What are Drive-by downloads? Drive-by download attacks occur when vulnerable computers get infected by just visiting a website. Findings from Microsoft Security Intelligence Report and many of its previous volumes reveal that Drive-by Exploits have become the top web security threat to worry about. Even the EU cybersecurity group, the European Network and Information Security Agency (ENISA) agrees.
What are Drive-by downloads?
It’s accepted that Drive-by download attacks remain many attackers’ favorite type of attack. This is because the attack can be easily launched by injecting malicious code into legitimate websites. Once injected, malicious code may exploit vulnerabilities in operating systems, web browsers, and web browser plugins such as Java, Adobe Reader, and Adobe Flash. The initial code that gets downloaded is usually small. But once it lands on your computer, it will contact another computer and pull the rest of the malicious coder to your system.
In short, vulnerable computers can be infected with malware simply by visiting such a website, without attempting to download anything. Such downloads happen without the person’s knowledge. These are called Drive-by downloads.
New data and findings have highlighted the relative prevalence of drive-by download sites, hosted on different web server platforms.
Certain representations made in the article via figures give a fair idea of the concentration of drive-by download pages in countries and regions throughout the world. Locations with relatively high concentrations of drive-by download URLs in both quarters include,
- Syria – 9.5 drive-by URLs for every 1,000 URLs
- Latvia – 6.6
- Belarus – 5.6.
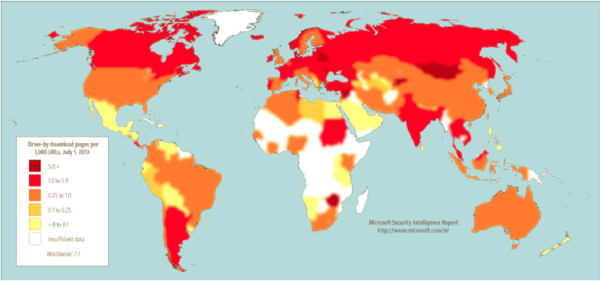
The Drive-by Download concentrations were tracked by Bing at the end of the second quarter of 2013. Accordingly, the measures taken by the search engine to help protect users from drive-by download attacks include analysis of websites for exploits when indexing them and displaying warning messages when listings for drive-by download pages appear in the list of search results.
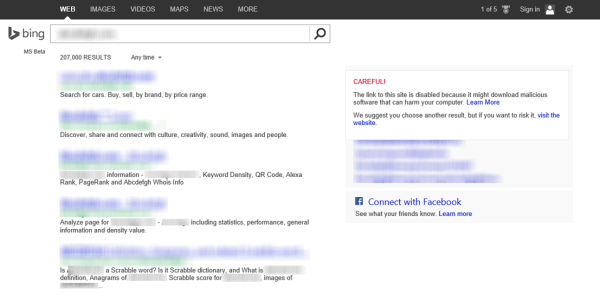
Prevent Drive-by download attacks
A TechNet article features steps for developers and IT Professionals to be taken for managing the risk related to drive-by download attacks. Some of the measures include:
Preventing web servers from being compromised. Web servers can be compromised if they are not kept updated with the latest security updates. So,
- Keep the server’s operating system(s) up to date
- Software installed on these web servers up to date
- Check out SDL Quick Security Reference Guides for the latest updates
- Avoid browsing the Internet from web servers or using them to open email and email attachments.
- Register your site with Bing webmaster tools and Google Webmaster, so that search engines can proactively inform you if they detect something bad on your site.
As a user, you can take the following precautions:
- Make sure your Windows operating system and web browser is fully up-to-date.
- Use a good security software and again ensure that it has the latest definitions always
- Use minimum browser addons as they often get compromised
- Using a URL Scanner addons for your browser might also be an option you may want to consider
- If you are using Internet Explorer make sure your SmartScreen is turned on.
- And finally, develop a habit of safe browsing and be selective about which sites you browse regularly.
Do let us know if your computer has ever been infected with a drive-by download attack.
Now read: What is Malvertising?
And if you use Firefox, install “NoScript”.
It´s an addon that lets you allow javascript only on selected webbsites, and block them on all other sites.
Nice tip. Thanks.
This is actually one of the best articles I’ve read on this site in a long time. THANK YOU, Anand.
And, actually, that’s probably unfair. There are TONS of excellent articles, here. But this one is really good. It explains the problem, and gives EXCELLENT advice regarding what to do about it for both the website owner, and the end-user. Granted, it’s a little bit Microsoft-centric, but then, again, so it this website, so no surprise (nor is that a bad thing).
For me, it’s:
1) Having a hardware firewall. At one of my locations, it’s the firewall that’s built-in to the combination DSL modem, router/switch and WI-FI device (commonly called a “gateway,” even though that’s not really technically entirely accurate); and at my other location it’s a DSL modem with separate router/switch, and an older roughly equivalent of this device…
SEE | http://dell.to/1eCEuFs (Sonicwall TZ 205 firewall appliance)
…from back before when Dell acquired Sonicwall; and which has no wireless capability. A customer traded-up, so I kept (and have been for years using his old one). I’ve been recommending and using Sonicwall stuff for years and years, and was none-too-happy when Dell absconded with it; but that’s a rant for another day. The products are still best-of-breed… though more expensive than they used to be. Consumer-grade end-users are probably priced-out of most Sonicwall products, but there are many excellent hardware firewall appliances out there, some of them well below $100(US). And as long as the firewall that’s built right into the DSL or cable modem “gateway” (I hate that technical misuse of the term) has the right basic firewall features (and most of today’s do), then it’s good enough. Of course, one should still use a software firewall, which I get into further down herein.
2) Configuring my routers to use OpenDNS instead of the DNS service that my Internet Service Provider (ISP) includes. I use AT&T DSL at both locations, and so AT&T’s normal DNS service automatically comes with it, just as every ISP offers its own DNS. However, by bypassing that, and using OpenDNS instead, I can configure things so that most bad websites can’t even be accessed; and those that can have most of their bad stuff blocked. It’s also a great way to keep the kids (in my case, grandkids) off the porn, etc. OpenDNS’s anti-phishing protection, too, is best-of-breed.
3) Using SR Ware’s “Iron” (portable, in my case; though it matters not whether one uses the installed or the portable Iron) browser… a Chromium-based Google Chrome look-and-act-alike, but with all of Chrome’s Google-snooping privacy problems removed. Iron also allows for the use of all Chrome plug-ins/extensions, exactly the same as Chrome (in fact, it still allows extensions not from the Chrome Store to be installed, where Chrome is now blocking that) which include some extentions that further help to block both access to bad websites, as well as provide mitigation of what they can do. Admittedly, Internet Explorer (IE) has scored better than Chrome in some malware-blocking tests; but not once certain free extensions are installed into Chrome (or, in my case, Iron… same difference, for our purposes, here). IE users also often complain that in order for IE to so effectively block, it can sometimes over-block — that it is, in other words, overly-zealous — which can make it a real pain to use. My copy of Iron is as locked-down as it needs to be in order to be just about the safest browser out there. One may do the same thing to Chrome, though, as long as one’s willing to live with Google’s inherent privacy violations that are in Chrome. There’s also COMODO DRAGON, which is yet another Chromium-based Chrome look-and-act-alike, which also removes most or all of the inherent Google privacy violations in Chrome; plus adds even more built-in capabilty to block things (though none which can’t be replicated in Iron or Chrome with the right extensions added).
4) Using the following extensions in the either Chrome or Chrome look-and-act-alike browser:
* Adblock-Plus, with the “EasyList” and the “EasyPrivacy” and the “Malware Domains” lists running in it; plus a few custom filters of my own.
* Ghostery (with pretty much everything blocked at first; and then carefully unblocking either by-site, or globally — usually globally, so I don’t have to keep doing it — only the things I want: it can take a little while to finally get it just perfect). I once tested Ghostery against its competitors (like Abine’s DO-NOT-TRACK-ME, for example; and others), head-to-head, and found Ghostery to be the single most effective tool of its type, so I’ve now just settled-on it to keep the number of extensions down to just what’s needed).
* McAfee Site Advisor | Uses McAfee’s monster database of website malware scan results to mark with either a green (for “the site’s safe”), or yellow (for “exercise caution”) or red (for “beware of” or “don’t visit”) little ball all Google search results, as well as all links in Facebook (and on a few other sites, too). It will also literally block access to yellor or red sites (with a link to allow you to ignore the warning and visit the site anyway if one wishes). It’s far, far better than WOT because WOT is crowd-sourced, and so is just a big popularity contest; and by so being can also be (and often is) gamed. McAfee Site Advisor, on the other hand, relies solely on McAfee’s own anti-malware servers’ scanning of websites for malware; and they have scanned virtually every website on the planet. There are very few gray-colored balls next to Google search results (meaning that McAfee has not yet scanned the site); and in recent years, the number of false positives has dropped to near zero (it used to be quite a problem). I would not run a browser without McAfee Site Advisor installed into it; and it’ll install into Chrome (and it’s Chromium-based cousins), Firefox, and IE. Even only the free version is good enough.
* The ScriptBlock extension which blocks, of course, scripts (and scripts are the number one means by which drive-by malware downloading occurs; and the malware is executed). Sadly, ScriptBlock blocks too much at first, and so needs to have its settings reigned-in; but once it’s just-right, it’s amazing. There are several other extensions which do what it does; at least one of which does at least a few things better, but its downside tradeoffs are not worth it to me. All things considered, the ScriptBlock extension seems to be the best of all worlds; but ya’ gotta’ get it just so, or it’ll block too much and drive ya’ nuts when ya’ hit a favorite website. Takes a little time to test and configure.
* Privacy Manager | Doesn’t really block anything, but it helps to keep things clean (or at least to quickly access the parts of the browser where cleaning can happen) so that malwarish stuff that happens to make it into the browser’s cookies cache, for example, or any other store or cache will not survive browser closure.
* The Click&Clean and History Eraser extensions/apps are SERIOUS browser cache, store and history cleaners with high configurability. If History Eraser had Click&Clean’s “Securely Close Browser” feature, I’d have only History Eraser, and not also Click&Clean in my browser since the only part of Click&Clean that I use is the “Securely Close Browser” feature. Of course, all I’d have to do is run History Eraser before browser closure, and it would be the same thing; but I’m lazy and want it all to happen in one click. I could also always launch the browser using a batch file, which batch file runs the History Eraser app after browser closure, but I’ve yet to sit down and actually do it. The point is, though, that I want everything cleaned after browser use in part so that the browser is peppy when next launched, and in part so that nothing bad which somehow made it into cache or history or any stores in one browser session will still be there in the next.
* The HTTPS Everywhere extensions ensures that any site which can be used with SSL (https://) will be so used, thereby ensuring that all data exchanged between the browser and the website is encrypted; which further ensures that said data cannot be “sidejacked” by someone who’s sharing the same public WI-FI (in a coffee shop, for example) that I’m using.
* Cache Killer to kill anything that makes it into the browser’s cache in real time (rather than waiting until something like Click&Clean and/or History Eraser is used). This will keep any malware which lands in the cache effectively out of it before it can do anything. Of course, nothing stops that sort of thing like a Hosts Intrusion Protection System (HIPS) utility, which I cover further down, herein. Most of the time, though, I keep Cache Killer turned-off; and only use it if there’s an actual need.
* There’s also the “Disconnect” extension, which LifeHacker liked best of all for what at least a few of the above-listed extensions do, all wrapped-up in one extension. However, in my head-to-head testing of it against the killer combination of my above-listed extensions, it wasn’t as effective. I have it installed, but de-activated. I keep thinking I’ll just remove it, but I sometimes like to test it and see if it has improved. It hasn’t.
5) Use of the freeware version of “Spyware Blaster” by Brightfort which sorta’ kinda’ “innoculates” the registry against its list of known bad stuff. The freeware version won’t auto-update, so ya’ gotta’ do it manually about twice a month (or so it is my recommendation).
6) Use the freeware version of “SuperAntiSpyware,” which has become, despite its incredibly stupid name, probably the best-of-breed of its particular type of anti-malware tool. Though the freeware version will allow a system tray (notification area) icon to protect against browser hijacking, said icon in the freeware version does not also have realtime protection (that’s only in the paid version), nor paid-version-only scheduled scanning. The freeware version does everything else it needs to, though… and more. Just manually whole-system scan once a week and it’ll be fine.
7) use the freeware version of “Malware Bytes,” which sorta’ kinda’ does what SuperAntiSpyware does, but which has superior “zero day” protection. “Zero day” means malware that’s so new its “signature” has not yet been put into any anti-malware signature database; and so sophisticate heuristics are required to detect stuff that only “looks” like it could be bad (and which probably is), but which can’t be confirmed as bad by its signature being in the anti-malware software’s malware signature database. The Malware Bytes folks, for whatever reason, have some of the best heuristics in the world of that kind of software. The freeware version has no realtime protection or schedule scanning, and so a weekly manual whole system scan is the best bed. Do SuperAntiSpyware one night while you sleep, and Malware Bytes the next night while you sleep, and then…
8) Use the free COMODO INTERNET SECURITY (CIS) which includes pretty-darned-good, now (after a few years of not-so-good) anti–virus; still-not-that-great anti-spyware; pretty-okay anti-rootkit; excellent HIPS, and a best-of-breed (among freeware anti-malware suites) software firewall. Its firewall, in fact, routinely scores right up there with the commercial Kaspersky firewall in independent firewall tests. CIS’s firewall and HIPS are so good that they’re worth using even if one wants to rely on other tools for anti-virus, anti-spyware, and anti-rootkit. It’s a little bit of a geek’s tool in terms of its tendency to pop-up warnings that only geeks tend to understand; but COMODO has done a good job of minimiziing that problem in recent years. There’s truly no other entirely-free anti-malware suite that’s better out there. There are, though, some that are just as good, and that are friendlier to non-technical end-users. I love CIS, though, and would consider nothing else. And its firewall — especially when coupled with the earlier-mentioned hardware firewall appliance, and all that’s herein listed; but even only on its own — lets virtually *NOTHING* bad through
9) Use of a HOSTS file, managed by the freeware “HostsMan” to auto-download and keep up-to-date the preconfigured HOSTS files out there by such as MVPS Hosts, hpHosts, Peter Lowes Adservers, and others. All known badware sites are already in such preconfigured HOSTS files (in fact, too much is blocked; and so one ends-up, over time, adding websites to the HostsMan exclusion list… mine’s gotten pretty long, after all these years; and so, like some of the other tools, here, a bit of tweaking, over time, is necessary to get things just right). HostsMan’s companion “HostsServer” tool sits down in the system tray (notification area) as a mini web server, and serves-up a one-pixel-sized transparent .GIF file whenever a web page or ad or anything blocked in the HOSTS file is called-for on a website; and if said site uses modern DIV and CSS technology for page layout, spaces on the page normally occupied by ads just collapse down to nothing and disappear; and if older fixed-sized boxes are used for ads, then they’re just blank (as opposed to displaying an error because the site can’t be found, as would happen were it not for HostsServer and its little one-pixel transparent .GIF.
–
These nine things combine in my home and at my office to provide a completely free (except, of course, for the hardware firewall appliance; but there’s already a pretty good one of those in most people’s DSL or cable modem “gateways”) set of tools that I think of as my pseudo-suite that becomes a fortress of protection around my machine; and, trust me, NOTHING bad is getting through. When I run either SuperAntiSpyware or Malware Bytes (both versions of which are paid, but, again, it wouldn’t matter if they were the freeware ones) they find almost nothing anymore. CIS never finds anything, either. It’s very satisfying.
Plus, because of Adblocker-Plus and the HOSTS file, I see almost no advertising on any website… ever. I only intentionally allow ads on sites like this one, that I like, so that if any payment to this site is based on hits, the revenue can be earned. But for the most part, I never see ads anymore. Period.
Sites known to contain drive-by downloads are blocked by both the HOSTS file, and OpenDNS; and I’m warned off any that aren’t by McAfee Site Advisor. Seriously: Nothing gets through. Nothing. And it’s all free… or at least could be, for you; I happen to pay for, again, SuperAntiSpyware and Malware Bytes (both of which have old lifetime licenses, so they were just one-time payments; SuperAntiSpyware no longer does that, and Malware Bytes has announced that it soon won’t, either).
That, in any case, is how I do it. Your mileage may vary.
__________________________________
Gregg L. DesElms
Napa, California USA
gregg at greggdeselms dot com
Veritas nihil veretur nisi abscondi.
Veritas nimium altercando amittitur.
Thanks for the kind words, Gregg. And thanks for your amazing list of additional inputs too.