passwords using reversible encryption is essentially the same as storing plain-text versions of the passwords. For this reason, this policy should never be enabled unless application requirements outweigh the need to protect password information.
Read: How to customize the Password Policy in Windows.
Account Lockout Policy in Windows 11/10
To further strengthen the Password Policy, you can also set the lockout durations and thresholds, as this will stop potential hackers in their tracks after a particular number of failed attempts. To configure these settings, in the left pane, click on Account Lockout Policy.
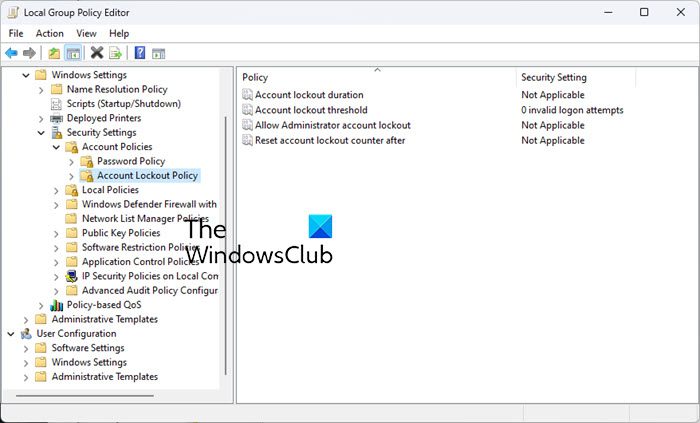
1] Account lockout duration
This security setting determines the number of minutes a locked-out account remains locked out before automatically becoming unlocked. The available range is from 0 minutes through 99,999 minutes. If you set the account lockout duration to 0, the account will be locked out until an administrator explicitly unlocks it. If an account lockout threshold is defined, the account lockout duration must be greater than or equal to the reset time.
Default: None, because this policy setting only has meaning when an Account lockout threshold is specified.
Using this setting, you can fix the number of minutes a locked-out account remains locked out before automatically becoming unlocked. You can set any figure between 0 minutes and 99,999 minutes. This policy has to set along with the Account lockout threshold policy.
2] Account lockout threshold

If you set this policy, you can control the number of invalid logins. The default is 0 but you can set a figure between 0 and 999 failed logon attempts.
Read: Restrict the number of Login attempts in Windows.
3] Allow Administrator account lockout
This security setting determines whether the built-in Administrator account is subject to account lockout policy.
Brute force attacks are one of the top three ways Windows machines are attacked today. To prevent further brute force attacks/attempts, Microsoft has started implementing account lockouts for Administrator accounts. Thus, Windows 11 now has a DEFAULT account lockout policy to mitigate RDP and other brute-force password vectors.
Read: How to block Brute force attacks on Windows Server
4] Reset account lockout counter after
This security setting determines the number of minutes that must elapse after a failed logon attempt before the failed logon attempt counter is reset to 0 bad login attempts. The available range is 1 minute to 99,999 minutes. This policy too has to set along with the Account lockout threshold policy.
Stay safe, stay secure!
Aware of AuditPol in Windows? If not, you might want to read about it.
How do I find my Windows login password?
You cannot unless you have noted it somewhere. Windows stores all account passwords hashed into Credential Manager; no one can view it in plaintext format. If you have forgotten your account password, you can ask your admin to reset it for you or sign in using a Microsoft account connected to the PC.
How do you reset your Microsoft account password to sign in to your computer?
You can either use another PC or Phone or click on the password text box below and select I forgot my password. Follow the steps to reset your password. Please select the correct user account, or else it will not work as expected.
Secpol.msc and also gpedit.msc are not available in Windows 7 Starter/Home Basic/Home Premium or Windows 8 standard Editions. Same actually goes for Vista and XP. These console plugins are only available in Pro or above versions.
Yes, I suppose I should have mentioned that. Thanks for mentioning it.
You’re welcome. It’s a good article.